Overview
The article delineates four critical cybersecurity compliance solutions tailored for Chief Information Security Officers (CISOs), underscoring the necessity of adhering to regulations such as GDPR, HIPAA, and PCI-DSS to safeguard sensitive data and avert substantial penalties. It articulates a thorough approach that encompasses:
- Conducting compliance assessments
- Formulating security policies
- Instituting continuous monitoring and training programs
These measures are vital for bolstering organizational resilience against cyber threats, thereby enhancing overall security posture.
Introduction
In an era where data breaches can result in severe financial and reputational harm, the significance of cybersecurity compliance has never been more pronounced. Organizations across diverse sectors must navigate a complex web of regulations, including:
- GDPR
- HIPAA
- PCI-DSS
All while safeguarding sensitive information and maintaining customer trust. The challenge, however, lies in comprehending and implementing effective compliance strategies that not only satisfy regulatory requirements but also bolster the overall security posture.
What essential solutions can Chief Information Security Officers (CISOs) leverage to ensure their organizations remain compliant and resilient against the ever-evolving landscape of cyber threats?
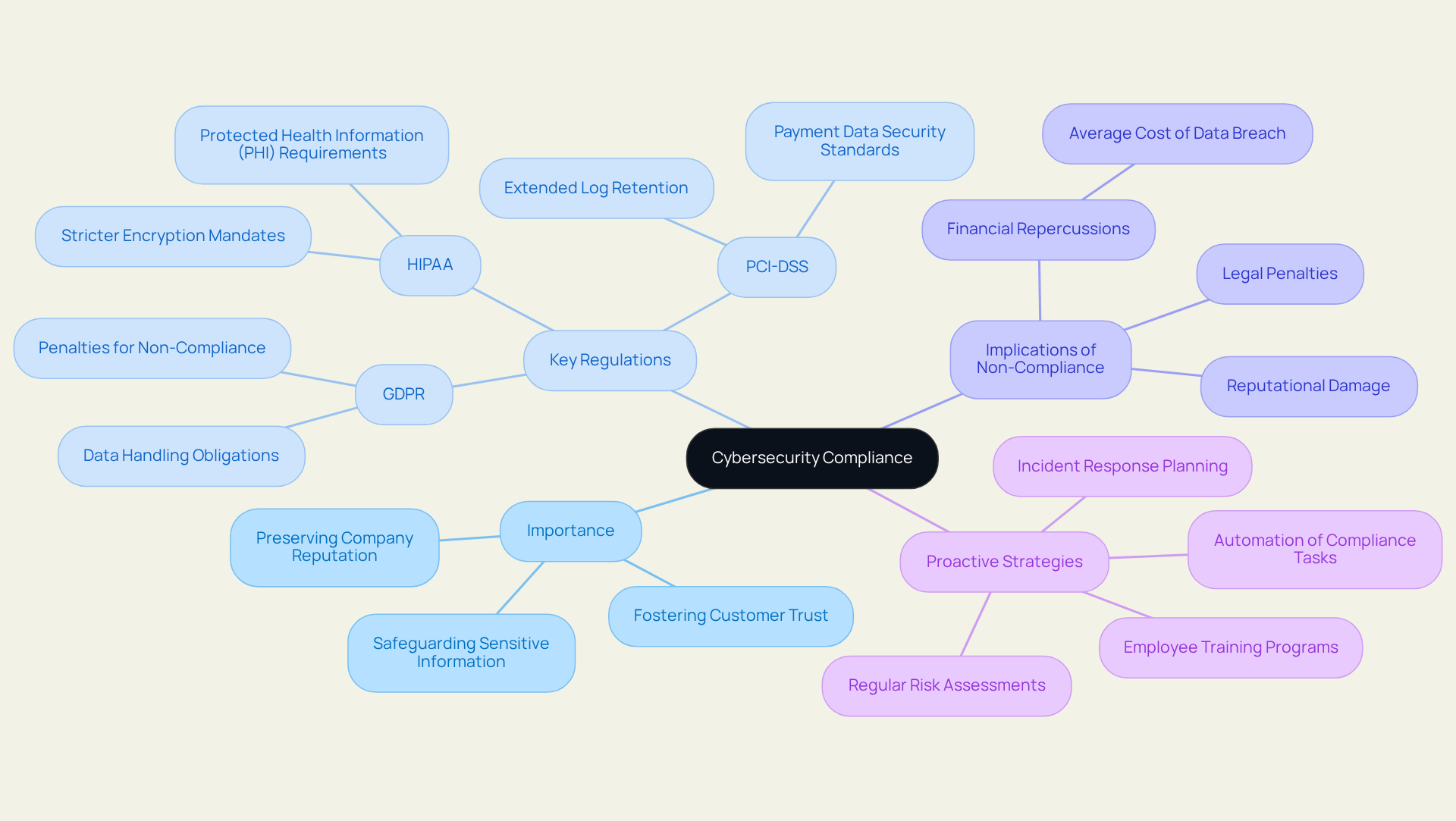
Define Cybersecurity Compliance and Its Importance
The paramount importance of cybersecurity compliance solutions involves adherence to laws, regulations, and standards that dictate how entities manage and safeguard sensitive information. This compliance is especially critical in sectors like financial services and healthcare, where data breaches can lead to significant legal and financial repercussions. Not only does compliance necessitate the implementation of essential security measures to defend against cyber threats, but it also plays a crucial role in preserving a company's reputation and fostering customer trust.
JSOC IT distinguishes itself in this arena by providing integrated cybersecurity solutions tailored to the unique needs of various industries. Our commitment to working alongside your team allows us to merge IT, cybersecurity, compliance, and operations into a cohesive service, revolutionizing the approach to cybersecurity. Key regulations such as GDPR, HIPAA, and PCI-DSS impose specific obligations that entities must meet to mitigate risks and evade penalties. For example, GDPR updates are projected to elevate standards for all data handlers by 2025, while HIPAA will introduce stricter encryption mandates for protected health information (PHI). Additionally, PCI-DSS requirements, including extended log retention and enhanced multi-factor authentication, are vital for organizations managing payment data.
Understanding these regulations is the foundational step in crafting a robust adherence strategy that aligns with both organizational objectives and industry standards. Compliance is a continuous process, necessitating regular evaluations and adjustments to cybersecurity compliance solutions to keep pace with evolving rules and threats. Entities that engage proactively with these regulatory frameworks—especially through JSOC IT's flexible cybersecurity compliance solutions, which include advanced protective measures and comprehensive services—not only bolster their defense posture but also position themselves to navigate the dynamic landscape of cyber threats more effectively. Real-world instances illustrate that businesses prioritizing have successfully strengthened their security measures, thereby reducing the likelihood of breaches and fostering a culture of accountability and resilience. Furthermore, the financial implications of non-compliance are substantial, with the average cost of a data breach projected to reach $4.88 million in 2024, underscoring the critical importance of adhering to regulatory standards.
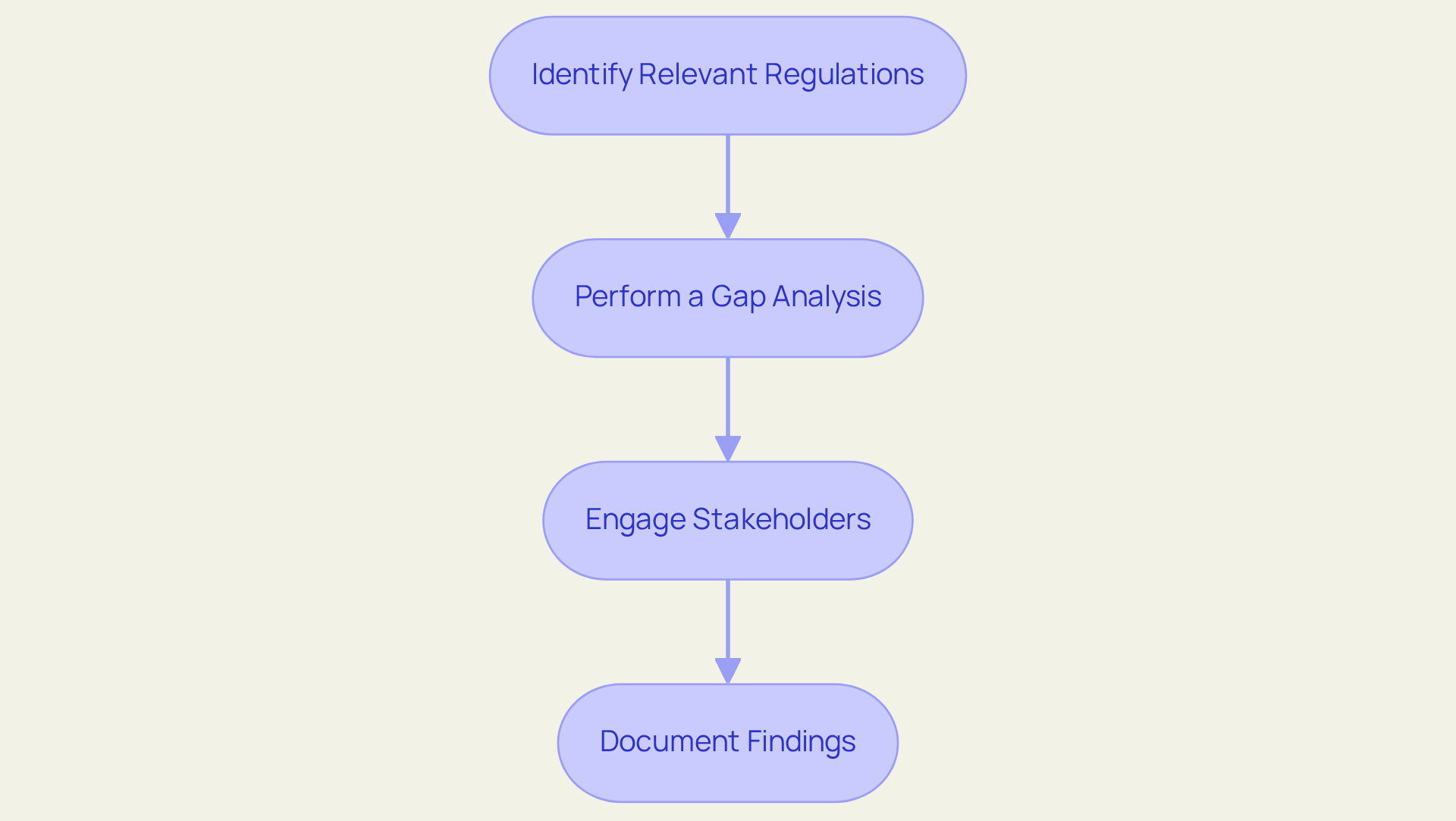
Conduct a Comprehensive Compliance Assessment
To conduct a comprehensive compliance assessment, follow these essential steps:
- Identify Relevant Regulations: Begin by determining which regulations apply to your entity based on your industry and the types of data you handle. This may encompass GDPR for , HIPAA for healthcare information, or PCI-DSS for payment data. Notably, over 70% of entities have reported challenges in identifying regulations specific to their sector, underscoring the critical need for thorough research.
- Perform a Gap Analysis: Next, compare your current security practices against the requirements of the identified regulations. This analysis should reveal areas where your organization is non-compliant or at risk. Organizations that conduct regular gap assessments are better equipped to adapt to evolving regulatory requirements, particularly in sectors like healthcare and finance, where cybersecurity compliance solutions are essential due to intensifying oversight.
- Engage Stakeholders: It is crucial to involve key stakeholders from various departments, including IT, legal, and operations, to gather insights and ensure a comprehensive understanding of regulatory requirements. Effective collaboration among departments can significantly enhance the accuracy of your regulatory evaluation and foster a culture of accountability.
- Document Findings: Finally, create a detailed report of your findings, encompassing identified gaps, potential risks, and recommendations for remediation. This documentation will serve as a strategic roadmap for your compliance efforts. Organizations that maintain auditable trails across all compliance-related processes are more likely to demonstrate accountability and readiness during audits, ultimately bolstering their credibility with regulators and stakeholders.
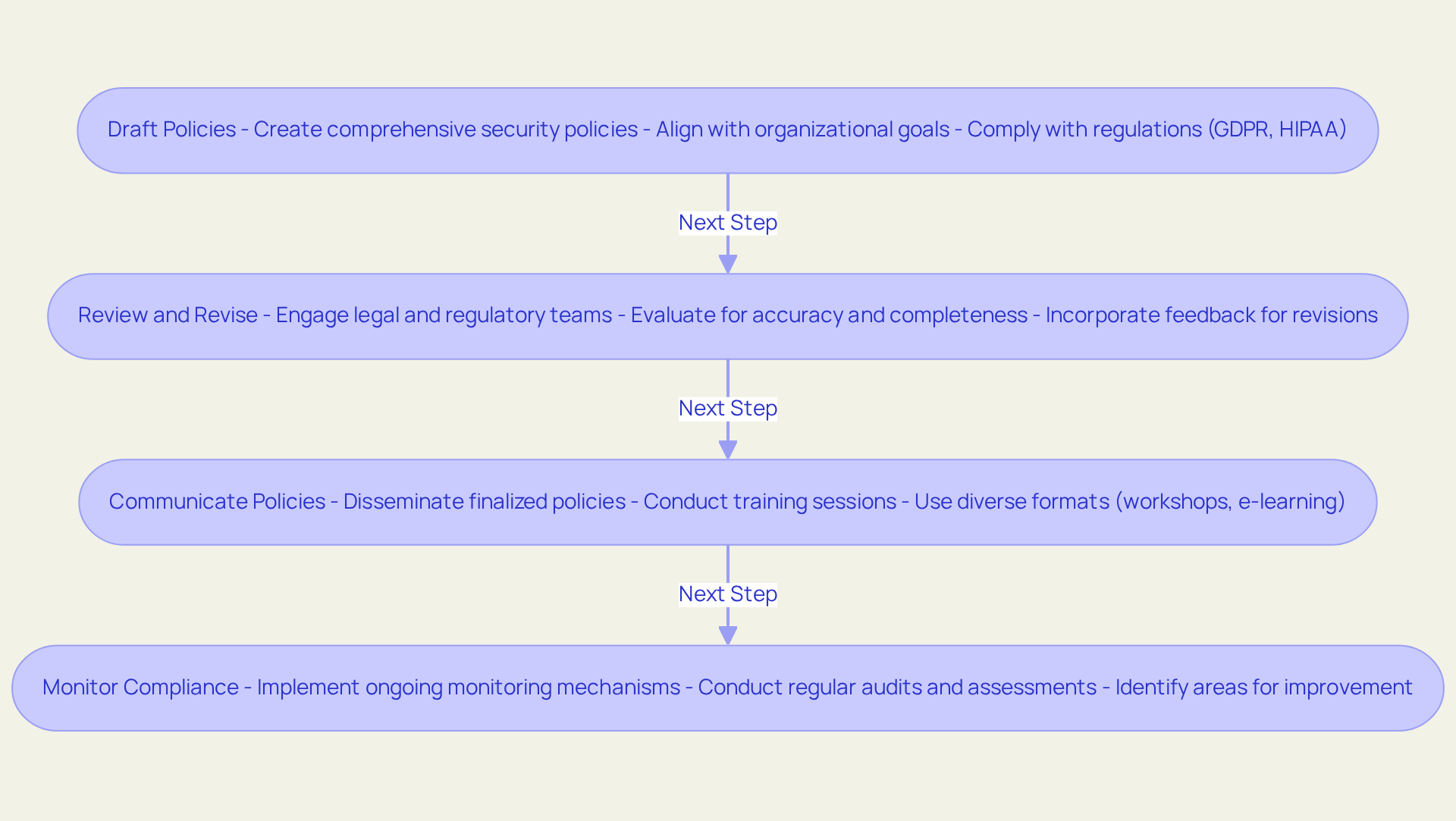
Develop and Implement Security Policies and Procedures
Developing and implementing effective security policies necessitates several key steps:
- Draft Policies: Begin by creating comprehensive security policies that encompass critical areas such as data protection, incident response, access control, and employee training. These policies must align with organizational goals and comply with regulatory requirements like GDPR and HIPAA, which mandate specific protections for sensitive data, by implementing cybersecurity compliance solutions.
- Review and Revise: Engage legal and regulatory teams to rigorously evaluate the policies for accuracy and completeness. This step is crucial; entities that incorporate legal insights into their policy development are better positioned to meet and mitigate potential penalties. Constructive feedback from these teams should inform revisions, ensuring that all necessary regulations are addressed.
- Communicate Policies: Disseminate the finalized policies to all employees and conduct sessions to ensure understanding and compliance. Employing diverse formats—such as workshops, e-learning modules, and written documentation—can significantly enhance engagement. Data indicates that organizations with robust training initiatives experience a notable reduction in incidents, with effective training improving employee awareness and adherence by up to 70%.
- Monitor Compliance: Implement mechanisms for ongoing monitoring of adherence to the policies, including regular audits and assessments. This proactive strategy is essential for identifying areas for improvement and ensuring continuous cybersecurity compliance solutions, especially as regulatory scrutiny intensifies. Organizations that conduct frequent adherence assessments are more likely to maintain a strong protective posture and minimize risks associated with non-compliance.
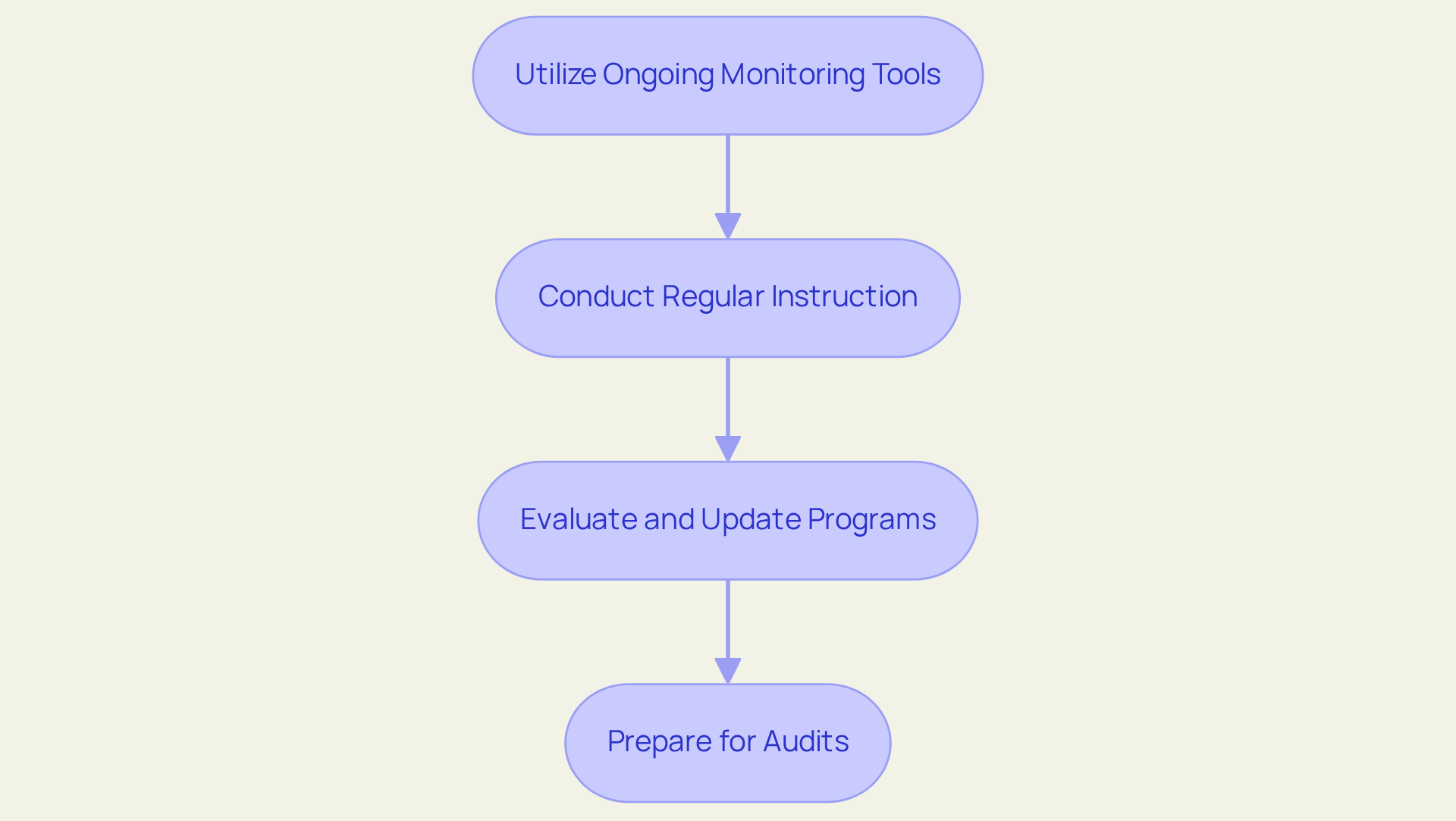
Establish Continuous Monitoring and Training Programs
To establish effective continuous monitoring and training programs, consider the following steps:
- Utilize Ongoing Monitoring Tools: Employ automated instruments to consistently assess your protective stance and adherence status. These tools are essential for identifying vulnerabilities, monitoring adherence metrics, and generating audit-ready reports.
- Conduct Regular Instruction: Develop a comprehensive educational program that includes frequent updates on compliance requirements, security best practices, and emerging threats. Engaging development customized for employees' specific roles enhances retention and effectiveness. With nearly 90% of organizations reporting cyber incidents last year, the necessity for cannot be overstated.
- Evaluate and Update Programs: Regularly assess the effectiveness of your monitoring and development initiatives. Collect feedback from employees to refine content and delivery methods, ensuring they remain relevant and engaging. Ongoing enhancement is essential; efficient education can greatly lessen the risk of cyberattacks, with 96% of executives believing that organization-wide instruction can alleviate threats.
- Prepare for Audits: Maintain comprehensive documentation of adherence efforts, including training records, monitoring reports, and policy updates. This thorough documentation not only facilitates smoother audits but also demonstrates your organization’s commitment to maintaining high standards of cybersecurity compliance solutions.
Conclusion
The significance of cybersecurity compliance is paramount, particularly for organizations navigating the complexities of safeguarding sensitive information. By adhering to established regulations and standards, entities not only shield themselves from legal and financial repercussions but also cultivate a foundation of trust and reliability with their customers. The integration of tailored cybersecurity solutions, such as those provided by JSOC IT, is essential in fostering a proactive approach to compliance, ensuring that organizations remain resilient against evolving cyber threats.
Throughout this article, key strategies for achieving robust cybersecurity compliance have been articulated. These strategies include:
- Conducting comprehensive compliance assessments to identify relevant regulations
- Developing and implementing effective security policies
- Establishing continuous monitoring and training programs
Each of these steps plays a crucial role in not only meeting regulatory requirements but also enhancing the overall security posture of an organization. The emphasis on collaboration among stakeholders and the importance of ongoing education further underscore the necessity of a holistic approach to compliance.
Ultimately, the journey toward cybersecurity compliance is an ongoing process that demands vigilance and adaptability. Organizations are encouraged to prioritize their compliance efforts, recognizing that the landscape of cyber threats is ever-changing. By embracing best practices and leveraging advanced compliance solutions, businesses can not only mitigate risks but also position themselves as leaders in their respective industries. Taking decisive action now will pave the way for a more secure and compliant future, ultimately safeguarding both the organization and its stakeholders.
Frequently Asked Questions
What is cybersecurity compliance?
Cybersecurity compliance refers to adherence to laws, regulations, and standards that dictate how organizations manage and protect sensitive information, particularly in sectors like financial services and healthcare.
Why is cybersecurity compliance important?
Cybersecurity compliance is crucial because it helps prevent data breaches that can lead to significant legal and financial consequences. It also protects a company's reputation and fosters customer trust.
What are some key regulations related to cybersecurity compliance?
Key regulations include GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and PCI-DSS (Payment Card Industry Data Security Standard), which impose specific obligations on entities to manage data securely.
How do regulations like GDPR and HIPAA affect organizations?
GDPR updates are expected to raise standards for all data handlers by 2025, while HIPAA will introduce stricter encryption mandates for protected health information. Compliance with these regulations is essential to mitigate risks and avoid penalties.
What role does JSOC IT play in cybersecurity compliance?
JSOC IT provides integrated cybersecurity solutions tailored to the unique needs of various industries, merging IT, cybersecurity, compliance, and operations into a cohesive service to enhance cybersecurity efforts.
How can organizations ensure they remain compliant?
Organizations must engage proactively with regulatory frameworks, regularly evaluate and adjust their cybersecurity compliance solutions, and implement advanced protective measures to keep pace with evolving rules and threats.
What are the financial implications of non-compliance?
The average cost of a data breach is projected to reach $4.88 million in 2024, highlighting the critical importance of adhering to regulatory standards to avoid substantial financial losses.
How does prioritizing compliance benefit businesses?
Businesses that prioritize regulatory compliance can strengthen their security measures, reduce the likelihood of breaches, and foster a culture of accountability and resilience.