Overview
The article underscores the critical importance of integrated IT and security solutions in bolstering business resilience. It asserts that these comprehensive solutions—encompassing services such as:
- 24/7 monitoring
- incident response
- compliance advisory
empower organizations to safeguard their digital environments effectively. By streamlining operations, these solutions not only enhance overall security posture but also improve operational efficiency in the face of ever-evolving cyber threats.
Introduction
In an era where cyber threats are escalating at an unprecedented rate, businesses confront the formidable challenge of safeguarding their digital environments while pursuing growth. Integrated IT and security solutions emerge as a pivotal strategy, providing organizations with the opportunity to fortify their defenses and streamline operations simultaneously. Yet, with a plethora of options available, how can companies discern which integrated solutions truly enhance their resilience against evolving risks?
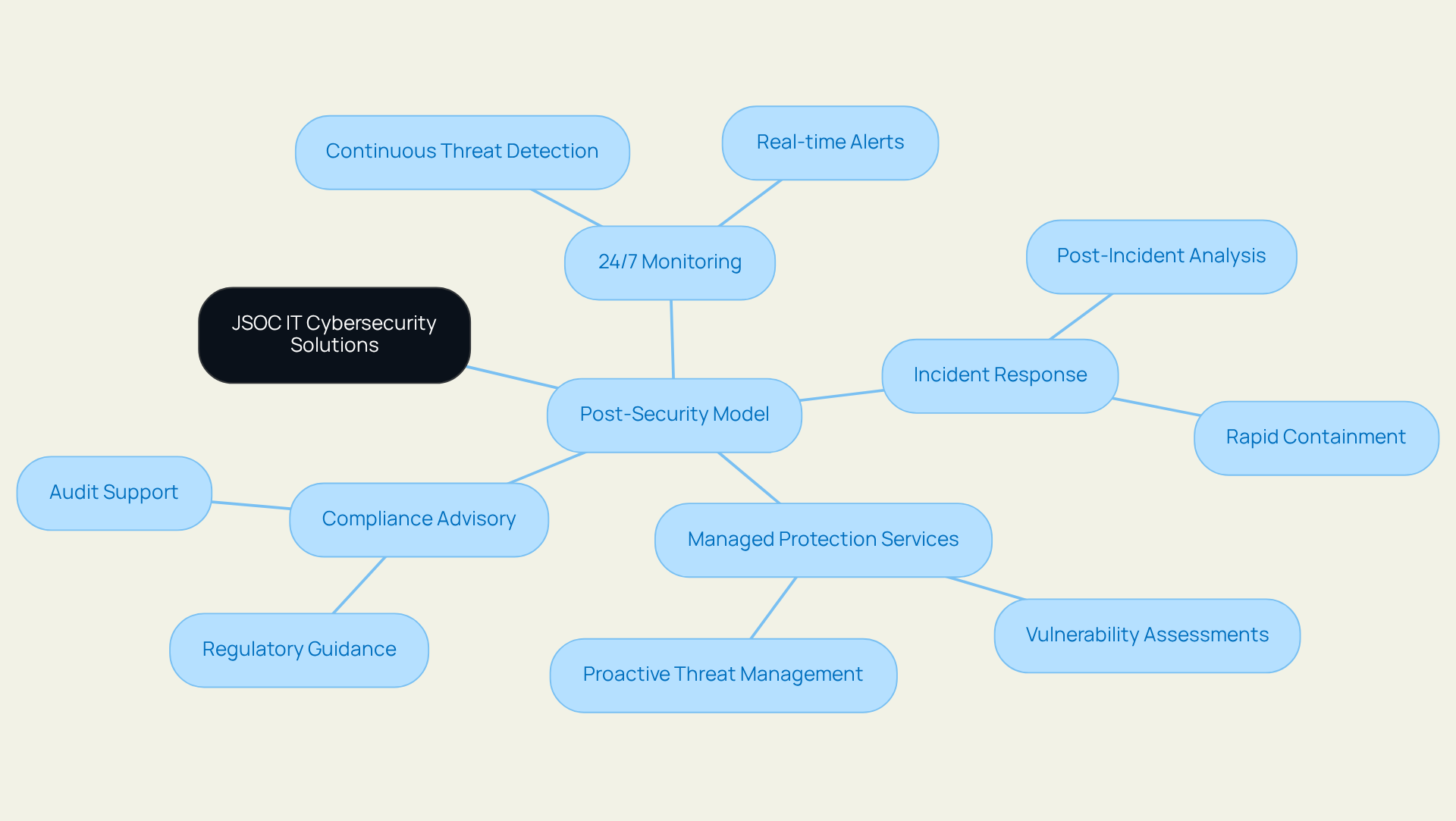
JSOC IT: Comprehensive Cybersecurity Solutions for Business Resilience
JSOC IT sets a benchmark in the cybersecurity landscape by providing a comprehensive suite of services designed to protect and optimize digital environments. Their groundbreaking 'Post-Security' model utilizes integrated IT and security solutions to combine IT operations, protective measures, and compliance into a cohesive framework, enabling businesses to scale with confidence while being safeguarded against potential breaches.
Key services include:
- 24/7 monitoring
- Incident response
- Managed protection services
- Compliance advisory
All meticulously tailored to address the unique challenges faced by sectors such as financial services and healthcare. This , incorporating integrated IT and security solutions, not only strengthens security but also streamlines processes, allowing organizations to concentrate on growth without compromising their safety posture.
Cybersecurity experts emphasize that a unified protective framework is essential for navigating today’s complex risk landscape, making IT's model an invaluable asset for companies aiming to enhance their resilience.
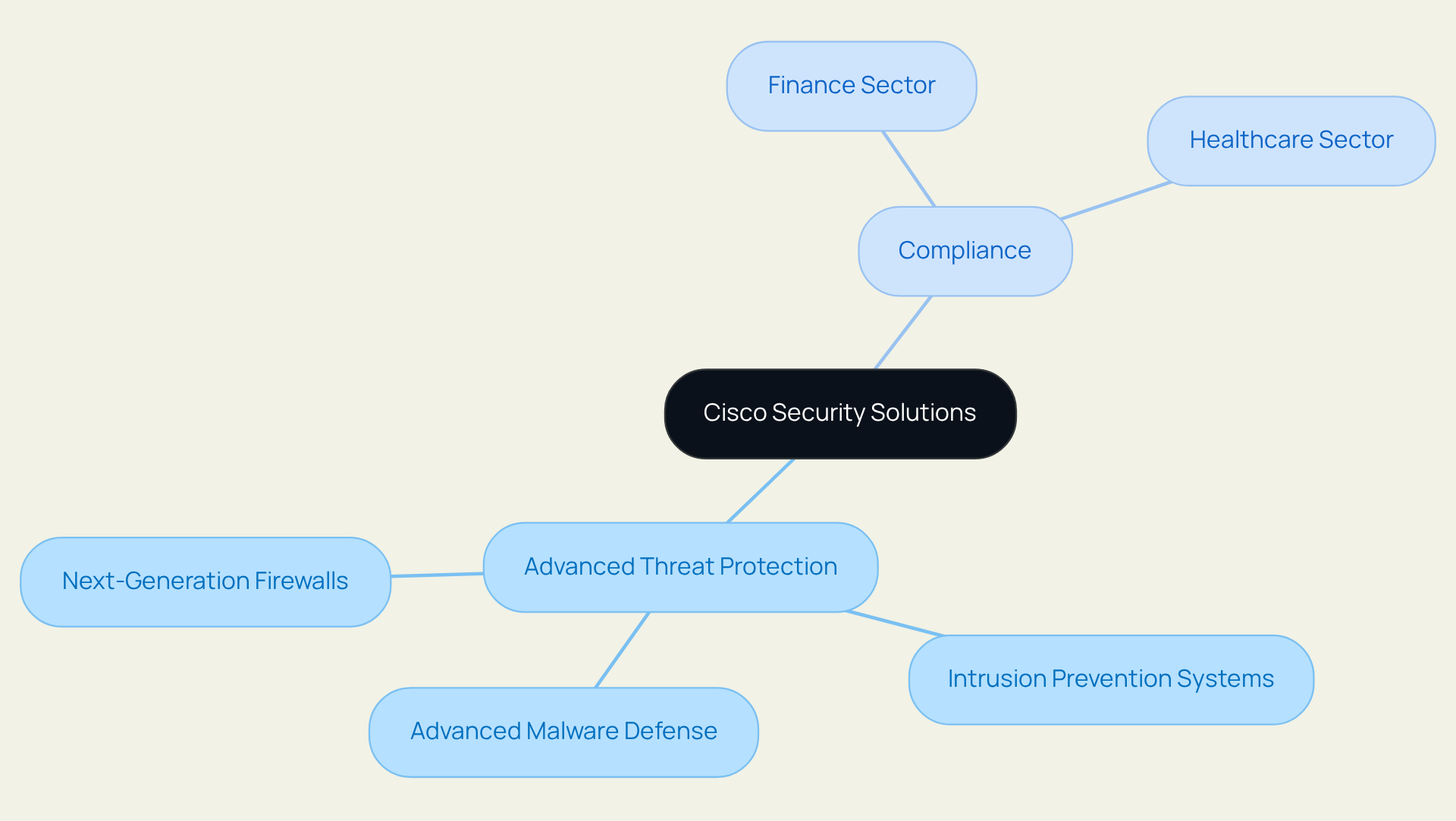
Cisco Security Solutions: Advanced Threat Protection and Compliance
The IT division delivers essential advanced risk protection and compliance features that are crucial for modern enterprises. Their comprehensive suite encompasses network protection measures, including next-generation firewalls, intrusion prevention systems, and advanced malware defense, all meticulously designed to identify and respond to threats in real-time.
Organizations leveraging integrated IT and security solutions have reported significant improvements in their protective posture, notably a marked reduction in incident response times. These solutions are especially beneficial for sectors such as finance and healthcare, where stringent regulatory requirements necessitate that facilitate adherence to legal standards.
Expert insights affirm that 'visibility is the foundation of any effective cybersecurity strategy,' emphasizing the critical role of the organization's technology in enhancing operational resilience. By utilizing JSOC IT's integrated IT and security solutions, businesses can substantially strengthen their protective stance while ensuring compliance with industry regulations, ultimately enhancing both operational resilience and trust.
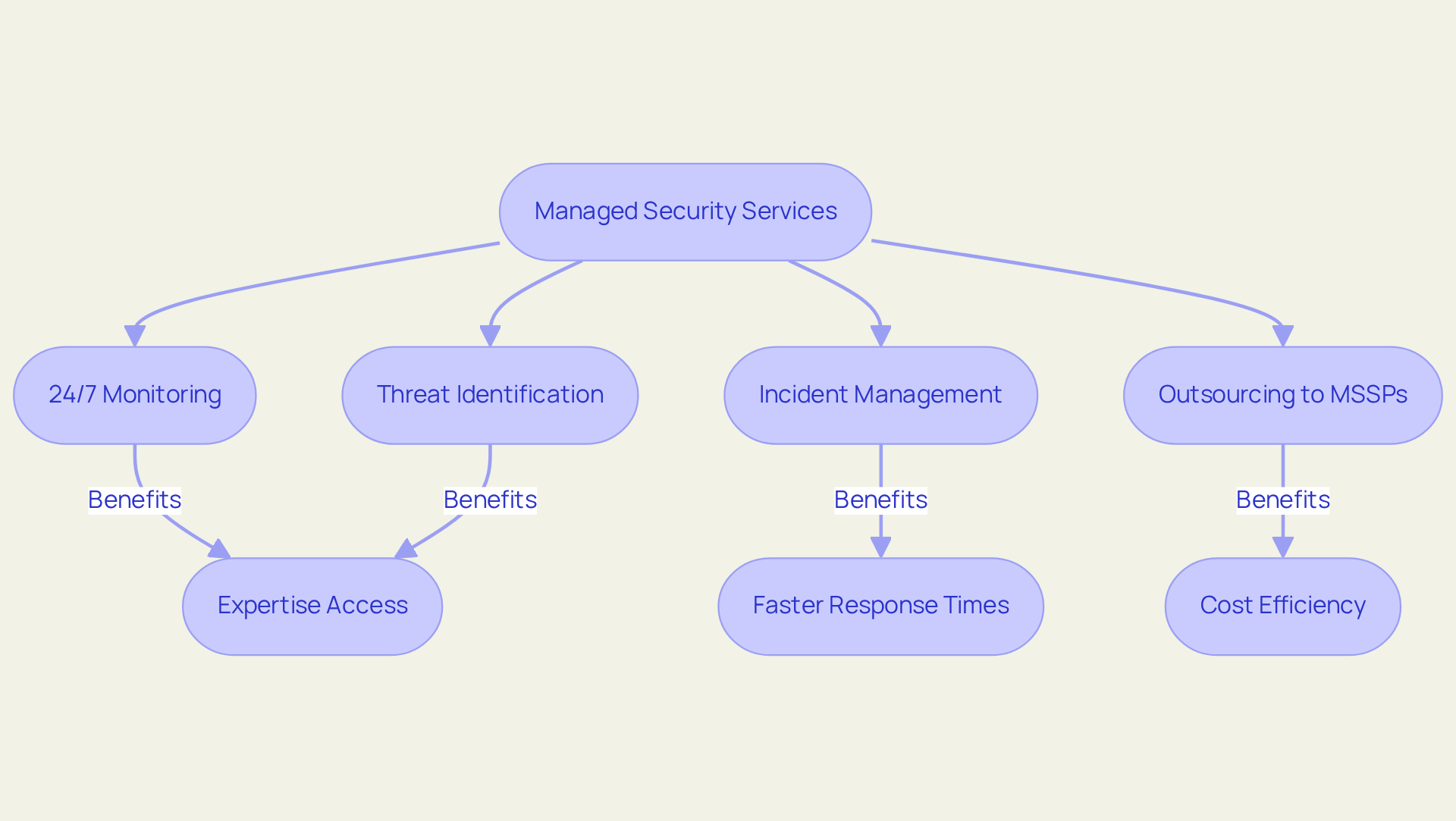
Integrated IT: Managed Security Services for Continuous Protection
Integrated IT and security solutions, especially those that incorporate managed safety services, deliver continuous defense against cyber risks. These services encompass 24/7 monitoring, threat identification, and incident management, enabling organizations to concentrate on their core operations without the burden of internal security oversight.
By outsourcing protection to specialized providers, businesses access extensive expertise and advanced tools that would otherwise be financially unfeasible to implement in-house. This strategy not only fortifies security but also significantly , ensuring that threats are swiftly identified and addressed.
A recent case study illustrates this point: an e-commerce company successfully thwarted a distributed denial-of-service (DDoS) attack through real-time monitoring, averting potential revenue loss and downtime.
As the cybersecurity landscape evolves, the trend of outsourcing protective services is on the rise, with organizations recognizing the critical need to collaborate with managed service providers (MSSPs) that provide integrated IT and security solutions to effectively tackle complex threats and compliance requirements.
Furthermore, grasping the policies and procedures outlined in user manuals is essential for ensuring effective monitoring and incident response.
Securitas: Integrated Security Solutions Combining Technology and Personnel
JSOC IT provides integrated IT and security solutions that expertly merge advanced technology with skilled personnel, offering businesses a comprehensive defense strategy. This multifaceted approach includes:
- Surveillance systems
- Access control
- On-site security staff
Ensuring that every aspect of security is meticulously addressed. By integrating these elements, organizations gain enhanced situational awareness and expedited response times during incidents. The IT department prioritizes confidentiality through restricted access to customer data and a robust data retention and disposal policy, ensuring that sensitive information is managed securely. Furthermore, the company's commitment to vulnerability and patch management significantly enhances overall cybersecurity resilience. The organization's integrated IT and security solutions comprise essential components such as:
- Strong authentication
- Encryption
- Access control policies
Which fortify defenses and optimize resource allocation. This strategic alignment empowers businesses to while maintaining compliance with industry standards.
IntelliSec: Expert Security Consulting for Tailored Solutions
JSOC IT stands at the forefront of expert consulting services, offering integrated IT and security solutions that are meticulously tailored to address the distinct needs of organizations. Their dedicated team conducts thorough evaluations to uncover weaknesses and devise protection plans that align with both business objectives and regulatory standards.
This emphasis on personalized solutions is vital for industries grappling with unique , such as healthcare and finance, where the stakes are particularly high. Organizations that have implemented customized protective measures have reported significant improvements in their overall safety posture, effectively mitigating risks associated with emerging cyber threats.
Insights from protection experts underscore the importance of regular vulnerability assessments and proactive risk reduction strategies, which are essential in today’s dynamic threat landscape. The IT department's commitment to enhancing compliance and data protection through integrated IT and security solutions, including encryption and access controls, empowers businesses to navigate the complexities of the current cybersecurity environment with confidence.
By adopting these tailored protective strategies, organizations not only bolster their resilience but also foster a culture of awareness throughout their workforce. Furthermore, the IT division offers a comprehensive suite of cybersecurity services, including threat detection and response, to further strengthen organizational protection.
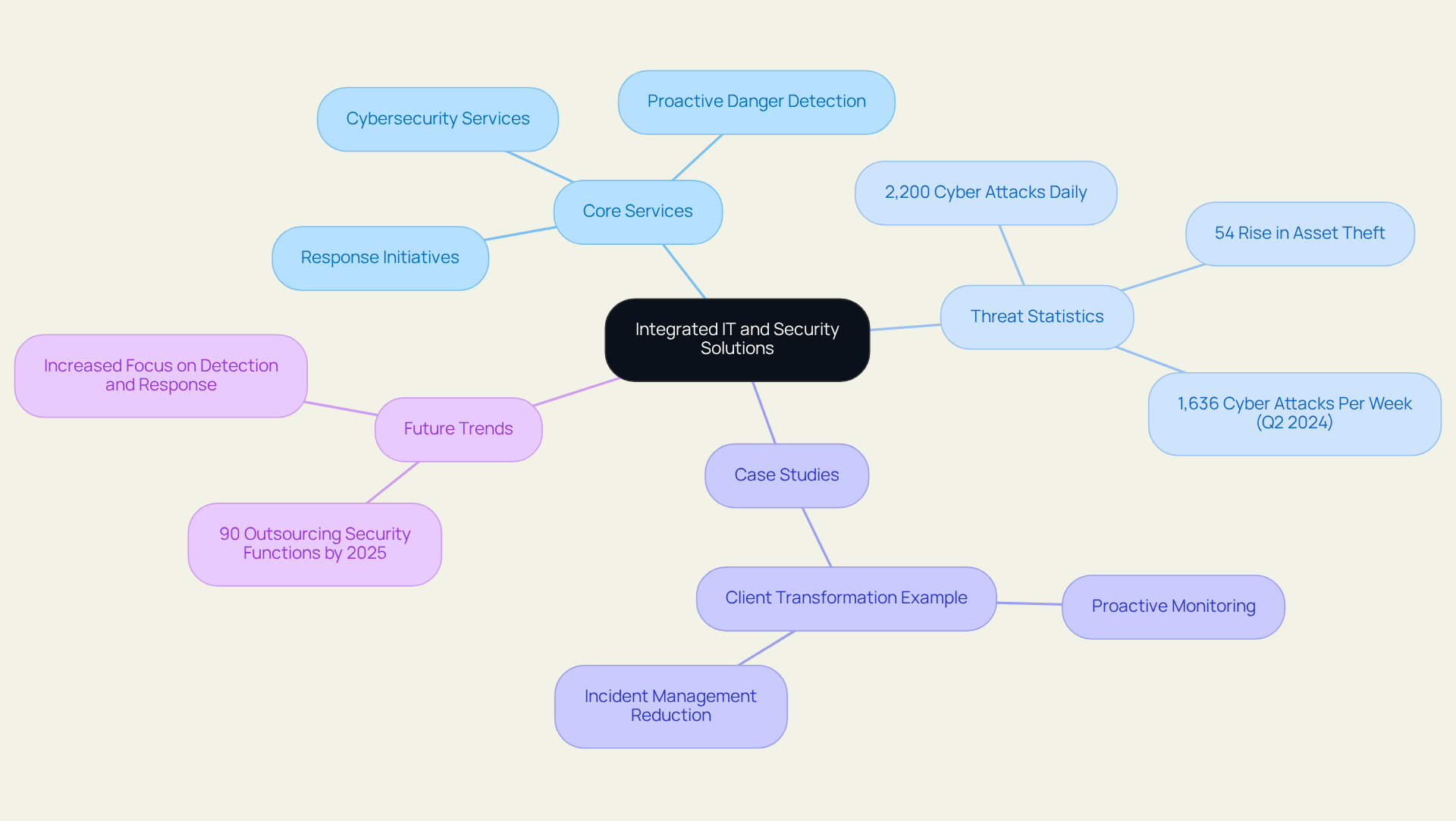
MTI Security: Asset Protection and Comprehensive Security Services
The IT division offers a robust suite of integrated IT and security solutions, including asset safeguarding and extensive protection services, meticulously designed to shield businesses from a myriad of threats. Their solutions, which are integrated IT and security solutions, encompass advanced cybersecurity services, proactive danger detection, and strategic response initiatives, all aimed at safeguarding both physical and digital assets. By seamlessly integrating these services, JSOC IT offers integrated IT and security solutions that empower organizations to formulate a comprehensive strategy adeptly addressing the complexities of today’s risk landscape.
This integrated approach, which encompasses integrated IT and security solutions, is increasingly crucial as businesses confront a surge in cyber threats, with over 2,200 cyber attacks occurring daily across the globe. In Q2 2024, organizations faced an average of 1,636 cyber attacks per week, reflecting a staggering 75% year-over-year increase. Such statistics underscore the urgent need for businesses to embrace integrated IT and security solutions that provide comprehensive protection strategies encompassing both physical and cyber realms.
Real-world examples vividly illustrate the efficacy of this holistic strategy. For instance, a client of JSOC IT transformed their protective stance overnight, significantly reducing incident management durations through proactive monitoring and swift action strategies. This exemplifies how integrated IT and security solutions can bolster operational efficiency and safety. Furthermore, with asset theft incidents rising by 54% in the past two years, companies are increasingly recognizing the imperative for integrated IT and security solutions that encompass both physical security and cybersecurity.
Current trends indicate that by 2025, a significant proportion of organizations will prioritize integrated IT and security solutions, with 90% of those seeking to outsource these functions focusing on detection and response capabilities. This shift signifies a growing awareness of the , making it essential for companies to implement integrated IT and security solutions that ensure resilience and operational continuity in an evolving risk environment. Additionally, JSOC IT’s flat-rate, high-touch support model guarantees that clients receive personalized assistance while absorbing tool licensing costs, further enhancing the value of their services.
Integrated Fire and Security Solutions: Comprehensive Safety Measures
Integrated fire and safety solutions present organizations with a comprehensive strategy for protection, effectively addressing both fire hazards and safety threats. By merging fire detection systems with advanced protective technologies, businesses can significantly enhance their safety posture. This integration facilitates , ensuring that incidents related to fire and safety are managed effectively.
Organizations that adopt this unified strategy experience improved safety outcomes, reduced risks, and a more resilient operational framework. As the landscape of threats continues to evolve, the implementation of comprehensive safety measures becomes increasingly essential for maintaining organizational integrity and safeguarding assets.
Real-world examples of businesses that have embraced unified fire and protection measures underscore the effectiveness of this approach in mitigating risks and enhancing overall safety.
OneC1: AI-Native Solutions for Enhanced IT Efficiency
The IT department delivers integrated IT and security solutions that significantly enhance both IT efficiency and security for businesses. By implementing essential cybersecurity controls—such as strict access management and data encryption strategies—the IT department guarantees the confidentiality and protection of sensitive information. Their proactive monitoring and rapid substantially reduce response times, allowing organizations to focus on their core operations without the constant worry of potential threats.
Furthermore, the IT Vulnerability and Patch Management Policy plays a crucial role in identifying and addressing vulnerabilities, ensuring that systems remain safeguarded against emerging threats. For example, the IT department has transformed the security posture of numerous clients, enabling them to effortlessly meet compliance standards while adapting to evolving security needs.
As organizations increasingly prioritize robust cybersecurity measures, integrated IT and security solutions like those offered by this IT group are essential for maintaining a competitive edge in the cybersecurity landscape. Industry leaders underscore the importance of investing in integrated IT and security solutions that facilitate autonomous operations and enhance overall resilience against cyber risks.
ISSI Solutions: Collaborative Decision-Making for Enhanced Security
JSOC IT underscores collaborative decision-making as an essential component of enhanced safety. By fostering collaboration among protection professionals, organizations can significantly improve their response to threats and refine operational procedures. Collaborative methods facilitate the exchange of insights and best practices, leading to more effective protection strategies. This is particularly crucial in complex environments where diverse stakeholders must unite to efficiently address challenges.
As we approach 2025, the imperative to bolster cybersecurity through teamwork is accentuated by the alarming statistic that global cybercrime losses reached $10.5 trillion annually in 2024. This stark reality highlights the urgent need for organizations to implement proactive measures, such as those provided by JSOC IT, to protect their assets. Initiatives like NATO's Cyber Coalition, which trained 5,000 specialists across 30 nations, exemplify the proactive strategies organizations are adopting to prepare for real-world cyber threats while nurturing a collaborative culture essential for overcoming intricate safety challenges.
Insights from protection experts further stress the significance of collaboration in countering threats. Daniel Gumucio, CEO & Founder of AssureSoft, asserts that effective collaboration is vital for real-time insights, emphasizing that organizations must synchronize their engineering, compliance, and business teams to adeptly manage security risks. This unified approach ensures that all participants remain informed and engaged, resulting in quicker and more accurate responses to incidents.
The organization's dedication to delivering customized integrated IT and security solutions bolsters this collaborative framework. Their proactive monitoring and rapid incident response strategies empower organizations to confront risks in real time, substantially mitigating potential damage and downtime. By working closely with clients, JSOC IT ensures that their specific protective needs are met, fostering a culture of shared responsibility that enhances overall resilience against cyber threats.
The benefits of collaboration extend beyond immediate risk mitigation. Organizations embracing collaborative practices frequently observe improved morale and a stronger commitment to safety. By working together, teams can leverage diverse perspectives and expertise, leading to innovative solutions that bolster overall resilience against cyber risks.
As the cybersecurity landscape continues to evolve, the demand for effective collaboration among protection professionals will only intensify. By investing in collaborative frameworks and promoting a culture of shared responsibility, organizations can adeptly navigate the complexities of contemporary cyber challenges and cultivate a more secure digital environment with integrated IT and security solutions.
Integrated Security Corporation: Streamlined Security Operations for Businesses
JSOC IT delivers streamlined operations that empower businesses to effectively respond to emerging threats. Their centralized management systems integrate various protective functions, enabling real-time monitoring and rapid incident handling. This integration not only but also enhances the overall safety posture of organizations, significantly reducing the time required to address incidents.
Clients have reported that JSOC IT swiftly transformed their protective stance, drastically decreasing incident handling durations through proactive monitoring and rapid reaction strategies. Organizations that implement these systems typically experience substantial reductions in incidents, demonstrating the tangible benefits of a coordinated protection strategy.
As Alex Mosher, President and CRO at Armis, states, 'The integrated solution allows organizations to transition from reactive to proactive risk management by automating workflow actions and policy implementation at scale.'
In today's fast-paced business environment, where prompt risk management is critical, the effectiveness achieved through centralized oversight is essential for maintaining resilience. Furthermore, as companies navigate the complexities of cybersecurity in 2025, adopting integrated IT and security solutions from JSOC IT becomes increasingly vital for safeguarding their operations.
Their comprehensive services, including threat detection and response, managed security services, and expert security consulting, ensure that organizations can concentrate on growth initiatives while feeling secure in their compliance and security measures.
Conclusion
In a rapidly evolving digital landscape, the necessity for integrated IT and security solutions has never been more pronounced. By adopting a holistic approach that combines advanced technology, expert consulting, and collaborative strategies, businesses can significantly enhance their resilience against an array of cyber threats. This integration not only fortifies security measures but also streamlines operations, allowing organizations to focus on growth while maintaining a robust safety posture.
Throughout the discussion, key solutions such as those offered by JSOC IT, Cisco, and other industry leaders have been highlighted for their effectiveness in addressing unique business challenges. From comprehensive cybersecurity services and managed security offerings to tailored consulting and collaborative frameworks, these approaches empower organizations to navigate the complexities of compliance and risk management. The emphasis on 24/7 monitoring, incident response, and proactive threat detection underscores the importance of continuous protection in safeguarding both physical and digital assets.
As businesses look toward the future, embracing integrated IT and security solutions is essential for maintaining a competitive edge and ensuring operational continuity. Organizations are encouraged to invest in these comprehensive strategies, fostering a culture of awareness and collaboration that enhances overall security. By prioritizing integrated approaches, businesses can effectively mitigate risks, adapt to emerging threats, and cultivate a resilient environment that supports long-term success.
Frequently Asked Questions
What is JSOC IT and what services do they provide?
JSOC IT is a cybersecurity provider that offers a comprehensive suite of services designed to protect and optimize digital environments. Their key services include 24/7 monitoring, incident response, managed protection services, and compliance advisory.
How does the 'Post-Security' model work?
The 'Post-Security' model integrates IT operations, protective measures, and compliance into a cohesive framework, allowing businesses to scale confidently while being safeguarded against potential breaches.
Which sectors benefit most from JSOC IT's services?
JSOC IT's services are particularly tailored to address the unique challenges faced by sectors such as financial services and healthcare.
What are the benefits of using integrated IT and security solutions?
Integrated IT and security solutions strengthen security, streamline processes, and allow organizations to focus on growth without compromising their safety posture.
What advanced features do Cisco Security Solutions offer?
Cisco Security Solutions provide advanced risk protection features, including next-generation firewalls, intrusion prevention systems, and advanced malware defense, designed to identify and respond to threats in real-time.
How do integrated IT and security solutions improve incident response times?
Organizations leveraging these solutions have reported significant improvements in their protective posture, notably a marked reduction in incident response times, which is crucial for sectors with stringent regulatory requirements.
What role does visibility play in cybersecurity strategy?
Visibility is considered the foundation of any effective cybersecurity strategy, as it enhances operational resilience and helps organizations identify and address threats more effectively.
What are managed security services and how do they benefit organizations?
Managed security services provide continuous defense against cyber risks, including 24/7 monitoring, threat identification, and incident management, allowing organizations to focus on core operations without internal security burdens.
How does outsourcing security services impact incident response?
By outsourcing security to specialized providers, businesses gain access to extensive expertise and advanced tools, which significantly enhances incident response times and ensures swift threat identification and resolution.
Why is collaboration with managed service providers (MSSPs) becoming more important?
As the cybersecurity landscape evolves, organizations recognize the critical need to collaborate with MSSPs to effectively tackle complex threats and compliance requirements, leading to improved security and operational resilience.