Overview
The article delineates four best practices for compliance advisory in cybersecurity, asserting the critical need for:
- Understanding regulatory requirements
- Assessing the current cybersecurity posture
- Selecting a tailored compliance framework
- Implementing continuous monitoring strategies
Each practice is substantiated by pertinent examples and statistics, underscoring the necessity for stringent measures under GDPR and HIPAA. These elements collectively illuminate the pivotal role of compliance in bolstering security and mitigating risks within an ever-evolving threat landscape.
Introduction
Navigating the intricate landscape of cybersecurity compliance presents a pressing challenge for organizations today, particularly as regulations evolve and become increasingly stringent. With the stakes at an all-time high, a deep understanding of frameworks such as GDPR, HIPAA, and PCI DSS is essential for safeguarding sensitive data and avoiding costly penalties.
What strategies can organizations implement to ensure they not only meet compliance requirements but also enhance their overall cybersecurity posture? This article explores four best practices for compliance advisory in cybersecurity, offering valuable insights that empower organizations to thrive amidst regulatory complexities and emerging threats.
Understand Regulatory Requirements for Cybersecurity Compliance
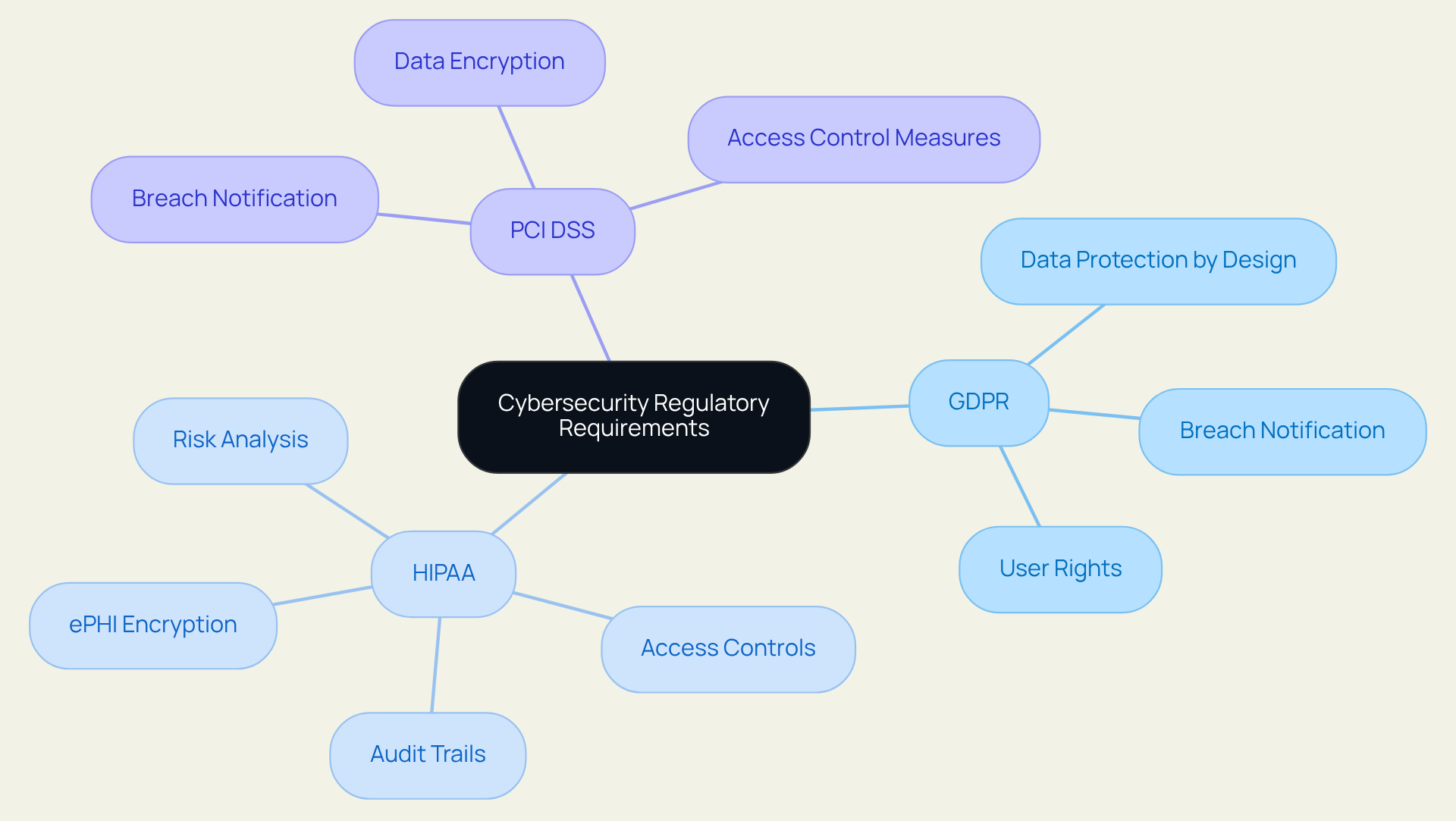
Organizations must possess a comprehensive understanding of the regulatory landscape governing their operations, particularly regarding and data protection. Key regulations such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS) impose specific requirements regarding data handling, breach notification, and risk management.
For instance, GDPR mandates that entities implement a 'data protection by design and by default' approach, ensuring that privacy measures are integrated into their systems from the outset. Conversely, HIPAA emphasizes the necessity of stringent access controls and thorough audit trails for patient information, with statistics indicating that over 168 million records were compromised in 2023 alone. This stark reality highlights the urgent need for healthcare entities to fortify their cybersecurity frameworks in response to evolving threats.
Moreover, the imminent changes to HIPAA regulations in 2025 will introduce new adherence requirements, including enhanced encryption standards and multi-factor authentication, critical for safeguarding electronic protected health information (ePHI). As cybersecurity specialist Steve Alder aptly notes, 'Maintaining adaptability and reliability will be more crucial than ever' as entities navigate these regulatory shifts. Organizations can significantly mitigate the risk of non-compliance penalties and enhance their overall safety posture by utilizing a compliance advisory for cybersecurity that aligns their strategies with these compliance requirements.
Assess Your Current Cybersecurity Posture
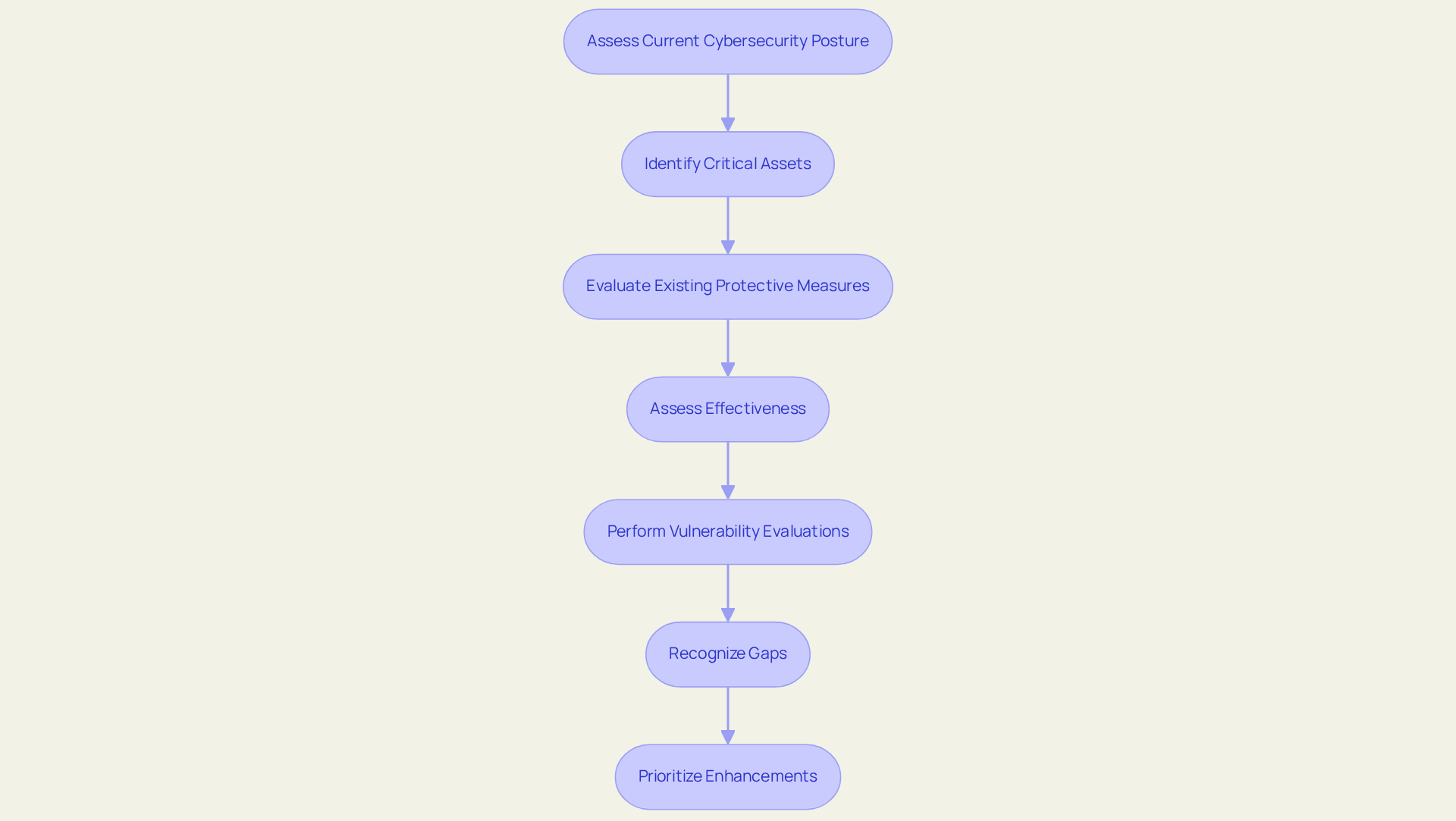
Conducting a comprehensive evaluation of your current cybersecurity status is essential. This process involves assessing existing protective measures, policies, and incident response capabilities. Organizations must leverage frameworks such as the NIST Cybersecurity Framework or ISO 27001 to guide their assessment effectively. Start by identifying critical assets, then assess the effectiveness of current protective measures, followed by performing thorough vulnerability evaluations. For example, a financial institution may uncover that its incident response plan lacks routine testing, potentially leading to delays in addressing breaches. Recognizing such gaps enables organizations to prioritize enhancements that bolster their readiness and overall resilience.
JSOC IT's proactive monitoring and rapid incident response strategies have demonstrated effectiveness in transforming clients' security postures. This transformation allows clients to without the constant anxiety of potential threats. Their customized solutions not only address specific cybersecurity challenges but also adapt as organizational requirements evolve, ensuring robust protection and offering compliance advisory for cybersecurity across diverse industries. Organizations are urged to take decisive action, embracing these insights to fortify their cybersecurity frameworks and safeguard their assets.
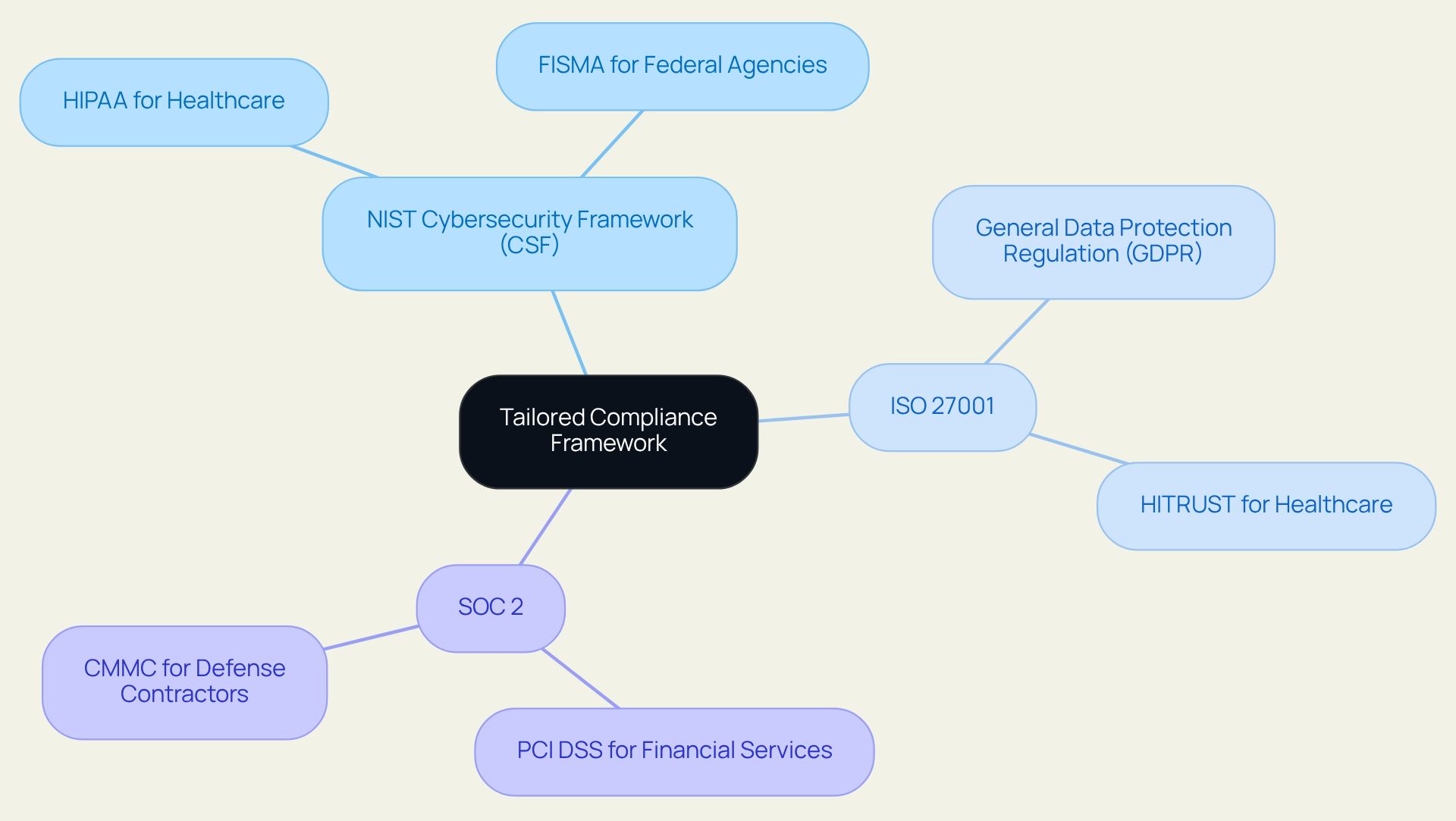
Select a Tailored Compliance Framework
Organizations must select a regulatory structure that aligns with their industry and legal obligations. Prominent frameworks include:
For instance, healthcare institutions can significantly benefit from adhering to HIPAA guidelines, while financial services companies should prioritize compliance with PCI DSS. Customizing the adherence structure to the operational environment not only ensures regulatory compliance but also acts as a compliance advisory for cybersecurity, enhancing the efficiency of protective measures in mitigating risks.
Furthermore, integrating various frameworks can address shared needs, streamlining regulatory efforts and bolstering the overall security posture. Real-world examples demonstrate that entities effectively merging with ISO 27001 and SOC 2 have achieved improved compliance outcomes and reduced audit risks. As industry leaders emphasize, a tailored compliance advisory for cybersecurity is essential for navigating the complexities of the field, ensuring that organizations remain agile and secure in an evolving threat landscape.
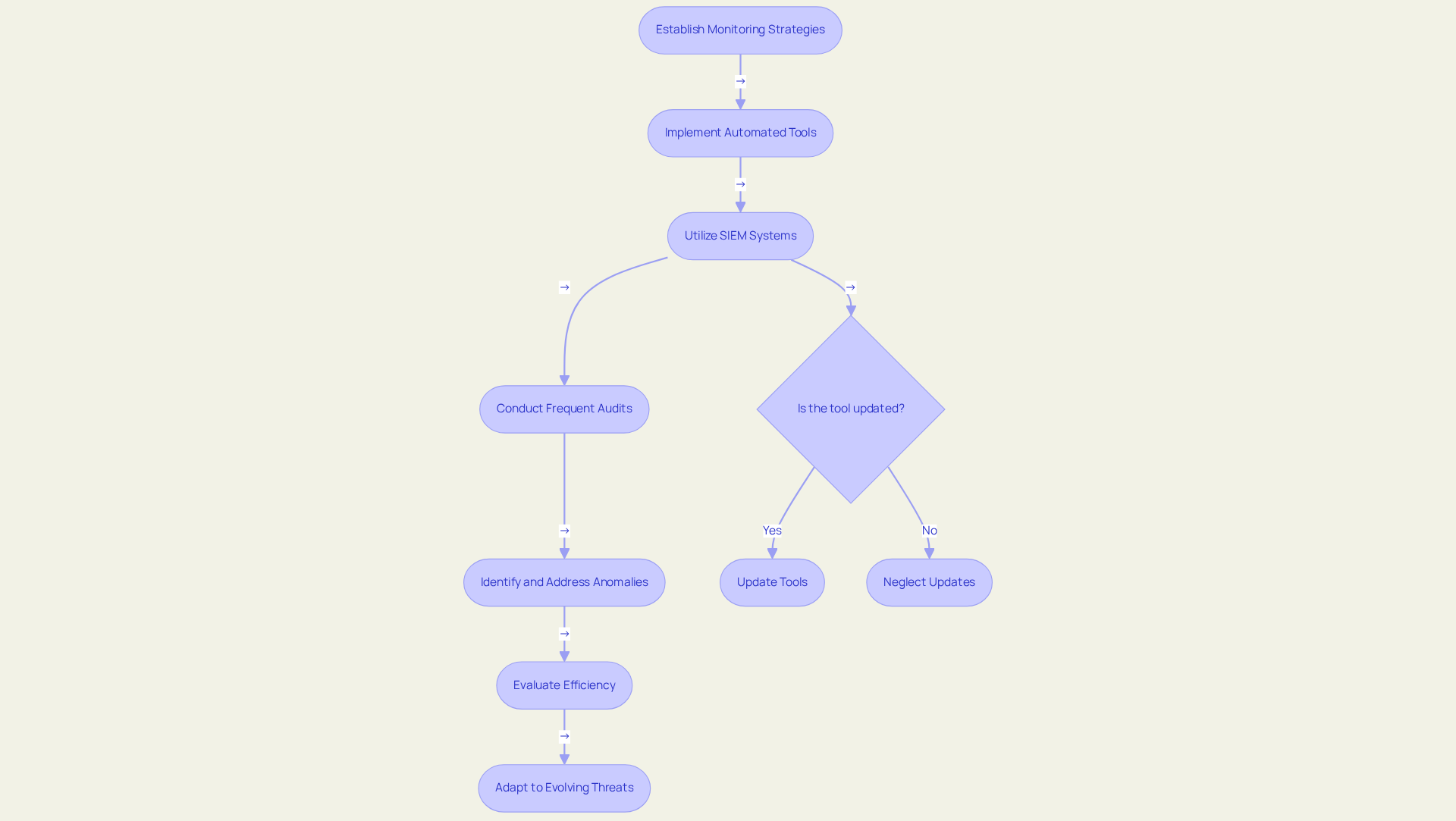
Implement Continuous Monitoring and Assessment Strategies
Establishing ongoing monitoring and evaluation strategies is paramount for effective cybersecurity adherence. Organizations must implement automated tools that significantly enhance real-time threat detection, vulnerability management, and auditing. For instance, JSOC IT underscores the necessity of a robust Security Information and Event Management (SIEM) system, which continuously analyzes logs for suspicious activities. This capability not only but also ensures that all activities are monitored and any anomalies are promptly addressed. Such measures align with JSOC IT's unwavering commitment to maintaining confidentiality and executing a comprehensive vulnerability and incident response management strategy.
According to the 2025 Verizon Data Breach Investigations Report, the anticipated increase of 34% in the use of automated threat detection tools reflects a growing awareness of their critical role in ensuring safety. Frequent audits and evaluations are essential to assess the efficiency of protective measures and ensure adherence to the compliance advisory for cybersecurity and regulatory standards. By adopting a proactive monitoring approach, organizations can swiftly identify and mitigate potential threats, thereby reinforcing their overall security framework and ensuring they follow compliance advisory for cybersecurity.
However, it is crucial for organizations to recognize common pitfalls, such as:
- Underestimating the resources required for effective monitoring
- Neglecting to regularly update their monitoring tools to adapt to evolving threats
Are you prepared to navigate these challenges and fortify your cybersecurity posture?
Conclusion
Understanding and implementing best practices for compliance advisory in cybersecurity is essential for organizations striving to protect sensitive data and adhere to regulatory standards. By grasping the complexities of the regulatory landscape, evaluating current cybersecurity measures, selecting appropriate compliance frameworks, and establishing continuous monitoring strategies, businesses can significantly enhance their security posture and mitigate risks.
The article underscores the critical importance of comprehensively understanding regulations like GDPR, HIPAA, and PCI DSS, which dictate essential requirements for data protection. It emphasizes the necessity for organizations to:
- Assess their current cybersecurity status
- Select tailored compliance frameworks that align with their specific industry needs
- Implement ongoing monitoring to ensure adherence to these regulations
Proactive approaches discussed, including the integration of automated tools for threat detection and regular audits, are crucial for maintaining a robust cybersecurity framework.
As the landscape of cybersecurity regulations continues to evolve, organizations must remain vigilant and adaptable. Embracing these best practices not only strengthens compliance but also fosters a culture of security awareness. By prioritizing these strategies, businesses can navigate the complexities of cybersecurity compliance and safeguard their assets against emerging threats. The call to action is clear: organizations must take decisive steps to fortify their defenses and ensure they are prepared for the challenges ahead in the realm of cybersecurity compliance.
Frequently Asked Questions
What are the key regulatory requirements for cybersecurity compliance?
Key regulations include the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS), which impose specific requirements regarding data handling, breach notification, and risk management.
What does GDPR require from organizations regarding data protection?
GDPR mandates that organizations implement a 'data protection by design and by default' approach, ensuring that privacy measures are integrated into their systems from the outset.
What are the main focus areas of HIPAA in terms of cybersecurity?
HIPAA emphasizes the necessity of stringent access controls and thorough audit trails for patient information to protect it from unauthorized access and breaches.
What alarming statistic highlights the need for improved cybersecurity in healthcare?
In 2023 alone, over 168 million records were compromised, underscoring the urgent need for healthcare entities to strengthen their cybersecurity frameworks.
What changes to HIPAA regulations are expected in 2025?
The upcoming changes to HIPAA regulations will introduce new adherence requirements, including enhanced encryption standards and multi-factor authentication for safeguarding electronic protected health information (ePHI).
Why is adaptability important for organizations in the context of regulatory changes?
As noted by cybersecurity specialist Steve Alder, maintaining adaptability and reliability will be crucial for organizations as they navigate regulatory shifts and enhance their cybersecurity measures.
How can organizations mitigate the risk of non-compliance penalties?
Organizations can mitigate the risk of non-compliance penalties by utilizing a compliance advisory for cybersecurity that aligns their strategies with the relevant compliance requirements.