Overview
The article emphasizes critical cybersecurity risk management strategies for Chief Information Security Officers (CISOs) to safeguard sensitive data and ensure compliance. It underscores essential approaches, such as:
- Integrating risk management into enterprise frameworks
- Implementing the NIST Cybersecurity Framework
- Prioritizing continuous monitoring alongside employee training
Collectively, these strategies significantly bolster an organization's resilience against cyber threats.
Introduction
In an era marked by the rapid evolution of cyber threats, organizations are confronted with the formidable challenge of protecting sensitive data while adhering to regulatory standards. Chief Information Security Officers (CISOs) face the dual task of not only deploying effective cybersecurity measures but also seamlessly integrating these strategies into the overarching business framework.
This article delves into ten essential cybersecurity risk management strategies that empower CISOs to adeptly navigate the complexities of today's digital landscape, bolster their organization’s resilience, and safeguard against potential breaches.
How can CISOs strategically align their security initiatives with business objectives while adeptly managing the persistent risks posed by cyberattacks?
JSOC IT: Integrated Cybersecurity Solutions for Risk Management
JSOC IT's 'Post-Security' model revolutionizes cybersecurity by seamlessly integrating IT operations, protective measures, and compliance into a unified framework. This holistic approach incorporates cybersecurity risk management strategies that dismantle traditional silos, empowering entities to scale confidently while maintaining robust defenses against breaches.
By embedding their services directly within client teams, JSOC IT significantly enhances incident response times—reducing them from an average of 322 days with legacy systems to mere seconds with AI-driven tools. This integration not only boosts security confidence but also positions JSOC IT as a in regulated sectors such as financial services and healthcare.
The model's success is evidenced by substantial advancements in compliance readiness and operational resilience, establishing it as a cornerstone for organizations navigating the complexities of today's digital security environment with effective cybersecurity risk management strategies. Key features, such as the Data Retention and Disposal Policy and Vulnerability and Patch Management Policy, further enhance confidentiality and data protection.
As Sam Sawalhi, Founder & CEO, emphasizes, 'We’ve proven that integrating deeply with our clients — rather than selling them another tool — is the path forward.'
For CISOs, implementing cybersecurity risk management strategies is essential for protecting sensitive data and ensuring compliance.

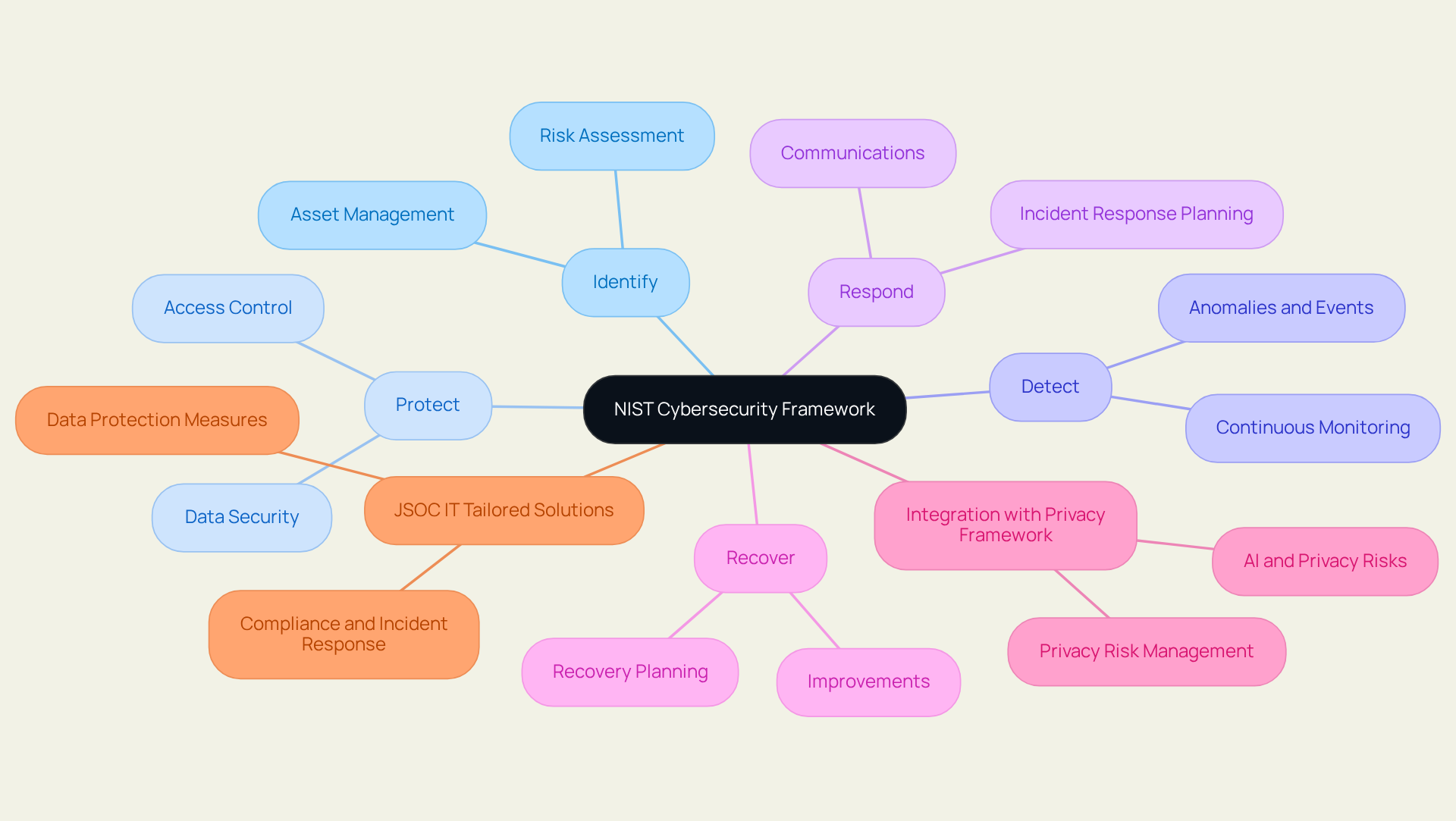
NIST Cybersecurity Framework: A Structured Approach to Risk Management
The NIST Cybersecurity Framework offers a robust structure for managing cybersecurity risks, comprising five essential functions: Identify, Protect, Detect, Respond, and Recover. By implementing this framework, organizations can craft comprehensive cybersecurity risk management strategies that align with their business objectives and fulfill regulatory requirements. This systematic approach empowers Chief Information Security Officers (CISOs) to effectively prioritize resources within their , thereby enhancing their entity's resilience against evolving cyber threats.
Furthermore, the integration of the framework with the updated Privacy Framework allows organizations to implement cybersecurity risk management strategies that effectively address both privacy and security risks in a cohesive manner, significantly improving overall risk management effectiveness.
JSOC IT amplifies this framework by providing tailored cybersecurity solutions, including advanced data protection measures such as encryption and stringent access controls, which guarantee compliance and effective incident response. Their commitment to serving sectors like finance and healthcare enables organizations to protect sensitive information while maintaining operational excellence.
ISO 27001: Establishing an Information Security Management System
ISO 27001 offers a robust framework for establishing, implementing, maintaining, and continually enhancing an Information Security Management System (ISMS). By adhering to this standard, organizations can systematically manage sensitive information, ensuring its confidentiality, integrity, and availability. As of 2022, around 60% of companies within the Electronic and Electrical Equipment sector have attained ISO 27001 certification, underscoring its escalating significance across various industries.
Achieving ISO 27001 certification signifies a profound commitment to information protection, fostering trust among clients and stakeholders. This certification correlates with an enhanced corporate reputation and improved financial performance, as organizations that embrace often demonstrate superior compliance with regulations, including HIPAA, HITRUST, and FDA standards, alongside diminished operational risks.
Numerous success stories illustrate the advantages of ISO 27001 certification. For instance, Luma Health has fortified its data protection measures by implementing this standard, ensuring compliance with HIPAA regulations and bolstering trust among its healthcare clients. Similarly, JSOC IT has transformed its clients' protective measures, significantly reducing incident response times and allowing organizations to focus on their core business activities without the persistent worry of potential threats. Their proactive monitoring and swift response strategies have been instrumental in assisting clients in effortlessly meeting compliance standards, highlighting the essential role of ISO 27001 in comprehensive cybersecurity risk management strategies.
Experts emphasize that aligning an ISMS with ISO 27001 is vital for organizations aiming to mitigate risks through effective cybersecurity risk management strategies and enhance their protective posture. Dr. Damla Durak Usar asserts, "Compliance with these standards can lead to increased legitimacy and reputation, which can enhance corporate financial performance." The standard not only offers a structured approach to managing information security but also aligns with broader organizational objectives, establishing it as a crucial element of any holistic cybersecurity risk management strategies.

Risk Assessment Process: Identifying and Prioritizing Cybersecurity Risks
The risk assessment procedure stands as a cornerstone of effective digital security management. It encompasses the identification of assets, evaluation of potential threats, and analysis of the likelihood and impact of various risks. This structured approach empowers organizations to prioritize their by focusing on the most critical vulnerabilities. Regular risk assessments not only enable CISOs to align protective measures with the ever-evolving threat landscape but also ensure that organizational objectives are met.
As cyber threats continue to advance, organizations that implement systematic evaluations can optimize resource allocation, bolster their security posture, and uphold compliance with regulatory standards by adopting cybersecurity risk management strategies. This proactive strategy is vital for mitigating risks and safeguarding sensitive information, ultimately fostering a culture of awareness regarding online security throughout the organization.

Incident Response Plan: Preparing for Cybersecurity Incidents
An effective incident response plan delineates the procedures for detecting, responding to, and recovering from incidents, which are integral to cybersecurity risk management strategies. This plan must encompass clearly defined , communication protocols, and systematic steps for containment and recovery. By consistently evaluating and revising the incident response plan, organizations can ensure a prompt and efficient reaction, thereby minimizing harm and facilitating a swift return to standard operations.
For instance, organizations that conduct regular tabletop exercises can identify weaknesses in their plans, which enables them to refine their strategies and enhance overall preparedness. Furthermore, integrating proactive risk detection and continuous surveillance into the incident response framework is essential for recognizing unusual network activity and addressing potential issues before they escalate.
Additionally, the implementation of secure development policies and integrated change management practices is vital for sustaining business continuity and disaster recovery. By adopting cybersecurity risk management strategies, such as prioritizing patch management for critical vulnerabilities and conducting post-incident evaluations, organizations can significantly bolster their security posture and resilience against evolving threats.

Continuous Monitoring: Real-Time Threat Detection
Continuous monitoring stands as a pivotal element of contemporary cybersecurity strategies, characterized by the ongoing evaluation of a company's security posture through automated tools and processes. This proactive approach empowers organizations to utilize to identify anomalies and potential threats in real-time, facilitating prompt response actions. In 2024, cyberattack volumes surged by 114%, underscoring the imperative for organizations to adopt robust cybersecurity risk management strategies to effectively stay ahead of emerging threats. By integrating continuous observation into their security framework, Chief Information Security Officers (CISOs) can significantly enhance their organization's resilience, thereby reducing the likelihood of successful cyberattacks.
Real-time risk detection methods are indispensable for effective cybersecurity risk management strategies, enabling swift recognition and management of threats, ensuring that organizations can respond effectively before damage occurs. Security specialists emphasize that the ability to identify and respond to threats within 30 days can save organizations over $1 million compared to those that take longer. As we look toward 2025, the focus on cybersecurity risk management strategies for real-time threat detection will only intensify, driven by the increasing complexity of cyber threats and the necessity for organizations to maintain a proactive defense posture.

Employee Training: Cultivating Cybersecurity Awareness
Ongoing employee training on cybersecurity best practices is essential for cultivating a security-conscious culture that supports effective cybersecurity risk management strategies within organizations. Training programs must encompass critical topics such as:
- Phishing awareness
- Password protection
- Safe browsing habits
With phishing attacks surging by 1,200%, equipping employees with the necessary knowledge and skills is paramount to significantly mitigate the risk of human errors, which often serve as a primary cause of breaches. Current best practices underscore the necessity for tailored training that addresses specific vulnerabilities across various industries, ensuring that all employees, from front-line staff to executives, comprehend their role in upholding security.
Moreover, organizations are increasingly adopting interactive training techniques, including simulated phishing exercises, which have proven effective in enhancing engagement and information retention. As cyber risks continue to evolve, training programs must adapt by integrating cybersecurity risk management strategies, along with the latest trends and technologies, to keep employees informed and vigilant. As noted, "employees can serve as a strong line of defence against attacks but only when equipped with the proper knowledge." This proactive approach not only fortifies the entity's defensive posture but also fosters a culture of awareness and accountability among all employees.
Furthermore, with over 80% of companies implementing current awareness training programs, it is imperative for CISOs to persistently refine these initiatives to adapt to the shifting threat landscape.

Regular Testing and Updates: Strengthening Security Posture
Routine protective testing, including vulnerability evaluations and penetration assessments, is imperative for identifying vulnerabilities within a company's defenses. In 2025, the cybersecurity landscape is continuously evolving, with 67% of U.S. enterprises reporting a breach in the past 24 months, highlighting the urgent necessity for proactive measures. not only identify potential access points for attackers but also enable organizations to prioritize their protective measures effectively.
Current trends reveal an increasing dependence on automated tools for vulnerability assessments, with over half of enterprises now employing software-based pentesting solutions. This shift signifies a growing acknowledgment of the need for ongoing testing to adapt to the swiftly changing threat environment. As cybersecurity professionals assert, regular penetration testing provides real-world validation of protective measures, affirming their efficacy against potential attacks.
Moreover, keeping software and systems updated with the latest patches is crucial for mitigating known vulnerabilities. The updated NIST catalog underscores the significance of monitoring components during updates to ensure their security within the overall system. Organizations are encouraged to conduct penetration tests every three months, especially those managing high-risk assets, to maintain a robust protective posture.
In conjunction with these practices, adopting comprehensive policies such as the Vulnerability and Patch Management Policy, the Incident Response Plan, and the Risk Assessment and Treatment Policy can significantly enhance a company's security framework. Continuous oversight of protective measures and learning from past incidents are vital for preparedness against emerging threats.
By prioritizing regular testing and updates, alongside a robust set of integrated security policies, organizations can substantially reduce the likelihood of successful cyberattacks, thereby safeguarding sensitive data and preserving customer trust. As the threat landscape continues to evolve, integrating these practices into the protective strategy is not merely beneficial but essential for long-term resilience.

Integration with Enterprise Risk Management: Aligning Security with Business Goals
Incorporating cybersecurity risk management strategies into the broader enterprise risk management framework is not merely advisable; it is essential for any robust business strategy. This alignment ensures that protective measures are not only in place but actively support organizational objectives, thereby enhancing informed decision-making across the enterprise.
By clearly demonstrating how security initiatives bolster overall business resilience, Chief Information Security Officers (CISOs) can effectively advocate for the necessary resources and backing from leadership. Current trends indicate that organizations increasingly recognize the imperative for cybersecurity risk management strategies to safeguard their assets, transitioning from outdated systems to integrated platforms that facilitate this essential integration.
As industry experts assert, a business-aligned CISO can convert cybersecurity into a competitive advantage, fostering innovation while safeguarding critical assets. This strategic alignment cultivates a culture of commitment within organizations, ultimately leading to and increased support for safety initiatives.
JSOC IT exemplifies this strategic approach, having successfully transformed the security posture of numerous clients through customized solutions that incorporate cybersecurity risk management strategies to address specific compliance and risk management needs. Their proactive risk detection and response strategies not only enhance protection but also enable organizations to focus on growth initiatives, illustrating how integrated digital safety solutions can align with enterprise goals while ensuring compliance with industry standards.

Automation Tools: Enhancing Cybersecurity Risk Management Efficiency
Automation tools are essential for enhancing security risk management by streamlining critical tasks such as threat detection, incident response, and compliance reporting. Organizations that adopt automation can markedly improve their operational efficiency, enabling security teams to focus on strategic initiatives rather than monotonous processes. For example, automated systems can cut down the time required for manual tasks from days to mere seconds, effectively reducing human error rates by 18% to 40% for complex operations. This transformation not only accelerates response times but also cultivates a proactive approach to implementing .
Current trends indicate that entities with higher levels of automation are six times more likely to experience a data breach within 24 hours, which underscores the need for effective cybersecurity risk management strategies in real-time risk management. Furthermore, automation enhances the accuracy of threat identification, allowing response teams to address incidents 50% faster. By integrating automation into their cybersecurity risk management strategies, organizations can achieve significant cost savings and enhance compliance with industry standards, including NIST and HIPAA.
JSOC IT's robust security framework prioritizes confidentiality, vulnerability management, and stringent data retention and disposal policies, ensuring that organizations not only safeguard sensitive information but also uphold compliance with regulatory standards. Client testimonials highlight that JSOC IT's automation solutions have transformed protective strategies, enabling businesses to adapt swiftly to the evolving risk landscape. As cybercrime is projected to cost the globe $10.5 trillion annually by 2025, the demand for robust, automated protective measures has never been more critical. By harnessing advanced automation tools, organizations can fortify their security posture and ensure they are well-prepared to navigate the complexities of modern cyber threats. Kenility asserts that "Cybersecurity automation is no longer optional—it’s the backbone of resilience in 2025," reinforcing the vital role of automation in today’s cybersecurity environment.

Conclusion
Implementing effective cybersecurity risk management strategies is crucial for Chief Information Security Officers (CISOs) who aim to safeguard sensitive data and ensure compliance in an increasingly complex digital landscape. This article underscores a range of essential approaches, from integrating cybersecurity into enterprise risk management frameworks to leveraging automation tools that enhance operational efficiency. By adopting these strategies, organizations can fortify their defenses and maintain resilience against evolving cyber threats.
Key insights discussed emphasize the importance of frameworks like NIST and ISO 27001, which provide structured methodologies for managing risks and ensuring compliance. The significance of continuous monitoring, regular testing, and employee training in cultivating a security-aware culture is paramount. Furthermore, the integration of advanced technologies and automation into cybersecurity practices empowers organizations to respond more swiftly to incidents and reduce the likelihood of breaches.
In a world where cyber threats are ever-present and continuously evolving, the commitment to robust cybersecurity risk management strategies is not merely a best practice but a necessity. Organizations must prioritize these strategies to protect their assets, build stakeholder trust, and ultimately drive business success. By embracing a proactive approach to cybersecurity, CISOs can transform their organizations into resilient entities capable of navigating the complexities of the digital age.
Frequently Asked Questions
What is the 'Post-Security' model by JSOC IT?
The 'Post-Security' model by JSOC IT integrates IT operations, protective measures, and compliance into a unified framework, enhancing cybersecurity risk management by breaking down traditional silos.
How does JSOC IT improve incident response times?
JSOC IT reduces incident response times from an average of 322 days with legacy systems to mere seconds by embedding their services within client teams and utilizing AI-driven tools.
What sectors benefit from JSOC IT's services?
JSOC IT primarily serves regulated sectors such as financial services and healthcare, enhancing their cybersecurity posture and compliance readiness.
What are the key features of JSOC IT's cybersecurity approach?
Key features include the Data Retention and Disposal Policy and Vulnerability and Patch Management Policy, which enhance confidentiality and data protection.
What does the NIST Cybersecurity Framework encompass?
The NIST Cybersecurity Framework includes five essential functions: Identify, Protect, Detect, Respond, and Recover, providing a structured approach to managing cybersecurity risks.
How does the NIST Cybersecurity Framework benefit organizations?
It helps organizations align their cybersecurity risk management strategies with business objectives and regulatory requirements, enhancing resilience against cyber threats.
What is ISO 27001 and its significance?
ISO 27001 is a framework for establishing, implementing, maintaining, and enhancing an Information Security Management System (ISMS), ensuring the confidentiality, integrity, and availability of sensitive information.
What are the benefits of achieving ISO 27001 certification?
Achieving ISO 27001 certification signifies a commitment to information protection, enhances corporate reputation, improves financial performance, and demonstrates superior compliance with regulations.
How has ISO 27001 certification helped organizations like Luma Health?
Luma Health has strengthened its data protection measures and ensured compliance with HIPAA regulations, thereby bolstering trust among its healthcare clients through ISO 27001 certification.
Why is aligning an ISMS with ISO 27001 important?
Aligning an ISMS with ISO 27001 is vital for organizations to effectively mitigate risks, enhance their protective posture, and improve compliance with regulatory standards.