Overview
The article presents an authoritative five-step process for businesses to effectively procure cybersecurity solutions. It underscores the critical need for:
- Assessing cybersecurity requirements
- Conducting thorough research on available solutions
- Evaluating potential vendors
- Grasping pricing structures
- Planning for implementation
This structured approach is essential for organizations to select the appropriate tools necessary to safeguard against the ever-evolving landscape of cyber threats.
Introduction
In an increasingly digital world, the stakes of cybersecurity are at an all-time high. Businesses now confront a dynamic landscape of threats that could result in catastrophic breaches and significant financial losses. It is essential for organizations to understand how to effectively procure cybersecurity solutions to safeguard their sensitive data and uphold operational integrity. Yet, with a plethora of options available, how can businesses ensure they select the right solutions that align with their specific needs and budget?
This guide offers a structured approach to navigating the intricate process of acquiring cybersecurity solutions, empowering organizations to make informed decisions and fortify their defenses against cyber threats.
Assess Your Business Cybersecurity Needs
- Identify Critical Assets: Begin by cataloging all essential business assets, including sensitive data, applications, and infrastructure. Recognizing what needs safeguarding is crucial, as the repercussions of a security breach can be severe, potentially leading to significant financial losses and reputational damage. In 2025, organizations reported that breaches could cost upwards of millions, underscoring the necessity for proactive measures.
- Conduct a Risk Assessment: Assess the risks associated with each identified asset. Evaluate factors such as the likelihood of a cyber attack and the potential consequences of a breach. This step is vital; organizations that fail to recognize vulnerabilities may face dire repercussions, including operational disruptions and regulatory penalties. Leveraging JSOC IT's expert security consulting can significantly enhance this assessment process.
- Engage Stakeholders: Involve key stakeholders from various departments to gather insights on their specific security concerns and requirements. This collaborative approach fosters a comprehensive understanding of the organization's needs, ensuring that all essential perspectives are integrated into the security strategy. JSOC IT's tailored strategies can facilitate this engagement effectively.
- Review Compliance Requirements: Identify any industry-specific regulations your business must adhere to, such as HIPAA for healthcare or PCI DSS for financial services. Understanding these will guide your protective strategy and option selection, especially when you buy cybersecurity solutions for businesses, aiding in mitigating legal risks and bolstering your overall safety posture. Integrating embedded SOC and GRC operations can further support compliance efforts.
- Document Findings: Compile a detailed report summarizing your findings, which will serve as a reference throughout the purchasing process. This documentation is essential for tracking progress and ensuring that all identified risks and compliance needs are effectively addressed. Regular reviews of this documentation can also assist in adapting to evolving threats and regulatory changes, ensuring continuous protection.

Research Available Cybersecurity Solutions
- Explore Different Types of Solutions: Familiarize yourself with a variety of protective solutions, including firewalls, intrusion detection systems, endpoint protection, and managed defense services. Each type plays a crucial role in safeguarding your digital environment against evolving threats. At JSOC IT, we implement advanced security measures such as strong authentication, encryption, and strict access control policies, alongside our Data Retention and Disposal Policy and Vulnerability and Patch Management Policy, to ensure comprehensive access security.
- Utilize Online Resources: Leverage online platforms, industry reports, and security blogs to gather insights on the latest products and services. Significantly, 80% of CIOs have boosted their security budgets, indicating the increasing acknowledgment of the necessity for strong measures to address escalating data theft and extortion attacks. The IT department's dedication to providing customized security measures guarantees that your organization can successfully tackle its specific challenges.
- Attend Webinars and Conferences: Participate in industry events to discover new technologies and network with vendors. Interacting with specialists can offer valuable perspectives on the efficacy of various approaches, assisting you in making informed choices. Our team at JSOC IT frequently shares knowledge at such events, showcasing our comprehensive cybersecurity framework that emphasizes confidentiality, data protection, and vulnerability management.
- Read Reviews and Case Studies: Seek out customer feedback and case studies that demonstrate the effectiveness of particular approaches in real-world situations. For instance, our clients have reported substantial enhancements in their protective measures thanks to our proactive monitoring and swift [incident response strategies](https://trust.jsocit.com). A case study on our transformative cybersecurity offerings highlights how businesses can improve their compliance preparedness and overall security by collaborating with our IT team.
- Create a Shortlist: Based on your research, compile a shortlist of solutions that align with your business needs and compliance requirements. This targeted approach ensures that you focus on products that can deliver measurable outcomes, such as improved incident response times and compliance readiness. As specialists highlight, investing in advanced defensive strategies is crucial for addressing the ongoing development of automated cyber threats, and our IT team is here to assist you at every stage.

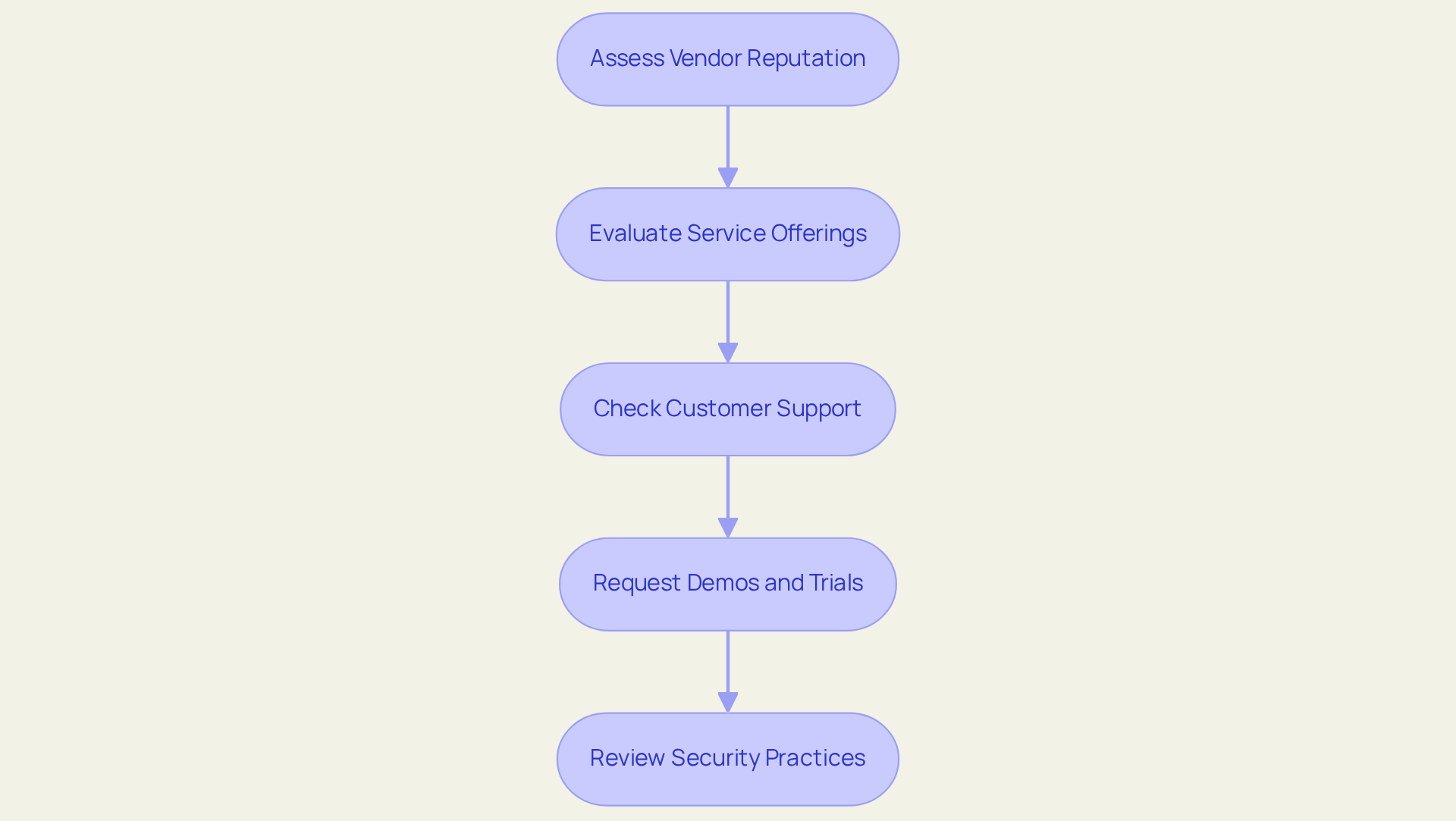
Evaluate Cybersecurity Vendors and Their Offerings
- Assess Vendor Reputation: Conduct thorough research into the vendor's reputation within the industry. Seek out awards, certifications, and partnerships that underscore their credibility. The IT team has revolutionized protection strategies for numerous clients, demonstrating unparalleled expertise in threat detection and response, which enables them to buy cybersecurity solutions for businesses and significantly bolsters their credibility in the cybersecurity arena.
- Evaluate Service Offerings: Scrutinize the specific services provided by each vendor. It is essential that these offerings align with your identified needs and compliance requirements. The IT department presents a comprehensive IT and security framework, allowing businesses to buy cybersecurity solutions for businesses that are designed to evolve alongside enterprise growth, ensuring that their services adapt as your requirements shift while seamlessly adhering to compliance standards.
- Check Customer Support: Delve into the level of customer support offered by the vendor. Evaluate factors such as availability, responsiveness, and the quality of technical assistance. The organization’s IT is celebrated for its that encompasses tool licensing expenses, allowing clients to buy cybersecurity solutions for businesses and focus on core activities without the persistent worry of potential threats.
- Request Demos and Trials: Proactively request product demonstrations or trial periods from vendors to assess the usability and effectiveness of their solutions within your environment. The proactive monitoring and swift response strategies employed by the IT team can be thoroughly evaluated during these trials, highlighting their commitment to client success.
- Review Security Practices: Confirm that the vendor adheres to best practices in online security, including regular updates, incident response protocols, and robust data protection measures. JSOC IT's unwavering commitment to excellence and meticulous attention to detail in their security practices make them a trusted partner for companies that need to buy cybersecurity solutions for businesses to safeguard sensitive information.
Understand Pricing and Budget for Cybersecurity Solutions
- Determine Your Budget: Establish a clear budget that allows you to buy cybersecurity solutions for businesses, reflecting your organization's financial capabilities and acknowledging the critical role of security in your operations. Typically, small organizations designate 4% to 10% of their IT budget to digital security, while small businesses might allocate 10-20% of their security budget to staffing. Medium-sized businesses may invest 10-30% in Managed Security Service Providers (MSSPs).
- Understand Pricing Models: Familiarize yourself with various , including subscription-based, one-time fees, and usage-based pricing. The notable shift towards subscription models often provides flexibility and scalability. For instance, large enterprises may invest 30-50% of their budgets in salaries, training, and management of protection teams, while also allocating 40-60% of their defensive budget to technology, which can include these models.
- Consider Total Cost of Ownership: Evaluate the total cost of ownership (TCO), encompassing not only the initial purchase price but also implementation, maintenance, and potential upgrade costs over time. Hidden costs can accumulate quickly, particularly with cloud-based services, where some companies charge extra for bandwidth usage and storage.
- Negotiate with Vendors: Engage in negotiations with vendors regarding pricing. Many are open to offering discounts or flexible payment plans to secure your business. Understanding the competitive landscape empowers you to advocate for better terms.
- Monitor Ongoing Costs: After implementation, diligently track ongoing costs to ensure they remain within budget. Consistently assessing costs associated with digital security aids in pinpointing areas for improvement and guarantees that when you buy cybersecurity solutions for businesses, your investment aligns with your organization's protection requirements. Significantly, 51% of security professionals believe their budgets are underfunded, highlighting the importance of careful budgeting. Furthermore, 66% of security professionals indicate their role is more stressful, emphasizing the difficulties encountered in managing security budgets.

Plan for Implementation and Ongoing Support
- Develop an Implementation Plan: Formulate a comprehensive plan that delineates the steps for deploying selected security solutions, complete with timelines and assigned responsibilities. This plan must also integrate training schedules for staff, ensuring they are adequately prepared to utilize the new systems effectively.
- Train Staff: Employee training is critical in safeguarding cybersecurity. Training programs should emphasize the , secure password practices, and adherence to protocols during a data breach. For instance, tailored training can substantially diminish the risk of succumbing to cyber threats, given that human error accounts for 82% of data breaches. Regular training sessions empower employees to serve as the primary line of defense against cyber threats, thereby enhancing the organization's overall protective posture.
- Establish Support Channels: Implement robust channels for ongoing support, including vendor assistance, internal IT resources, and user feedback mechanisms. This framework guarantees that employees have access to help when necessary, cultivating a culture of security awareness and responsiveness.
- Monitor Performance: Following implementation, it is imperative to continuously evaluate the effectiveness of security measures. This encompasses tracking incident response times and assessing the efficacy of training programs. For example, organizations that conduct simulated phishing exercises can evaluate employee readiness and modify training as needed to enhance outcomes.
- Review and Adjust: Regularly evaluate the effectiveness of cybersecurity solutions and training initiatives. As cyber threats evolve, so too must the strategies employed to counteract them. Adjustments based on performance metrics and emerging threats will ensure that the organization remains resilient against potential breaches.

Conclusion
Understanding the intricate process of purchasing cybersecurity solutions is essential for any business aiming to safeguard its digital assets. By methodically assessing cybersecurity needs, researching available solutions, evaluating vendors, understanding pricing, and planning for implementation, organizations can establish a robust security posture that effectively mitigates risks associated with cyber threats.
This article outlines a clear five-step approach:
- Identification of critical assets
- Thorough risk assessments
- Engaging stakeholders to ensure diverse perspectives shape the security strategy
- Compliance reviews to guide protective measures
- Researching various cybersecurity solutions and evaluating vendor offerings
By understanding pricing models, decision-makers are empowered to make informed choices that align with their business needs. Furthermore, planning for implementation and ongoing support is vital for sustaining a resilient cybersecurity framework.
Ultimately, investing in cybersecurity transcends mere compliance or protection; it fosters a culture of security awareness and preparedness within the organization. By prioritizing cybersecurity, businesses not only protect their assets but also enhance their reputation and trust with clients. As cyber threats continue to evolve, staying proactive in cybersecurity measures becomes indispensable for long-term success.
Frequently Asked Questions
What are the first steps to assess my business's cybersecurity needs?
Begin by identifying and cataloging all critical assets, including sensitive data, applications, and infrastructure. Recognizing what needs safeguarding is essential to prevent severe repercussions from security breaches.
Why is conducting a risk assessment important?
Conducting a risk assessment helps evaluate the likelihood of cyber attacks and the potential consequences of breaches for each identified asset. Organizations that overlook vulnerabilities may face operational disruptions and regulatory penalties.
How can I engage stakeholders in the cybersecurity assessment process?
Involve key stakeholders from various departments to gather insights on their specific security concerns and requirements. This collaborative approach ensures a comprehensive understanding of the organization's needs.
What compliance requirements should I review for my business?
Identify any industry-specific regulations your business must adhere to, such as HIPAA for healthcare or PCI DSS for financial services. Understanding these regulations will guide your protective strategy and help mitigate legal risks.
Why is it important to document my findings during the cybersecurity assessment?
Documenting your findings creates a detailed report that serves as a reference throughout the purchasing process. It helps track progress and ensures that all identified risks and compliance needs are addressed.
What types of cybersecurity solutions should I research?
Familiarize yourself with various protective solutions, including firewalls, intrusion detection systems, endpoint protection, and managed defense services, as each plays a crucial role in safeguarding your digital environment.
How can online resources assist in my research for cybersecurity solutions?
Utilize online platforms, industry reports, and security blogs to gather insights on the latest products and services. This information can help you understand the necessity for strong security measures and budget allocations.
What benefits can I gain from attending webinars and conferences?
Participating in industry events allows you to discover new technologies and network with vendors, gaining valuable perspectives on the efficacy of various approaches to cybersecurity.
How can I evaluate the effectiveness of specific cybersecurity solutions?
Seek customer feedback and case studies that demonstrate the effectiveness of particular approaches in real-world situations. This can provide insights into how solutions have improved security measures for other businesses.
What should I do after researching cybersecurity solutions?
Create a shortlist of solutions that align with your business needs and compliance requirements. This targeted approach ensures you focus on products that can deliver measurable outcomes, such as improved incident response times.