Overview
The article delineates ten best practices for effective threat detection and response in cybersecurity, underscoring the necessity of continuous monitoring, incident response planning, and the integration of advanced technologies such as AI. Evidence supports that organizations implementing these practices can markedly enhance their security posture, diminish incident response times, and more effectively safeguard sensitive data against the ever-evolving landscape of cyber threats.
Introduction
In an era where cyber threats are increasingly sophisticated and pervasive, organizations face mounting pressure to bolster their defenses. This article explores ten essential best practices for threat detection and response, providing invaluable insights that can significantly enhance an organization's cybersecurity posture. As businesses implement these practices, they must confront the challenge of keeping pace with evolving threats and ensuring that their strategies remain effective. What critical steps can organizations take to not only detect but also swiftly respond to potential breaches in this dynamic landscape?
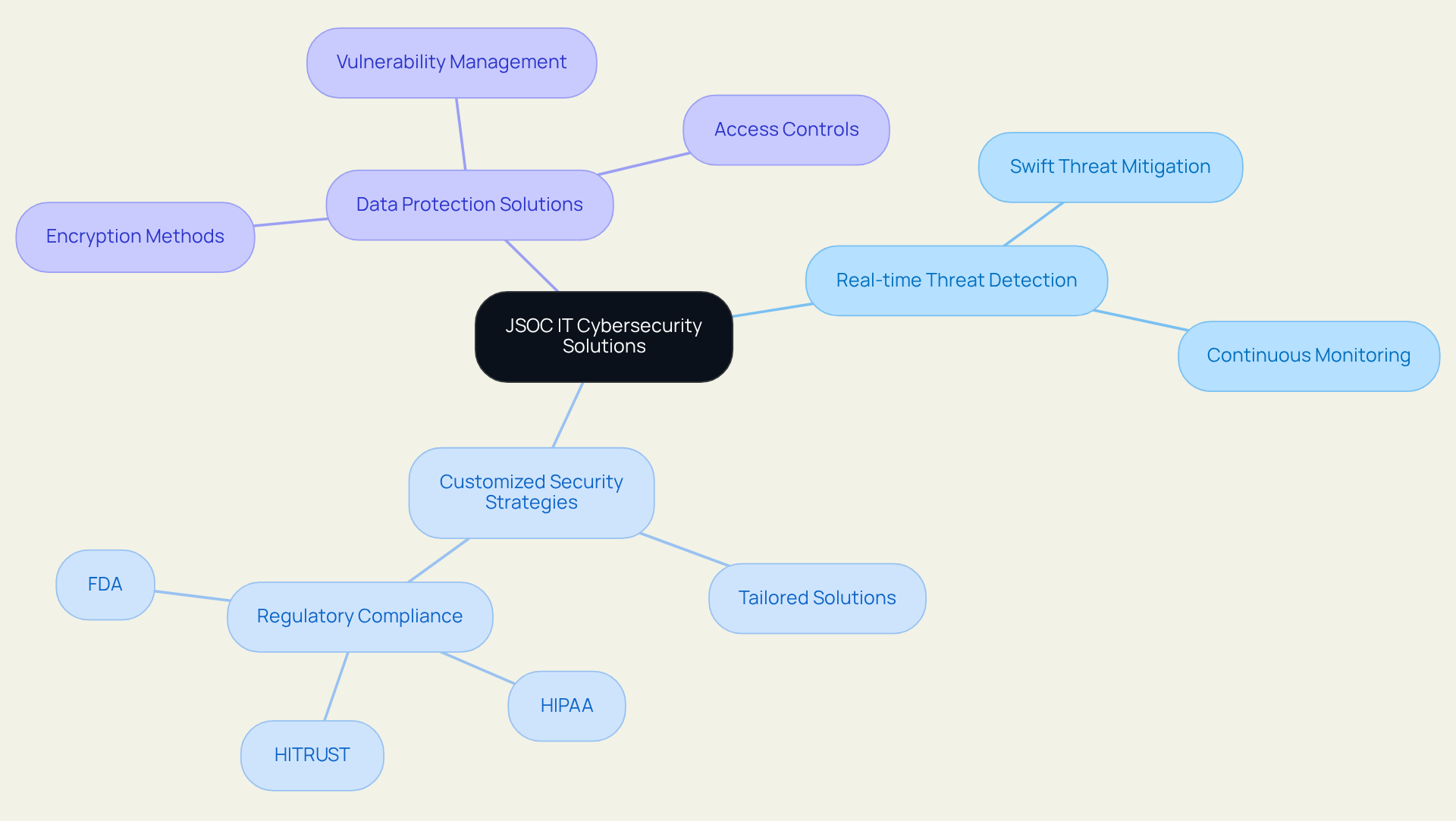
JSOC IT: Integrated Cybersecurity Solutions for Effective Threat Detection and Response
JSOC IT employs a 'Post-Security' model that integrates IT operations, protective measures, and compliance into a cohesive framework. This strategy dismantles silos, fostering seamless collaboration within client teams. By merging their services, JSOC IT enhances the protective posture of organizations, enabling them to expand confidently while being fortified against breaches and vulnerabilities. This integrated model proves particularly effective in sectors such as financial services and healthcare, where with standards like HIPAA, HITRUST, and FDA are paramount.
Key features include:
- Real-time threat detection and response: Continuous monitoring guarantees that threats are swiftly identified and mitigated, protecting sensitive patient data.
- Customized security strategies: Tailored solutions address specific industry needs and regulatory mandates, ensuring compliance with SEC, FINRA, and global data privacy standards.
- Data protection solutions: Employing encryption and access controls to secure sensitive information, complemented by robust vulnerability and patch management policies.
Implement Continuous Monitoring to Detect Threats in Real-Time
Establishing ongoing observation is essential for entities aiming to implement best practices for threat detection and response to protect their networks against cyber risks. This practice employs advanced tools and technologies to monitor network activity around the clock, empowering organizations to:
- Identify anomalies: Through the analysis of user behavior and system logs, organizations can pinpoint unusual activities that may signal a breach. For example, machine learning algorithms have demonstrated an impressive ability to identify over 98% of phishing attempts, which exemplifies best practices for threat detection and response, significantly bolstering threat detection capabilities.
- Respond promptly: Immediate alerts enable response teams to act swiftly, mitigating potential damage from cyber incidents. Organizations leveraging Managed Detection and Response (MDR) services are applying best practices for threat detection and response, resulting in a remarkable 62% reduction in security incidents annually, which underscores the effectiveness of timely responses.
- Utilize automated tools: Solutions such as Security Information and Event Management (SIEM) systems aggregate and analyze data from diverse sources, enhancing risk visibility. Notably, the average response time for MDR services is approximately three hours, compared to sixty-six hours for internal teams, illustrating the efficiency of automated systems in managing risks.
Current trends indicate that by 2025, 50% of entities will adopt MDR services for monitoring, detection, and response functions, aligning with best practices for threat detection and response, marking a significant shift towards proactive cybersecurity measures. As organizations face increasing complexities in cyber risks, the integration of real-time detection tools is vital for maintaining robust security postures and adhering to best practices for threat detection and response.

Create and Update an Incident Response Plan for Swift Threat Mitigation
A robust incident response plan is essential for effective threat mitigation and should encompass the following key components:
- Preparation: Establish a dedicated incident response team (IRT) with clearly defined roles and responsibilities. This team should include such as Incident Response Managers, Security Analysts, IT Support, Legal Advisors, and Public Relations personnel to ensure a coordinated response. JSOC IT highlights the significance of a proactive strategy, ensuring that organizations are prepared with the essential tools and knowledge to manage occurrences efficiently.
- Detection and Analysis: Implement comprehensive processes for identifying and assessing incidents as they occur. This includes utilizing advanced risk detection tools and maintaining centralized logging to monitor unusual network activity effectively. JSOC IT's dedication to ongoing surveillance and enhanced protective measures guarantees that possible risks are recognized quickly, enabling prompt action.
- Containment, Eradication, and Recovery: Outline specific steps for containing threats, eradicating malicious elements, and restoring normal operations. Immediate containment actions may involve disconnecting affected systems and applying firewall rules, while long-term strategies should focus on patching vulnerabilities and enhancing security measures. JSOC IT's integrated cybersecurity solutions provide tailored protection that aligns with industry-specific needs, ensuring robust recovery processes.
- Post-Event Review: Regularly carry out post-event assessments to evaluate the response to previous events. This practice is essential for recognizing shortcomings in the response process and enhancing future readiness. Cybersecurity experts stress that entities that adopt modifications based on these assessments can lower future occurrence rates by as much as 50%. Continuous training and regular tabletop exercises are also vital for keeping the IRT prepared for real-world attacks. JSOC IT's emphasis on compliance and customized solutions guarantees that entities not only meet regulatory requirements but also improve their overall security stance.
By adhering to these best practices, organizations can enhance their incident response capabilities, minimize damage during cyber incidents, and maintain compliance with regulatory requirements such as GDPR and CCPA.

Utilize Threat Intelligence for Proactive Threat Detection
Effectively utilizing threat intelligence requires several key practices:
- Collecting Data: Organizations must gather comprehensive information on emerging threats, vulnerabilities, and attack vectors from diverse sources, including threat feeds, industry reports, and internal logs. This data forms the foundation for informed decision-making. JSOC IT enhances this process with robust network security features, including restricted port configurations and endpoint security, ensuring that data collection is both secure and comprehensive.
- Analyzing Trends: By analyzing the collected data, organizations can identify patterns and predict potential threats that may impact their operations. This proactive approach enables teams to stay ahead of adversaries and mitigate risks before they materialize. Recent trends indicate a notable increase in advanced attacks, with credential harvesting being the most frequent effect noted in occurrences, happening in 28% of cases in 2024. JSOC IT's comprehensive cybersecurity framework supports this analysis by integrating essential controls for enhancing network protection and access management.
- Incorporating Intelligence into Protective Operations: Ensuring that risk intelligence guides protective strategies and response plans is essential. This integration facilitates a proactive defense, allowing organizations to respond promptly to recognized risks. Organizations that have effectively integrated risk intelligence into their protective frameworks are utilizing best practices for threat detection and response, leading to improved incident response times and an enhanced overall defense posture. As noted by industry experts, adapting strategies to counter AI-powered cyber-attacks is crucial for maintaining security. JSOC IT equips companies with integrated cybersecurity solutions that scale securely, offering customized support and proactive risk management.
Industry leaders emphasize the significance of adopting best practices for threat detection and response in risk detection. As cyber threats continue to evolve, incorporating risk intelligence into security operations is imperative for sustaining resilience against new challenges. To begin applying these practices, entities should prioritize , ensuring they remain informed and prepared. With JSOC IT's commitment to client success and exceptional service, businesses can focus on growth initiatives while feeling secure in their cybersecurity posture.

Promote Security Awareness Training Among Employees
Encouraging awareness training among employees is essential for protecting organizations from phishing and social engineering attacks. Effective training must encompass several key areas:
- Recognizing Phishing Attempts: Employees must be equipped to identify suspicious emails and links. Training should emphasize , such as urgent language, unexpected attachments, and poor grammar. Implementing a 'Phishing Red Flags Checklist' and conducting regular reviews of real-world examples can significantly enhance recognition skills. Notably, over 80% of data breaches involve human factors, underscoring the critical importance of employee awareness in preventing phishing attacks.
- Understanding Social Engineering: Staff should be educated on the tactics attackers use to manipulate individuals into revealing confidential information. This includes recognizing psychological tricks and the importance of verifying requests for sensitive data.
The guidelines on password management, secure data handling, and reporting suspicious activities are examples of best practices for threat detection and response. Employees should be trained to use strong, unique passwords and to employ multi-factor authentication wherever possible.
- Current Trends in Phishing Attack Recognition Training: As phishing attacks evolve, training must adapt. Organizations are increasingly shifting towards micro-training sessions that are brief and engaging, such as 5-minute videos and interactive quizzes, to maintain employee interest and retention. This shift represents a wider trend of transitioning from compliance-centered training to more engaging, expert-supported training that tackles genuine challenges.
- Examples of Successful Training Initiatives: Organizations that have implemented simulated phishing tests have seen significant reductions in click rates on phishing emails. For instance, a retailer in Northeast Louisiana achieved a 70% decrease in click rates after three months of simulations, demonstrating the effectiveness of hands-on training methods. As Grant Ho, Assistant Professor at the University of Chicago, observes, traditional training methods often fail to deliver valuable knowledge in protection, emphasizing the need for innovative approaches.
By fostering a culture of vigilance and continuous learning, entities can significantly enhance their defenses against phishing and social engineering threats.

Conduct Regular Vulnerability Assessments to Strengthen Security Posture
Performing regular vulnerability evaluations is essential for enhancing a company's security posture, particularly in the healthcare sector where safeguarding patient information is paramount. This process should encompass several key practices:
- Regular Scanning: Automated tools are indispensable for continuously identifying vulnerabilities in systems and applications. Given the proliferation of connected devices and cloud services, companies are increasingly adopting automated scanning solutions to ensure constant vigilance. Recent trends indicate that 24% of entities now conduct vulnerability assessments more than four times a year, reflecting a growing recognition of the necessity for frequent evaluations to stay ahead of emerging threats. Compliance with standards such as HIPAA, HITRUST, and FDA is critical in this context, as it ensures that sensitive medical data is adequately protected.
- Manual Testing: While automated tools are effective, they should be complemented by manual penetration testing. This method simulates real-world attacks, enabling entities to uncover potential vulnerabilities that automated scans might overlook. Ongoing penetration testing has become a strategic necessity, allowing entities to proactively identify vulnerabilities that scheduled compliance checks may miss. This is particularly crucial for healthcare organizations that must adhere to stringent regulatory requirements.
- Prioritization of Findings: Once vulnerabilities are identified, it is imperative to assess their severity and prioritize remediation efforts based on risk. A risk-based prioritization model aids entities in focusing on the most critical vulnerabilities that could impact operations. This organized approach not only enhances protection but also ensures that resources are allocated efficiently, aligning with compliance mandates.
Organizations that have successfully implemented best practices for threat detection and response exemplify the effectiveness of a comprehensive vulnerability management strategy. For instance, a healthcare organization that engaged ethical hackers for vulnerability scans uncovered misconfigurations that standard scans failed to detect, significantly bolstering their security posture. This underscores the increasing need for in the industry, as ongoing oversight is vital to adapt to evolving risks and maintain compliance with industry regulations.
As cybersecurity challenges continue to evolve, the integration of automated scanning and manual testing is increasingly vital in following best practices for threat detection and response. Cybersecurity professionals assert that prioritizing vulnerability remediation is essential for sustaining robust defenses against sophisticated attacks. By embedding these practices into their security culture, organizations can better protect sensitive data and ensure compliance with HIPAA, HITRUST, and FDA standards. Furthermore, integrating cybersecurity solutions, including embedded SOC and GRC operations, enhances continuous protection and aligns with comprehensive strategies to safeguard patient data.

Automate Threat Response Processes for Enhanced Efficiency
Automating danger response is essential for enhancing efficiency in cybersecurity operations by following best practices for threat detection and response. Key strategies include:
- Implementing SOAR solutions: Security Orchestration, Automation, and Response (SOAR) tools significantly enhance incident management by automating repetitive tasks. These platforms streamline workflows, allowing security teams to concentrate on critical threats while following best practices for threat detection and response instead of becoming bogged down by low-value activities. Entities employing SOAR have noted a decrease in response times by as much as 80%, which demonstrates the best practices for threat detection and response through the efficiency of automation in practical situations.
- Developing predefined response playbooks is crucial for standardizing actions during specific types of incidents, as it aligns with the best practices for threat detection and response. These playbooks outline the best practices for threat detection and response, guiding teams through the necessary steps to ensure a swift and coordinated response. By automating these workflows, organizations can adopt best practices for threat detection and response, which helps minimize human error and enhance decision-making during volatile situations.
- To maximize the benefits of automation, it is vital that SOAR tools integrate seamlessly with current protection infrastructures, following the best practices for threat detection and response. This integration not only improves overall efficiency but also aligns with best practices for threat detection and response by offering a , facilitating faster detection and resolution of issues. Organizations that have effectively incorporated SOAR solutions report enhanced awareness of their protective stance and quicker recovery from events, following best practices for threat detection and response.
- Current trends indicate that the adoption of SOAR solutions is on the rise, with many organizations recognizing their value in aligning with best practices for threat detection and response amid the complex cybersecurity landscape of 2025. As automated event management becomes increasingly essential, the emphasis on merging these solutions with current systems will be crucial for attaining operational resilience and sustaining strong security frameworks.

Establish Clear Communication Protocols for Incident Management
Effective communication protocols are paramount for successful event management in cybersecurity. Clearly delineating roles is essential; this ensures that the right information reaches the appropriate stakeholders promptly, minimizing confusion and enhancing response efficiency. Designating a Communication Lead is critical for maintaining precise event documentation and ensuring timely updates.
Utilizing allows for secure sharing of updates and information. This practice prevents misinformation and ensures that all communications are centralized and easily accessible. Continuous monitoring, as outlined in the Secure Development Policy, supports these channels by guaranteeing that information remains accurate and current.
Transparency is maintained through regular updates during the event response process. Consistent communication fosters trust among stakeholders and ensures that everyone is informed about the status and impacts of the event. It is advisable to inform stakeholders every 30 minutes to an hour during major events, in accordance with best practices for threat detection and response from the Incident Response Plan.
Organizations that adopt the best practices for threat detection and response have observed significant enhancements in their event management capabilities. For instance, companies that conduct regular training and simulations report a 35% quicker reaction to events. Furthermore, a well-defined communication strategy can reduce breach containment times by up to 33%, underscoring the importance of proactive communication. Additionally, incorporating robust policies like the Vulnerability and Patch Management Policy and the Risk Assessment and Treatment Policy bolsters overall cybersecurity posture and response effectiveness.
Cybersecurity experts emphasize that clear communication during events is not merely advantageous but essential. As one expert noted, "When you communicate clearly, people know what to expect," reinforcing the notion that effective communication can mitigate the negative impacts of incidents and cultivate a culture of trust and collaboration within organizations.

Leverage AI and Machine Learning for Advanced Threat Detection
Utilizing AI and machine learning is essential for advanced danger detection in today’s cybersecurity landscape. Key practices include:
- Behavioral Analysis: Implement systems that learn normal user behavior patterns, enabling the detection of deviations that may signal potential threats. This method is crucial, as insider risks often imitate genuine activities, making them difficult to recognize without advanced monitoring. Ensuring confidentiality through restricted access to customer data enhances the effectiveness of behavioral analysis by limiting exposure to sensitive information.
- Automated Risk Detection: Employ AI-driven tools to proactively identify potential dangers across the network. Organizations are increasingly adopting these technologies as part of their best practices for threat detection and response, achieving significant success in detecting vulnerabilities before they can be exploited. When coupled with a robust , these tools can greatly mitigate risks associated with unaddressed vulnerabilities.
- Continuous Learning: Ensure that AI systems are regularly updated with new data to refine their detection capabilities over time. This continuous adjustment is vital, as cyber threats evolve rapidly, necessitating systems that can learn from emerging patterns and anomalies. Implementing a data retention and disposal policy further supports this continuous learning process by ensuring that only relevant data is utilized for training AI models.
Current trends indicate that entities employing AI for proactive risk detection are experiencing marked improvements in their security protocols. Industry leaders assert that a robust behavioral analysis framework is essential for sustaining a resilient cybersecurity strategy and aligns with the best practices for threat detection and response. As cybercriminals increasingly exploit sophisticated techniques, the integration of AI and machine learning into danger detection processes, supported by comprehensive cybersecurity controls, will be a defining factor in effective cybersecurity management.

Continuously Review and Improve Threat Detection Strategies
To maintain and enhance the effectiveness of threat detection strategies, organizations must prioritize the following best practices:
- Conduct Regular Audits: Systematic reviews of existing threat detection strategies are essential. Regular audits evaluate performance against evolving risks, ensuring that the best practices for threat detection and response are applied to keep protective measures robust and efficient. These audits provide critical insights that can lead to measurable improvements in protection stance, aligning with the principles outlined in the Secure Development Policy.
Incorporating feedback by utilizing insights from incidents and risk intelligence represents best practices for threat detection and response. Organizations should establish systems to integrate feedback from safety occurrences into their practices, enabling adaptive responses to emerging challenges. This includes employing incident response plans and insights gained to inform future strategies, ensuring readiness for similar incidents in the future, as emphasized in the Business Continuity and Disaster Recovery Plan.
- Stay Informed: Keeping abreast of the latest cybersecurity trends and technologies is crucial for enhancing detection capabilities. The rapid evolution of threats demands a proactive security approach. Continuous education and awareness of current trends empower organizations to adopt advanced detection technologies that effectively identify and mitigate risks.
By implementing these practices, organizations can significantly strengthen their defenses against the dynamic threat landscape, ensuring preparedness to respond to incidents swiftly and effectively. Furthermore, integrating comprehensive cybersecurity policies can enhance organizational resilience.

Conclusion
The integration of best practices for threat detection and response is crucial for organizations aiming to protect their digital environments. By embracing a proactive strategy that includes:
- Continuous monitoring
- Incident response planning
- The use of threat intelligence
Businesses can significantly bolster their cybersecurity posture. The focus on collaboration, automation, and employee training further fortifies defenses against the ever-evolving landscape of cyber threats.
Key insights underscore the necessity of:
- Real-time threat detection
- A well-structured incident response plan
- Regular vulnerability assessments to identify potential weaknesses
Moreover, cultivating a culture of security awareness among employees and harnessing advanced technologies such as AI and machine learning are essential for outpacing cybercriminals. Organizations that prioritize these strategies not only mitigate their risk exposure but also ensure compliance with industry regulations.
Ultimately, the cybersecurity landscape is in constant flux, making it imperative for businesses to remain vigilant and adaptable. By committing to continuous improvement and routinely reviewing threat detection strategies, organizations can build resilience against cyber threats. Embracing these best practices empowers entities to protect sensitive data and maintain operational integrity in an increasingly complex digital world.
Frequently Asked Questions
What is the 'Post-Security' model employed by JSOC IT?
The 'Post-Security' model integrates IT operations, protective measures, and compliance into a cohesive framework, fostering collaboration within client teams and enhancing organizational protection against breaches and vulnerabilities.
Which sectors benefit most from JSOC IT's integrated cybersecurity solutions?
Sectors such as financial services and healthcare benefit significantly, as safeguarding sensitive data and compliance with standards like HIPAA, HITRUST, and FDA are crucial.
What are the key features of JSOC IT's cybersecurity solutions?
Key features include real-time threat detection and response, customized security strategies tailored to specific industry needs, and data protection solutions that employ encryption and access controls.
How does continuous monitoring enhance threat detection?
Continuous monitoring allows organizations to identify anomalies in network activity, respond promptly to potential breaches, and utilize automated tools like SIEM systems for enhanced risk visibility.
What impact do Managed Detection and Response (MDR) services have on security incidents?
Organizations using MDR services have seen a 62% reduction in security incidents annually due to immediate alerts and swift responses to cyber threats.
What components should an effective incident response plan include?
An effective incident response plan should include preparation with a dedicated incident response team, detection and analysis processes, containment and eradication strategies, and post-event reviews.
Why is preparation important in an incident response plan?
Preparation is crucial as it ensures that organizations have a dedicated team with defined roles and responsibilities, enabling efficient management of incidents when they occur.
How can organizations enhance their incident response capabilities post-event?
Organizations can enhance their capabilities by conducting regular post-event assessments, implementing continuous training, and performing tabletop exercises to improve readiness for future incidents.
What regulatory compliance standards are mentioned in relation to cybersecurity?
Regulatory compliance standards mentioned include GDPR, CCPA, HIPAA, HITRUST, SEC, and FINRA.