Overview
The article articulates strategies for achieving zero breach cybersecurity services, underscoring the necessity of integrating IT operations, security measures, and compliance within a cohesive framework. It elaborates on various approaches, including:
- The 'Post-Security' model
- Regular software updates
- Cybersecurity awareness training
- Managed security services
All designed to bolster an organization's defenses against cyber threats.
Introduction
In an era where cyber threats have evolved to be more sophisticated and pervasive than ever, organizations confront an urgent imperative to bolster their defenses against breaches. Zero breach cybersecurity services have surfaced as a pivotal strategy for protecting sensitive data and ensuring compliance across diverse industries. This article explores ten essential strategies that not only enhance security measures but also empower businesses to adeptly navigate the complexities of modern cyber risks.
How can organizations effectively implement these strategies to guarantee they remain one step ahead of potential threats?
JSOC IT: Comprehensive Cybersecurity Solutions for Zero Breach
JSOC IT's 'Post-Security' model revolutionizes cybersecurity by seamlessly integrating IT operations, security measures, and compliance into a unified framework. This innovative approach dismantles traditional silos, enabling real-time threat detection and response. By integrating their services within client teams, JSOC IT empowers companies to scale confidently, backed by zero breach cybersecurity services to defend against breaches and vulnerabilities.
Their comprehensive range of services, featuring round-the-clock monitoring, automated remediation, and incident response, is meticulously customized to meet the distinct needs of industries such as financial services and healthcare, where protection and compliance are paramount. Furthermore, JSOC IT offers a flat-rate pricing model, ensuring predictable costs without hidden fees, thus enhancing budget management for clients.
Their susceptibility and update management strategies bolster protective measures, ensuring that entities are well-guarded against emerging risks. By embedding cybersecurity measures into the fabric of client operations, businesses can not only safeguard sensitive information but also enhance their overall operational efficiency.
As the cybersecurity landscape evolves, trends indicate a growing emphasis on integrated services, particularly zero breach cybersecurity services, that prioritize collaboration and customization. This shift reflects a broader recognition that transcends mere technical challenges; it is a strategic imperative requiring a holistic approach. By embracing the 'Post-Security' model, entities can navigate the complexities of contemporary threats while maintaining a robust protective stance.
Zero Trust Architecture: Strengthening Security Posture
embodies the principle of 'never trust, always verify,' mandating rigorous identity verification for every user and device seeking access to resources, irrespective of their location. By employing micro-segmentation, least privilege access policies, and restricted port configurations, entities can drastically minimize their attack surface. This proactive strategy not only safeguards sensitive data but also bolsters compliance with industry regulations, making it an essential element of a comprehensive cybersecurity framework.
Essential access protection measures, such as intricate passwords, distinct access IDs, and strict access control policies, are crucial for improving network safety and access management within integrated service models. Notably, organizations adopting Zero Trust have reported an 83% reduction in security incidents, underscoring its effectiveness in enhancing overall security posture.
Additionally, the incorporation of AI functionalities into Zero Trust tools is anticipated to increase considerably, with 60% of these tools expected to integrate advanced features by 2028, further enhancing protections against emerging challenges. As emphasized by experts, Zero Trust is not a one-time implementation but requires continuous commitment and adaptation to effectively combat evolving threats.
JSOC IT's integrated cybersecurity solutions, including endpoint protection, are designed to scale securely with customized support, ensuring compliance and safeguarding sensitive data across sectors, particularly in financial services.
Regular Software Updates: Essential for Vulnerability Management
Regular software updates are essential for maintaining robust cybersecurity. These updates often include crucial security patches that address known vulnerabilities, which, if neglected, can lead to significant breaches. In 2025, the landscape of cyber risks continues to evolve, with unpatched software responsible for 60% of data breaches globally. Organizations must establish a routine for checking and applying updates across all software and systems. This proactive approach not only safeguards against potential exploits but also , reducing crashes and improving user experience.
For instance, the Travelex ransomware attack exemplifies the severe consequences of neglecting updates, underscoring the critical need for timely software management. Furthermore, adopting automated update systems can streamline this process, ensuring that critical patches are applied promptly and without manual intervention. As Travis Thompson notes, organizations should leverage automatic updates to ensure timely installations. By prioritizing timely updates, businesses can significantly bolster their defenses against cyber risks through zero breach cybersecurity services, maintain compliance with industry regulations such as GDPR and HIPAA, and enhance operational efficiency.
JSOC IT's commitment to tailored cybersecurity solutions ensures that these updates are integrated into a comprehensive strategy that addresses the unique challenges faced by different industries, reinforcing business continuity and disaster recovery efforts.
Cybersecurity Awareness Training: Empowering Employees Against Threats
Cybersecurity awareness training equips employees with essential knowledge and skills to identify and respond to potential threats. Regular training sessions must encompass critical topics, including:
- Phishing
- Password management
- Safe internet practices
By cultivating a culture of security awareness, organizations can significantly mitigate the risk of human error that may lead to security breaches. Engaging training methods, such as simulations and real-world scenarios, not only enhance retention but also improve the overall effectiveness of the training. Consider the impact: organizations that prioritize cybersecurity training can see a marked decrease in incidents. Are you ready to take action and fortify your organization's defenses?
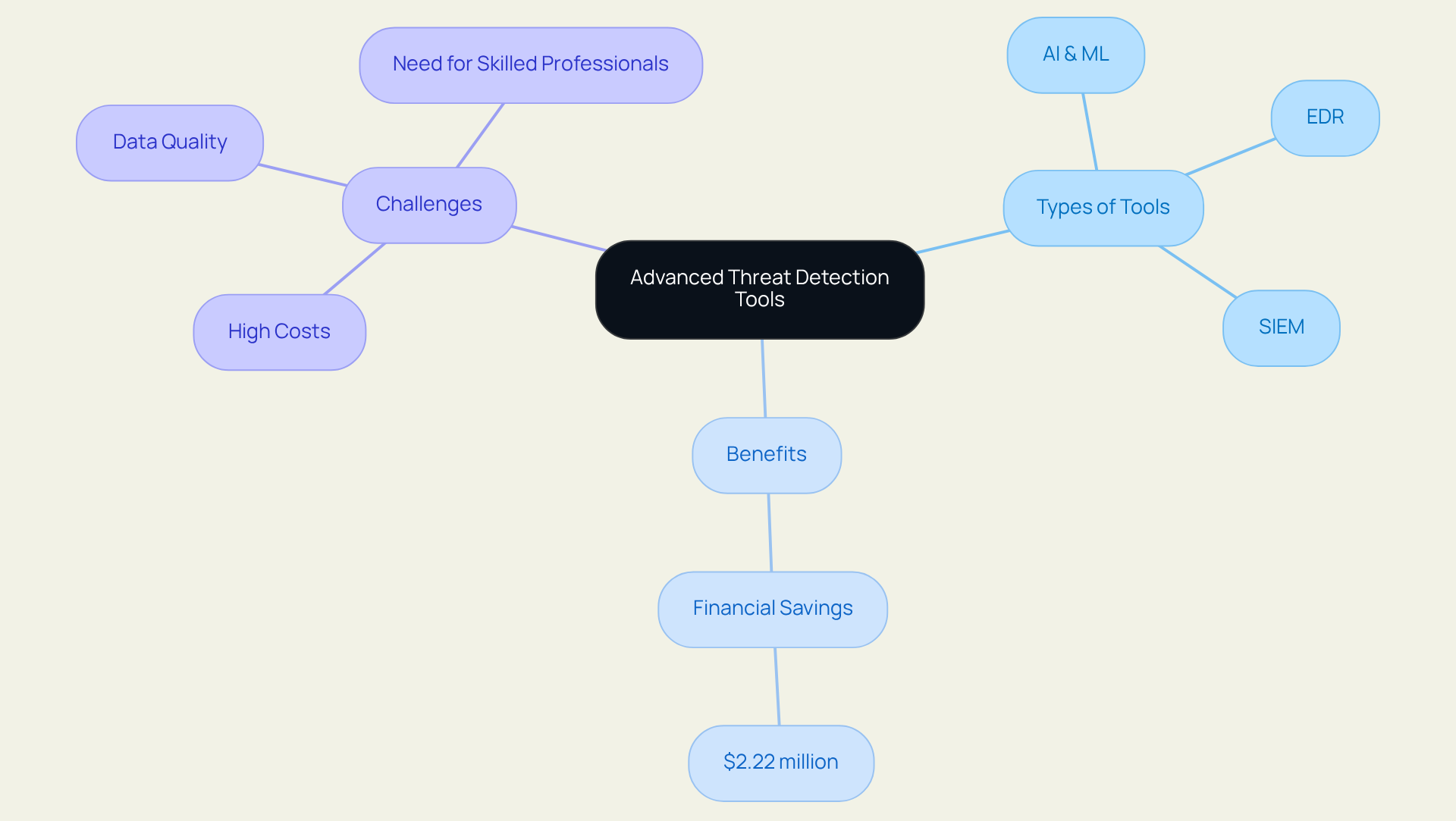
Advanced Threat Detection Tools: Proactive Defense Mechanisms
Employing advanced risk detection tools is essential for proactive cybersecurity. These tools harness and machine learning to identify anomalies and potential risks in real-time. Solutions such as Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM) systems—prominent platforms like Darktrace and Vectra AI—enable organizations to monitor their networks continuously.
By integrating these tools into their security framework, companies can significantly enhance their ability to identify and respond to threats swiftly, thereby minimizing potential damage. Furthermore, organizations that utilize AI-driven protection tools have reported average savings of $2.22 million compared to those that do not, underscoring the financial benefits of these advanced cybersecurity measures.
However, it is crucial to recognize the challenges associated with AI integration, including high costs, data quality concerns, and the necessity for skilled professionals. By adopting these technologies within their protective strategies, businesses can not only bolster their threat detection capabilities but also refine their incident response processes, ensuring a robust defense against the evolving landscape of cyber threats.
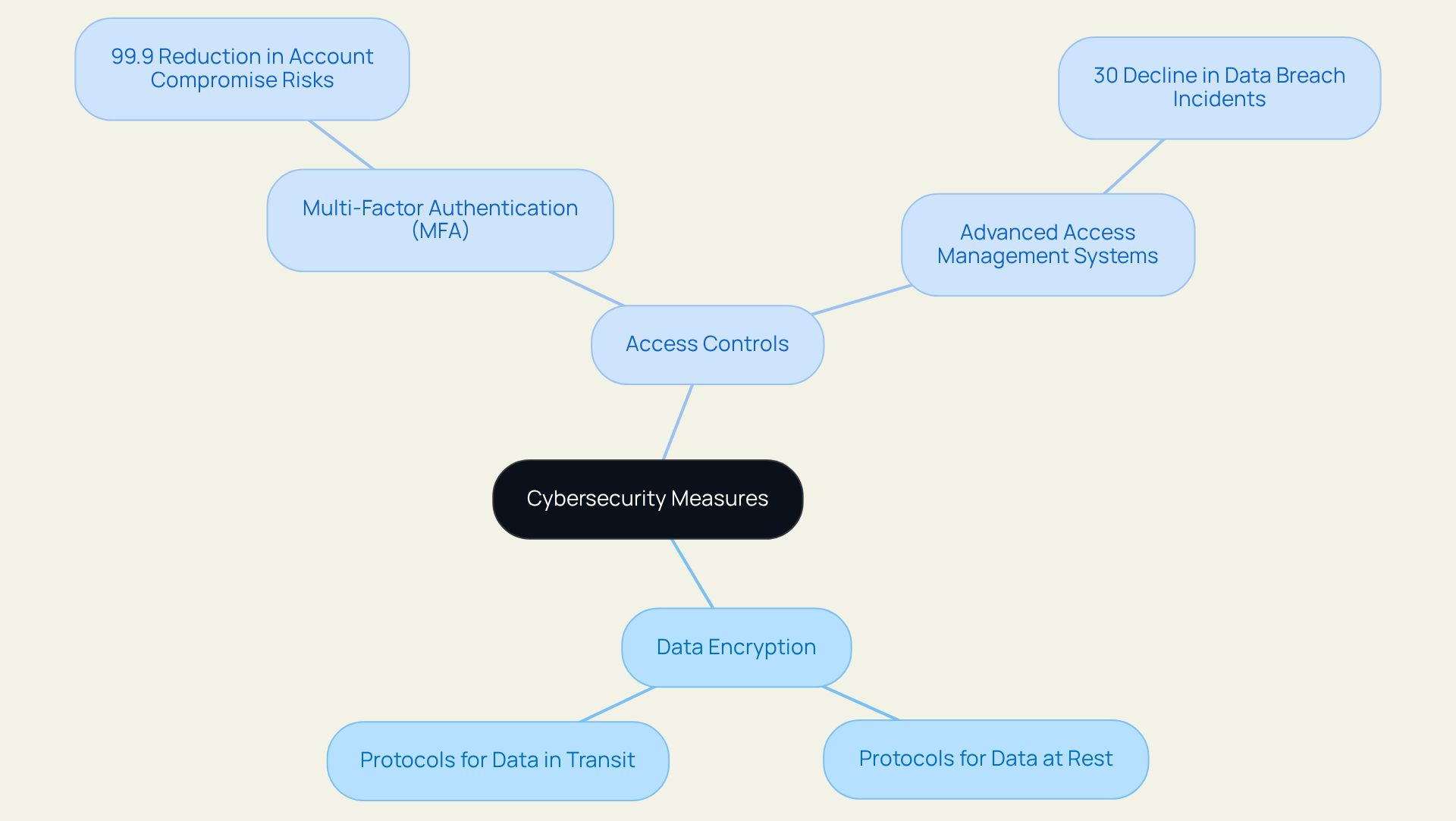
Data Encryption and Access Controls: Safeguarding Sensitive Information
Data encryption stands as a cornerstone of cybersecurity, protecting sensitive information from unauthorized access. Organizations must implement robust encryption protocols for both data at rest and in transit, ensuring that intercepted data remains unreadable. Access controls are integral to this framework, limiting data access exclusively to authorized personnel. The implementation of (MFA) significantly bolsters security by necessitating multiple verification methods, complicating unauthorized access attempts. A recent study highlighted that entities employing MFA experienced a staggering 99.9% reduction in account compromise risks. Moreover, real-world applications of access controls have showcased their effectiveness; companies that adopted advanced access management systems reported a 30% decline in data breach incidents. As we approach 2025, the significance of these measures cannot be overstated; they constitute the backbone of a proactive cybersecurity strategy that employs zero breach cybersecurity services to prevent breaches and safeguard sensitive data.
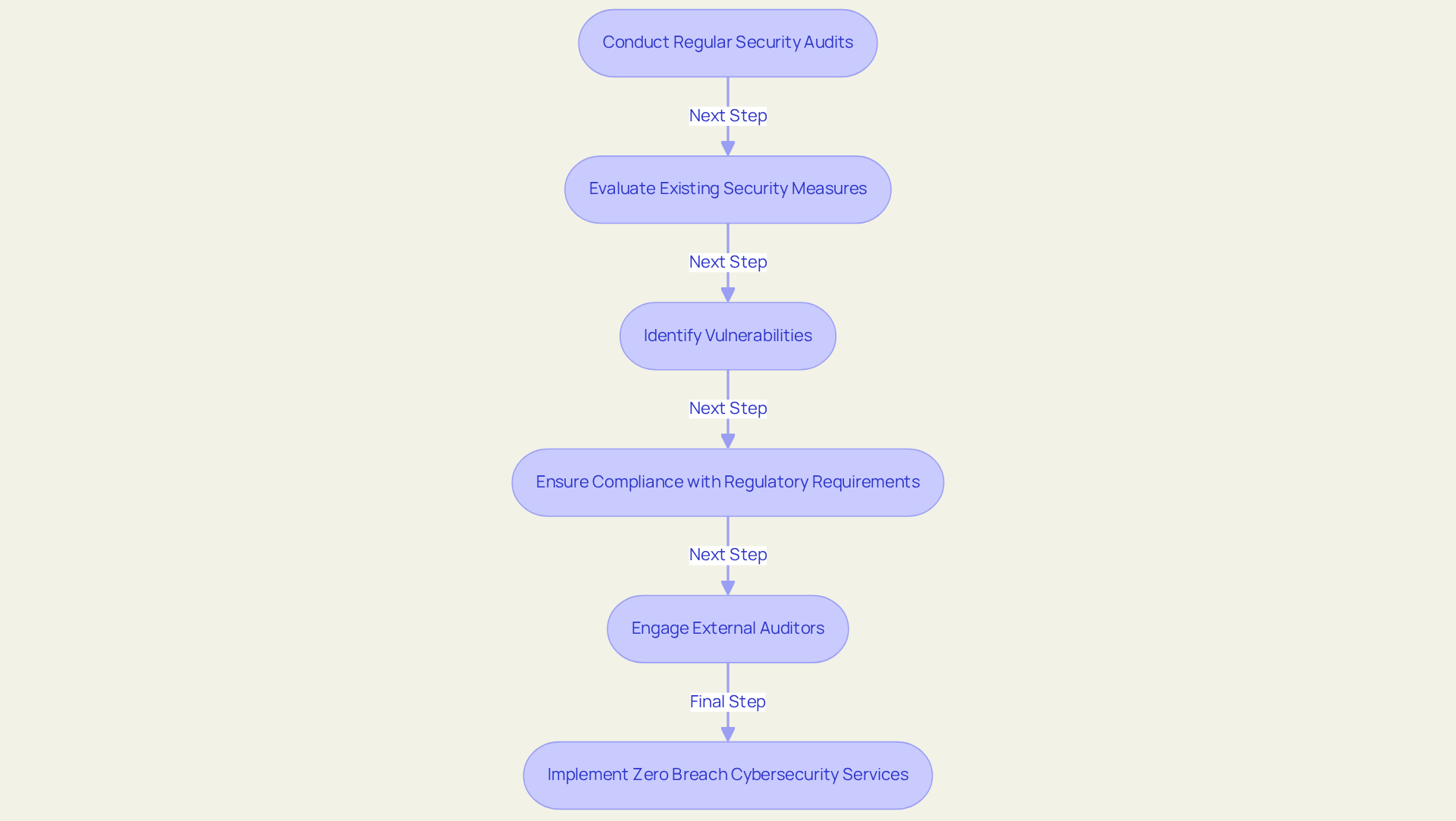
Regular Security Audits: Identifying and Mitigating Risks
Carrying out routine safety assessments is essential for identifying and mitigating threats within a company, and implementing zero breach cybersecurity services can significantly enhance this process. These audits rigorously evaluate the effectiveness of existing security measures, pinpoint vulnerabilities, and ensure compliance with regulatory requirements. Establishing a regular audit timetable empowers companies to proactively address potential vulnerabilities before they can be exploited. In 2024, healthcare data breaches surged to a staggering 1,160 incidents, underscoring the urgent need for such proactive measures.
Engaging external auditors can provide an impartial evaluation, offering insights that enable entities to benchmark their protective stance against industry standards. This strategy not only enhances credibility but also with regulations such as HIPAA and PCI-DSS, which mandate regular audits. For instance, entities that embraced a hybrid audit approach reported moderate expenses while achieving an improved value balance, illustrating that effective audits need not be overly complex or costly.
Moreover, regular audits play a pivotal role in the effectiveness of zero breach cybersecurity services for risk mitigation. They assist entities in identifying and addressing vulnerabilities, with research indicating that consistent evaluations can significantly reduce the likelihood of data breaches by uncovering weaknesses early. As David Angerdina, Cyber Practice Lead, asserts, "Cybersecurity audits are a strategic protection against increasing risks." By cultivating a culture of security awareness and continuous improvement, organizations can bolster their overall security posture and maintain compliance in an increasingly complex threat landscape.
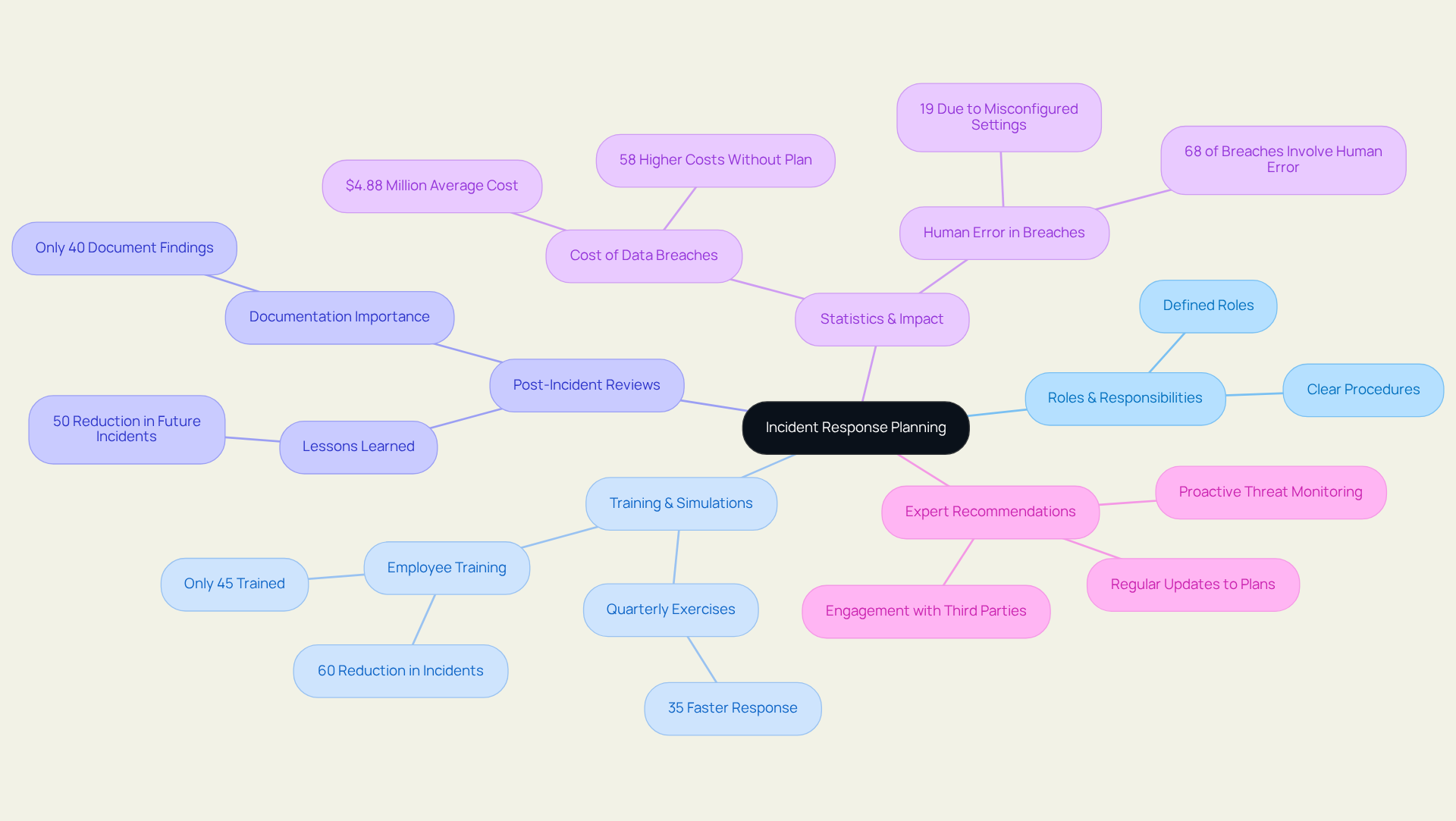
Incident Response Planning: Preparing for Cybersecurity Incidents
A robust response strategy is crucial for mitigating the impact of cybersecurity incidents. Organizations must develop a comprehensive plan that clearly defines roles, responsibilities, and procedures tailored to various event types. Regular training and simulations are essential; they ensure that team members are thoroughly familiar with the plan and can respond effectively during a breach. Notably, firms that conduct response exercises at least quarterly can react 35% faster to incidents, significantly reducing potential damage. However, only 30% of organizations routinely evaluate their response strategies, revealing a substantial gap in preparedness.
Moreover, post-incident reviews are vital for extracting lessons learned, enabling organizations to refine their response strategies and enhance future readiness. As highlighted by industry experts, a strong response strategy can mean the difference between a controlled recovery and a total disaster. Businesses without a formal response strategy face 58% higher costs per breach compared to those with structured, practiced response protocols.
By prioritizing training and continuous improvement, organizations can substantially bolster their cybersecurity posture and mitigate the effects of breaches. JSOC IT underscores the importance of a multi-layered approach to response situations, integrating change management and secure development policies to ensure business continuity and disaster recovery.
CISA encourages organizations to apply these lessons learned to strengthen their security posture, enhance preparedness, and diminish the risk of future compromises. With the projected to reach $4.88 million in 2024, the urgency for effective response planning has never been more critical. Furthermore, it is essential to recognize that 68% of breaches stem from human error, highlighting the necessity for comprehensive training and simulations to address the risks associated with human factors in cybersecurity incidents.
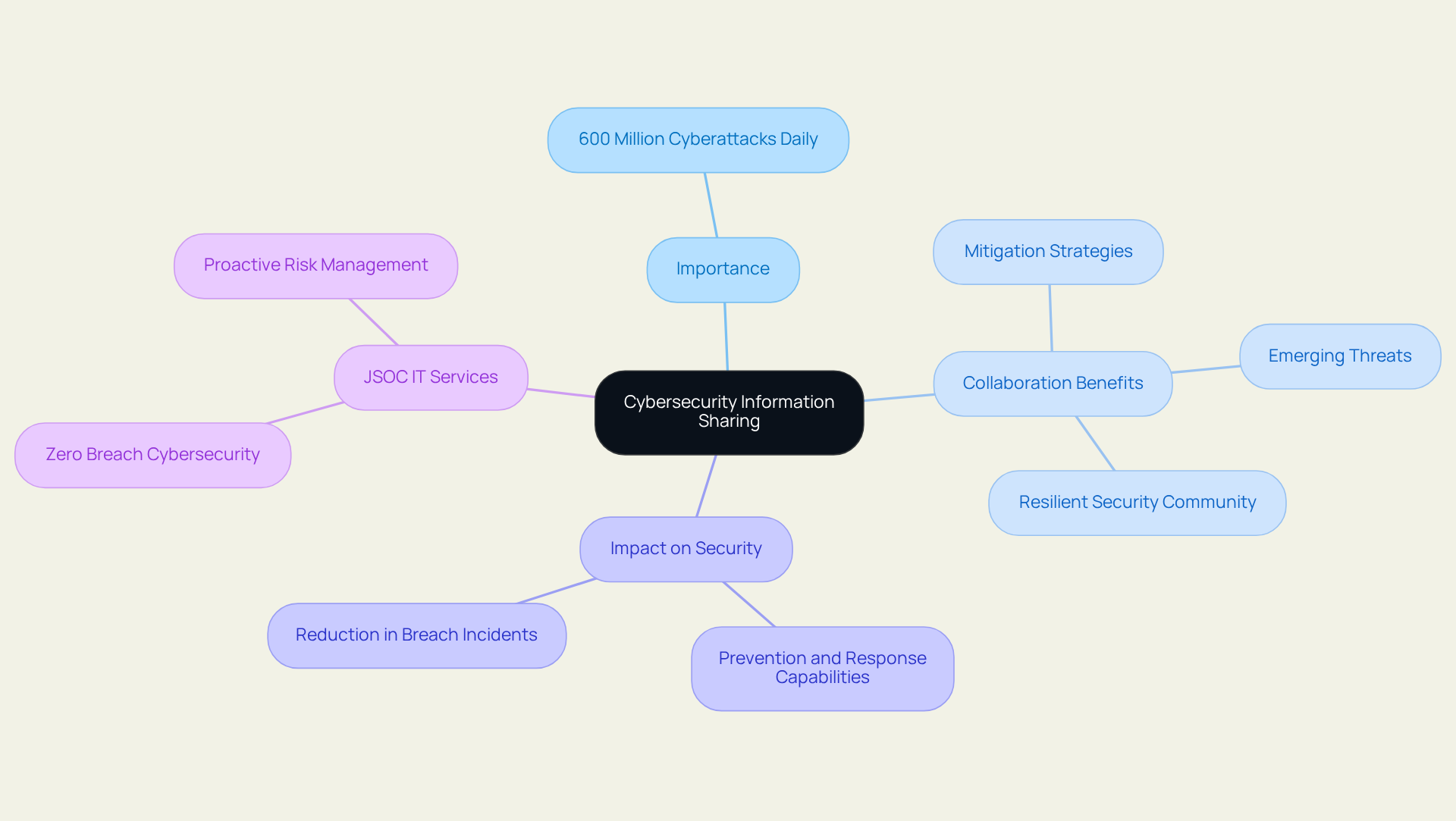
Cybersecurity Information Sharing: Enhancing Threat Intelligence
Cybersecurity information sharing is vital for a robust defense strategy. With approximately , collaboration among groups is essential to enhance understanding of the evolving risk landscape.
By forming partnerships with industry peers and engaging in information-sharing platforms, organizations can gain valuable insights into emerging threats and effective mitigation strategies. This collaborative approach not only fortifies individual entities but also cultivates a more resilient security community, empowering members to stay ahead of potential attacks.
The impact of risk intelligence sharing is significant, enhancing prevention and response capabilities, ultimately leading to a marked reduction in breach incidents.
At JSOC IT, we equip businesses with zero breach cybersecurity services that are integrated and customized to their specific requirements. Our proactive risk management strategies and commitment to client success exemplify how effective information sharing can yield transformative results in zero breach cybersecurity services.
As one client noted, 'JSOC IT's expertise in risk identification has significantly reduced our response time, allowing us to focus on growth initiatives.
Managed Security Services: Continuous Monitoring and Expert Support
Managed cybersecurity services (MSS) empower organizations by providing access to specialized expertise and continuous monitoring through zero breach cybersecurity services. By outsourcing protection management to specialized providers like JSOC IT, businesses benefit from zero breach cybersecurity services, which include:
- 24/7 threat monitoring
- Rapid incident response
- [Compliance support](https://huntress.com/blog/7-benefits-of-outsourcing-cybersecurity-services)
These are critical elements in today’s dynamic cyber landscape. JSOC IT’s flat-rate, high-touch service model eliminates hidden fees and endless license upsells, facilitating straightforward budgeting while delivering predictable, premium service. This model not only ensures consistent monthly costs but also highlights white-glove support, guaranteeing that clients receive personalized assistance that scales with their business needs.
MSS providers leverage advanced technologies and a team of skilled experts to bolster an organization’s protective posture with zero breach cybersecurity services, allowing internal teams to concentrate on core business activities. This strategic partnership enhances protective outcomes and simplifies the navigation of complex cybersecurity challenges. Organizations that have embraced MSS report marked improvements in incident response times and overall security confidence, showcasing the tangible benefits of this approach.
As cyber threats grow increasingly sophisticated, the proactive measures provided by MSS—particularly those aligned with HIPAA, HITRUST, and FDA standards—are vital for ensuring operational safety and compliance, especially in regulated sectors like healthcare and finance, where zero breach cybersecurity services are essential. Ultimately, this allows businesses to flourish in a .

Conclusion
The integration of zero breach cybersecurity strategies is not merely beneficial; it is essential for organizations committed to safeguarding their sensitive data and maintaining operational integrity. By adopting a comprehensive approach that encompasses real-time threat detection, incident response planning, and continuous employee training, businesses can effectively mitigate the risks associated with cyber threats. The focus on collaborative models, such as the 'Post-Security' framework, underscores the importance of embedding security measures into the very fabric of organizational operations.
Key strategies discussed include:
- The implementation of Zero Trust Architecture, which enforces strict access controls and identity verification.
- The necessity of regular software updates to proactively address vulnerabilities.
- Fostering a culture of cybersecurity awareness through employee training.
- Leveraging advanced threat detection tools to significantly enhance an organization's capacity to respond to incidents swiftly.
- Regular security audits to ensure compliance and identify potential weaknesses before they can be exploited.
Ultimately, the significance of adopting zero breach cybersecurity services cannot be overstated. As cyber threats continue to evolve, organizations must prioritize these strategies not only to protect their assets but also to cultivate resilience in an increasingly complex digital landscape. Embracing these comprehensive solutions will empower businesses to navigate the challenges of cybersecurity effectively, ensuring a secure environment conducive to growth and innovation.
Frequently Asked Questions
What is JSOC IT's 'Post-Security' model?
JSOC IT's 'Post-Security' model integrates IT operations, security measures, and compliance into a unified framework, allowing for real-time threat detection and response while dismantling traditional silos.
What services does JSOC IT offer?
JSOC IT offers a comprehensive range of services, including round-the-clock monitoring, automated remediation, and incident response, customized for industries like financial services and healthcare.
How does JSOC IT's pricing model work?
JSOC IT employs a flat-rate pricing model, ensuring predictable costs without hidden fees, which enhances budget management for clients.
Why are regular software updates important for cybersecurity?
Regular software updates are crucial for maintaining robust cybersecurity as they include security patches that address known vulnerabilities, preventing significant breaches.
What impact does unpatched software have on data breaches?
In 2025, unpatched software is responsible for 60% of data breaches globally, highlighting the importance of timely updates.
What is Zero Trust Architecture?
Zero Trust Architecture is a security model that operates on the principle of 'never trust, always verify,' requiring rigorous identity verification for every user and device seeking access to resources.
How does Zero Trust Architecture improve security?
It minimizes the attack surface through measures like micro-segmentation, least privilege access policies, and strict access control, which safeguards sensitive data and enhances compliance.
What are the benefits of adopting Zero Trust?
Organizations adopting Zero Trust have reported an 83% reduction in security incidents, demonstrating its effectiveness in enhancing overall security posture.
What role do automated updates play in cybersecurity?
Automated updates streamline the process of applying critical patches promptly, ensuring that vulnerabilities are addressed without manual intervention.
How does JSOC IT ensure compliance with industry regulations?
JSOC IT integrates cybersecurity updates and measures into a comprehensive strategy tailored to the unique challenges of different industries, helping maintain compliance with regulations like GDPR and HIPAA.