Overview
This article emphasizes seven customized security solutions that businesses can implement to significantly enhance their protection against a variety of threats. It underscores the critical nature of tailored security measures, including:
- Integrated cybersecurity frameworks
- Comprehensive risk evaluations
- Advanced surveillance technologies
Collectively, these solutions empower organizations to effectively address specific vulnerabilities and improve incident response times.
Introduction
In a world where cyber threats are becoming increasingly sophisticated, businesses confront a formidable challenge: how to effectively safeguard their assets and data. Customized security solutions have emerged as a vital strategy, providing tailored defenses that align with the unique vulnerabilities of each organization. As companies navigate this complex landscape, a critical question arises: are standard security measures sufficient, or is it time to embrace a more integrated and personalized approach to protection? This article explores seven innovative security solutions designed to enhance business protection, ensuring that organizations are not merely reactive, but proactive in their defense strategies.
JSOC IT: Integrated Cybersecurity Solutions for Enhanced Business Protection
The IT division establishes its authority in the cybersecurity arena through the implementation of an integrated approach that merges IT operations, security measures, and compliance into a unified framework known as the 'Post-Security' model. This innovative strategy effectively dismantles silos, empowering businesses to scale with confidence while implementing customized security solutions for businesses to maintain robust defenses against breaches and vulnerabilities.
By integrating their services within client teams, JSOC IT significantly enhances incident response times—organizations have reported reductions in response duration, enabling faster containment of issues. This model not only bolsters overall security confidence but also aligns with the increasing demand for cohesive security frameworks in an ever-evolving risk environment.
Continuous threat detection and ongoing system monitoring are foundational principles that further amplify the effectiveness of the 'Post-Security' model. Sectors such as financial services and healthcare have particularly benefited from this integrated strategy, illustrating the real-world efficacy of IT solutions.
With a strong commitment to compliance with HIPAA, HITRUST, and FDA standards, the IT department ensures that is protected through initiatives like the Data Retention and Disposal Policy and Vulnerability and Patch Management Policy, while offering customized security solutions for businesses to innovate securely.
As cybersecurity specialists emphasize, a unified protective framework is essential for addressing today’s challenges, positioning IT as a dependable ally for organizations that implement customized security solutions for businesses to enhance their defenses.

Pavion: Custom Security Solutions for Enterprise-Level Protection
JSOC IT excels in delivering customized security solutions for businesses that are specifically tailored for enterprise-level clients. Their approach encompasses comprehensive risk evaluations that identify weaknesses and potential threats, followed by the implementation of cutting-edge technologies to bolster security. This personalization not only enhances the overall protective posture of organizations but also ensures .
By aligning security strategies with the unique operational requirements of each client, the IT team effectively navigates the complexities of modern cybersecurity challenges, empowering businesses to traverse the evolving threat landscape with confidence. Recent trends indicate that organizations prioritizing tailored risk evaluations have witnessed significant improvements in their security frameworks, underscoring the efficacy of JSOC IT's integrated approach.
As a client articulates, 'JSOC IT changed our protection stance overnight.' Their proactive oversight and rapid response strategies have allowed us to focus on our core operations without the persistent worry of potential threats looming overhead. Furthermore, personalized protection solutions provide comprehensive defense by addressing all conceivable vulnerabilities, emphasizing the critical need for investment in customized security solutions for businesses to effectively combat the escalating intricacies of cyber threats.

Hoosier Security: Tailored Security Systems for Modern Business Needs
Hoosier Security is dedicated to delivering customized security solutions for businesses that meet the distinct needs of modern enterprises. Their offerings include advanced surveillance technologies, sophisticated access control mechanisms, and integrated alarm systems, all meticulously designed to mitigate the specific vulnerabilities of each facility. By collaborating closely with clients, Hoosier Security not only enhances asset protection but also streamlines operational processes, ensuring that protective measures contribute to overall efficiency.
With the projected to grow at a CAGR of 11.4% from 2025 to 2030, the importance of customized protection solutions has never been more critical. As Armando Perez, President of Hoosier Security, states, "It’s our goal to provide the education necessary to clients so they don’t feel compelled to purchase a protection system that jeopardizes their personal safety."
This tailored approach is vital in an era where companies face increasingly complex protection challenges, allowing them to maintain robust defenses through customized security solutions for businesses while focusing on growth. To effectively implement customized security solutions for businesses, organizations must assess their specific vulnerabilities and collaborate with experts to develop a strategy that aligns with their operational needs.

DQS: Customized Security Solutions for Emerging Challenges
The IT division stands resolutely committed to delivering customized security solutions for businesses that effectively address the evolving challenges within the cybersecurity landscape. Their comprehensive suite of services encompasses risk evaluations, compliance guidance, and includes customized security solutions for businesses, all meticulously crafted to adapt to the shifting threat environment. By emphasizing personalization, JSOC IT offers customized security solutions for businesses to proactively address potential risks, thereby fortifying their defensive posture.
Recent data highlights the critical importance of risk assessments in bolstering security measures; organizations that engage in regular assessments can markedly diminish the average cost of a data breach, which surged by 10% from 2020 to 2021. Moreover, compliance advisory services are a crucial part of the customized security solutions for businesses, assisting them in navigating the intricate web of regulatory requirements, ensuring ongoing compliance while minimizing vulnerabilities.
For instance, a recent case study revealed that a healthcare provider, after implementing JSOC IT's risk assessment protocols, reduced its incident response time by an impressive 40%, significantly enhancing its ability to manage risks. This not only safeguards sensitive information but also cultivates a culture of awareness within organizations, ultimately resulting in a more resilient operational framework. As cybersecurity experts assert, the development of customized security solutions for businesses is paramount in today's landscape, where threats are increasingly sophisticated. JSOC IT's unwavering commitment to continuous improvement and adaptation positions its clients to stay ahead of potential risks, ensuring robust protection against emerging threats.

Ark Systems: Targeted Custom Security Solutions for Commercial Facilities
Ark Systems stands as a leader in delivering customized security solutions for businesses that are specifically tailored for commercial facilities. Their methodology commences with of facility weaknesses, which are crucial for identifying specific vulnerabilities. Industry leaders underscore the importance of these evaluations, asserting that they lay the groundwork for effective protection strategies. For instance, a comprehensive evaluation can facilitate the implementation of cutting-edge surveillance systems and advanced access control measures, thereby fortifying each facility against potential threats.
Recent developments highlight how Ark Systems has successfully transformed protective measures through these evaluations, resulting in customized security solutions for businesses that cater to unique vulnerabilities. By honing in on the distinct requirements of each facility, Ark Systems not only enhances protection but also fosters a proactive safety culture. The impact of these thorough evaluations is evident, as organizations report significant improvements in their overall security preparedness and resilience against emerging threats.

Customized Security Solutions: Tailored Alarm Systems for Business Safety
Tailored alarm systems are essential for enhancing safety in enterprises. At JSOC IT, we understand the critical importance of integrating comprehensive cybersecurity measures within these systems. Our customized security solutions for businesses include:
- Integration of motion sensors
- Door/window alarms
- Remote monitoring capabilities
All designed to meet the specific needs of your organization. By tailoring alarm systems, businesses can ensure robust protection against unauthorized access and potential threats, bolstered by our commitment to SOC 2 Type 2 certification. This certification builds trust through effective security controls and compliance monitoring, ensuring that your organization is protected by a multi-layered security approach. With IT's , you can be confident that your alarm systems are not only effective but also aligned with industry best practices for incident response and compliance.

USAPD: Customized Security Solutions for Houston Businesses
The IT division stands out in delivering customized security solutions for businesses that effectively address the diverse needs of enterprises in Houston. Their comprehensive offerings encompass:
- Advanced threat detection and response
- Managed protection services
- Expert consulting
All meticulously crafted to bolster the safety and security of local businesses. By focusing on the specific requirements of Houston's commercial community, JSOC IT guarantees that clients receive not only effective but also relevant protective solutions tailored to their operational landscapes.
This proactive strategy is crucial in a city where recent studies reveal an , with retail theft surging by 11% in 2024 and expected to escalate into 2025. High-risk areas, such as parking lots and neighborhoods like Midtown and Montrose, underscore the necessity for companies to adopt robust protective measures.
As industry leaders emphasize, investing in customized security solutions for businesses is vital for mitigating risks and ensuring operational continuity in today's complex security landscape. Integrating intelligent alarm systems with access management and monitoring enhances the overall protective framework, equipping enterprises with comprehensive safeguards against evolving threats.
The IT department's unwavering commitment to client success and compliance enables businesses to concentrate on growth initiatives without the persistent concern of potential threats overshadowing them. Their solutions have proven instrumental in assisting clients in effortlessly meeting compliance standards, allowing them to focus on their core operations.

American Power Security: Risk Assessment and Custom Planning for Unique Needs
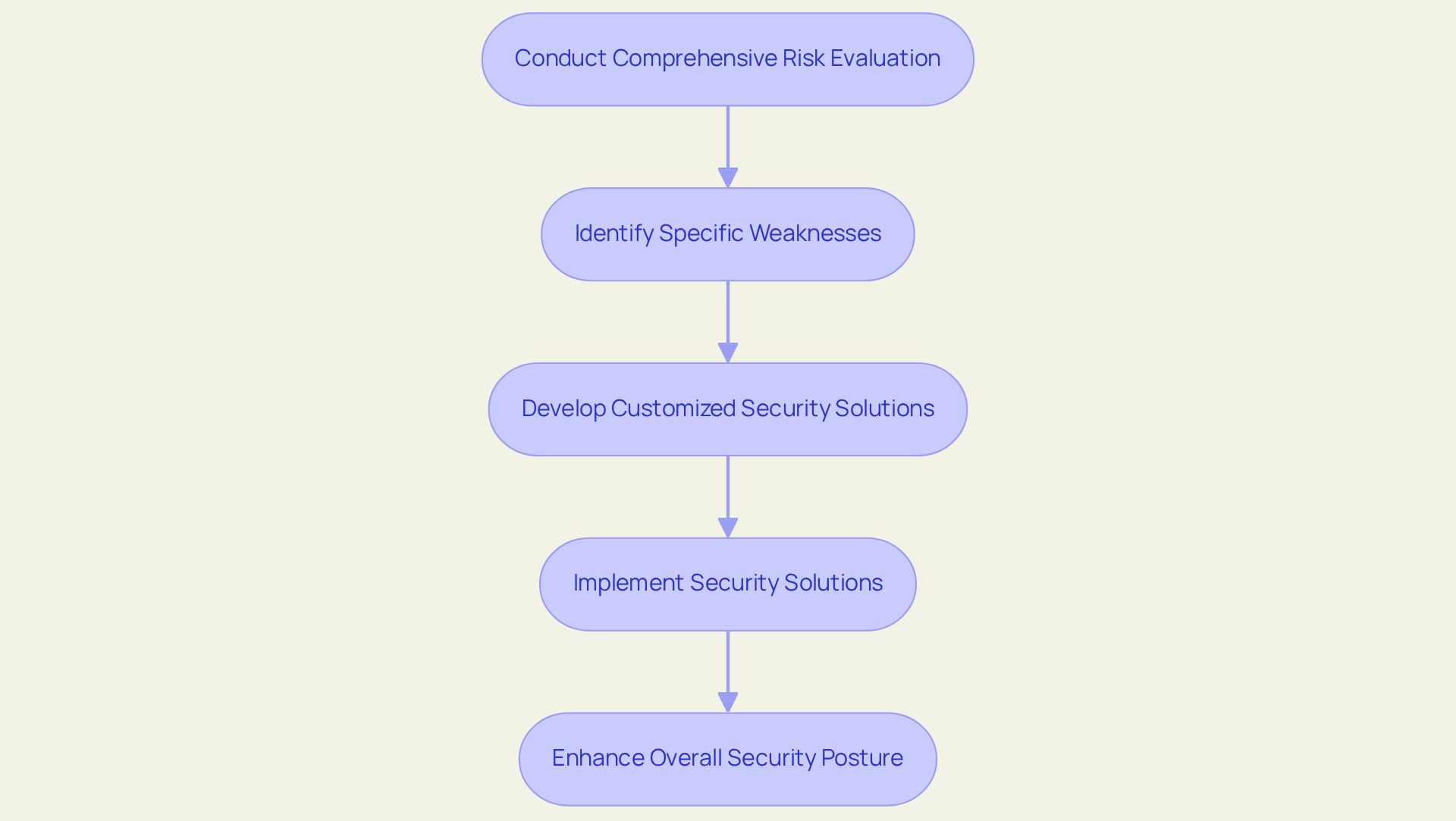
JSOC IT prioritizes comprehensive risk evaluations as the foundation for tailored protection planning. By thoroughly understanding the unique vulnerabilities of each client, they create customized security solutions for businesses that are specifically designed to address identified risks. This proactive strategy is crucial; indeed, 90% of executives recognize cyber threats as a long-term top risk, underscoring the necessity for businesses to be well-prepared to mitigate potential threats.
Organizations that implement customized security solutions for businesses report a significant reduction in incident response times and an enhanced overall security posture. According to IBM, the average cost of a data breach in healthcare is $3.62 million, highlighting the financial ramifications of neglecting vulnerabilities.
The organization’s commitment to adhering to HIPAA, HITRUST, and FDA standards ensures that sensitive patient information is protected, while their unified cybersecurity solutions provide robust defenses tailored to the specific requirements of the healthcare and financial industries. By concentrating on specific client needs, the IT department not only enhances defenses but also fosters a culture of resilience against evolving cyber threats.
To initiate tailored protection planning, CISOs should conduct a to identify specific weaknesses within their organization.
Custom Security KS: Comprehensive Security Services Including Access Control and Surveillance
The IT division delivers a comprehensive suite of protective services, encompassing access control, surveillance, and alarm systems. Their approach prioritizes the integration of diverse protective measures, including customized security solutions for businesses such as complex passwords, unique access IDs, and robust access control policies, to forge a cohesive strategy tailored to each client's specific needs.
By executing essential cybersecurity controls and maintaining continuous system monitoring—while adhering to user manuals and policies—JSOC IT ensures organizations are fortified against a wide array of threats. This holistic approach not only enhances network protection but also provides customized security solutions for businesses by incorporating lessons learned from incident response and effective risk evaluation strategies, resulting in unified cybersecurity policies and controls for superior organizational safeguarding.
To bolster protection, companies are advised to conduct regular evaluations of their safety protocols and stay updated on the .

Integration of Existing Systems: Enhancing Efficiency in Customized Security Solutions
Incorporating current protection systems into tailored solutions is crucial for enhancing efficiency and effectiveness. This seamless integration allows businesses to bolster their operational safety, significantly minimizing potential vulnerabilities. By aligning new protective measures with established infrastructure, organizations can enhance monitoring capabilities, achieve quicker response times, and adopt a more comprehensive approach to management.
For instance, organizations that integrate AI with their protection systems can decrease breach detection time by up to 85%, transforming passive defenses into smart, adaptive safeguards. Furthermore, the application of integrated guarding strategies has demonstrated an enhancement in operational results by aligning protective resources with specific risks rather than merely increasing the number of guards or cameras. This not only improves coverage but also results in a more responsive and cost-effective protection plan.
Moreover, JSOC IT offers a wide array of services, including:
- Risk detection and response
- Managed protection services
- Expert consulting
All of which can be developed as customized security solutions for businesses to meet the specific requirements of each organization. Conducting thorough physical risk evaluations prior to enhancing protection systems is essential for identifying significant dangers and ensuring that the integration process addresses particular weaknesses.
As the landscape of cybersecurity evolves, the integration of advanced technologies with existing systems will be paramount for businesses aiming to stay ahead of emerging threats and ensure robust protection. Client success stories illustrate how JSOC IT's tailored solutions have transformed security for various organizations, showcasing their commitment to effective cybersecurity measures across diverse industries.

Conclusion
The implementation of customized security solutions for businesses transcends mere trend; it is a necessity in today’s intricate cybersecurity landscape. Organizations must acknowledge the value of tailored approaches that specifically address their unique vulnerabilities and operational needs. By adopting integrated cybersecurity frameworks, businesses can significantly bolster their defenses against a multitude of threats while ensuring compliance with industry regulations.
Throughout this discourse, various providers underscore the importance of personalized security strategies. From JSOC IT's integrated approach to Ark Systems' targeted evaluations, it becomes clear that a one-size-fits-all solution is inadequate. The emphasis on risk assessments, ongoing monitoring, and the integration of advanced technologies highlights the essential role these customized solutions play in fortifying organizational security. Companies that prioritize tailored strategies not only enhance their overall security posture but also foster a culture of resilience and awareness against emerging threats.
As the cybersecurity landscape continues to evolve, it is imperative for businesses to remain proactive in their security measures. Investing in customized security solutions transcends compliance or risk mitigation; it empowers organizations to flourish in a secure environment. By embracing these tailored approaches, companies can concentrate on their core operations without the persistent anxiety of cyber threats, ultimately paving the way for sustainable growth and innovation.
Frequently Asked Questions
What is the 'Post-Security' model implemented by JSOC IT?
The 'Post-Security' model is an integrated approach that merges IT operations, security measures, and compliance into a unified framework, effectively dismantling silos and empowering businesses to implement customized security solutions.
How does JSOC IT enhance incident response times?
By integrating their services within client teams, JSOC IT significantly improves incident response times, leading to faster containment of issues reported by organizations.
What are the foundational principles of the 'Post-Security' model?
Continuous threat detection and ongoing system monitoring are the foundational principles that enhance the effectiveness of the 'Post-Security' model.
Which sectors have particularly benefited from JSOC IT's integrated strategy?
Sectors such as financial services and healthcare have particularly benefited from the integrated strategy offered by JSOC IT.
How does JSOC IT ensure compliance with industry standards?
The IT department ensures compliance with standards such as HIPAA, HITRUST, and FDA through initiatives like the Data Retention and Disposal Policy and Vulnerability and Patch Management Policy.
What does JSOC IT offer to enhance business protection?
JSOC IT offers customized security solutions tailored for enterprise-level clients, including comprehensive risk evaluations and the implementation of cutting-edge technologies.
What is the significance of tailored risk evaluations in cybersecurity?
Tailored risk evaluations help identify weaknesses and potential threats, leading to significant improvements in security frameworks for organizations that prioritize them.
How does Hoosier Security approach customized security solutions?
Hoosier Security delivers customized solutions that include advanced surveillance technologies, access control mechanisms, and integrated alarm systems, designed to mitigate specific vulnerabilities of each facility.
What is the projected growth rate for the commercial protection system market?
The commercial protection system market is projected to grow at a CAGR of 11.4% from 2025 to 2030.
Why is a tailored approach to security systems important for modern businesses?
A tailored approach is vital as it allows companies to maintain robust defenses against increasingly complex protection challenges while focusing on growth.




