Overview
The article articulates essential strategies for data protection solutions within enterprises, underscoring the critical role of:
- Encryption
- Access controls
- Data loss prevention
- Robust backup systems
It elaborates on how these strategies effectively mitigate risks linked to cyber threats and ensure regulatory compliance, thereby fortifying overall organizational security and resilience.
Introduction
In an era marked by escalating data breaches and cyber threats, enterprises are increasingly compelled to prioritize the protection of their sensitive information. With a multitude of data protection solutions at their disposal, organizations face the critical challenge of identifying the most effective strategies to safeguard their assets. This article explores key data protection strategies that not only bolster security but also ensure compliance with ever-evolving regulations. As businesses navigate this intricate landscape, the pressing question emerges: how can they effectively balance robust protection with the imperative for operational efficiency and regulatory adherence?
Understanding Data Protection Solutions for Enterprises
For safeguarding sensitive information against unauthorized intrusion, breaches, and loss, data protection solutions for enterprises are indispensable. Key strategies encompass:
- Encryption
- Access controls
- Loss prevention (DLP)
- Robust backup and recovery systems
As cyber threats become increasingly sophisticated, organizations must adopt a comprehensive strategy that includes data protection solutions for enterprises within their overall protective framework.
Encryption plays a vital role in ensuring that sensitive information remains confidential, even if intercepted. In 2025, the impact of encryption on business protection is underscored by the fact that organizations prioritizing confidentiality and integrity are better positioned to manage regulatory obligations and mitigate risks associated with breaches. For instance, firms employing advanced encryption techniques have reported significant reductions in the likelihood of information exfiltration and unauthorized access.
Control measures further enhance security by specifying who can access certain information and under what circumstances. The implementation of and role-based permission control guarantees that only authorized personnel can interact with sensitive data, thereby reducing the risk of insider threats and external breaches. Organizations that have enforced stringent access controls have witnessed a marked decline in incidents stemming from human error.
Cybersecurity experts emphasize the importance of integrating data protection solutions for enterprises into a cohesive protective stance. An anticipatory approach to safeguarding information—one that includes continuous monitoring and regular updates to protective measures—can substantially bolster an organization's resilience against evolving cyber threats. By understanding and applying effective protection solutions, enterprises can make informed decisions that enhance their security investments and strategies, ultimately cultivating a safer digital environment.

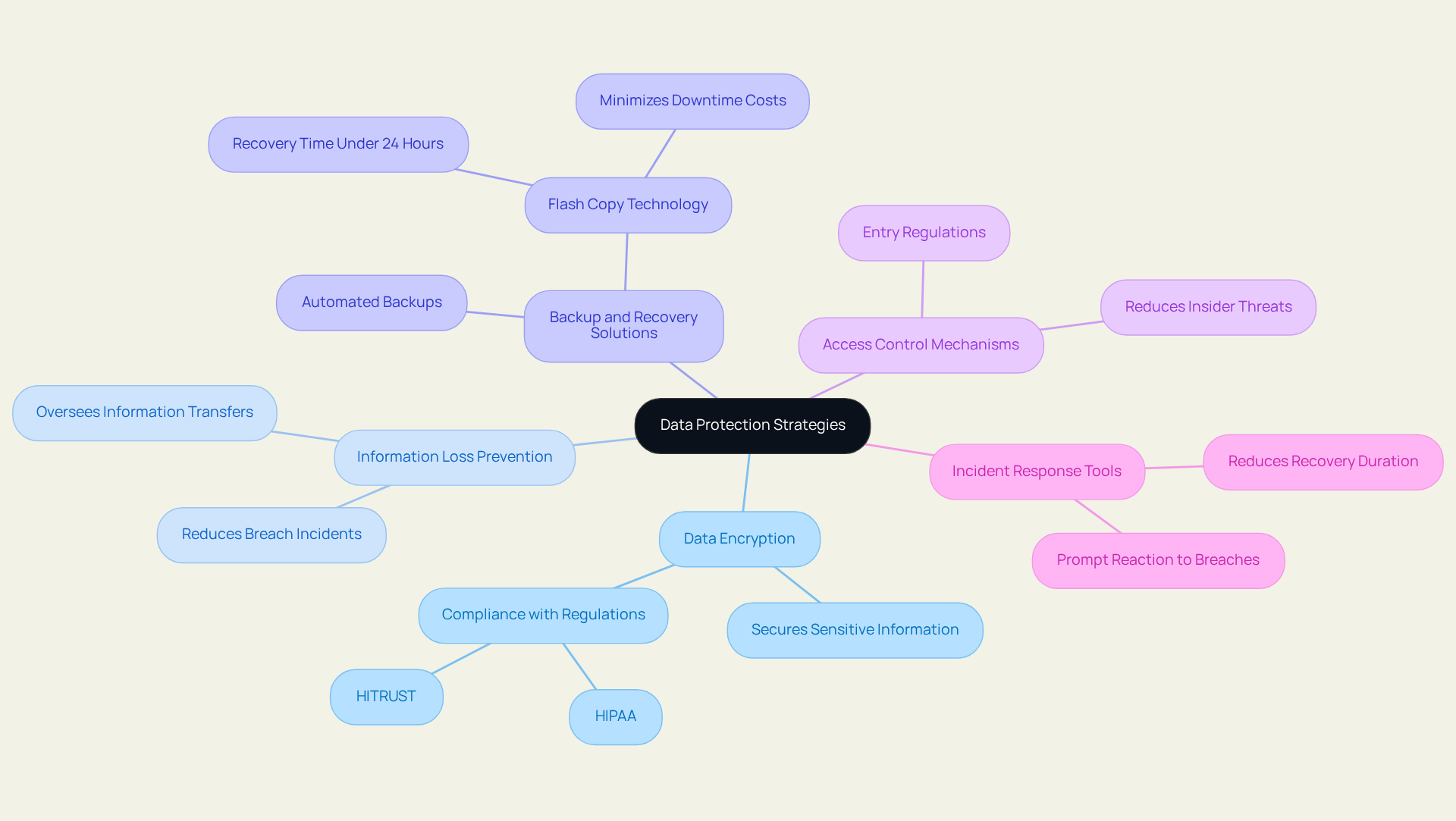
Comparing Key Data Protection Strategies and Tools
In the landscape of data protection strategies, several key tools stand out as essential components for enterprises, particularly those served by JSOC IT:
- Data Encryption: This critical tool secures sensitive information by converting it into a coded format, rendering it unreadable without the appropriate decryption key. It is essential for safeguarding information both at rest and in transit, ensuring adherence to regulations such as HIPAA and HITRUST, which are critical for industries like healthcare and finance.
- Information Loss Prevention (ILP): ILP solutions serve a crucial function in overseeing and regulating information transfers, stopping unauthorized sharing or loss of sensitive details. These tools are especially crucial for organizations striving to fulfill strict compliance standards, with for enterprises noted to decrease breach incidents considerably. JSOC IT offers customized data protection solutions for enterprises that adapt to changing threats, ensuring strong protection for sensitive information.
- Backup and Recovery Solutions: Strong backup and recovery tools are vital for ensuring information can be restored in the event of a breach or loss. Effective strategies include regular automated backups and off-site storage, which can reduce risks related to information loss. For instance, modern solutions like Flash Copy can achieve recovery times of under 24 hours, compared to traditional methods that may take over 72 hours. JSOC IT's data protection solutions for enterprises are specifically designed to minimize downtime, which is critical given that downtime costs businesses an average of $5,600 per minute.
- Access Control Mechanisms: Establishing stringent entry regulations is vital for guaranteeing that only permitted individuals can reach sensitive information. This decreases the risk of insider threats and improves overall data protection. Organizations that emphasize control over entry often observe a significant enhancement in their security stance, which is crucial for upholding compliance in regulated sectors by utilizing data protection solutions for enterprises. JSOC IT provides extensive data protection solutions for enterprises that are customized to meet the unique requirements of each entity.
- Incident Response Tools: These tools allow companies to react promptly to breaches, reducing harm and ensuring adherence to reporting obligations. A clearly outlined incident response strategy can greatly decrease recovery duration and expenses linked to breaches. JSOC IT's incident response services are intended to assist entities in managing the intricacies of breaches effectively.
Each of these strategies presents unique strengths and weaknesses, and the selection of data protection solutions for enterprises should align with the specific needs and regulatory environment of the enterprise. By embracing a thorough strategy that incorporates these elements, entities can improve their information safeguarding initiatives and manage the intricacies of compliance in 2025.
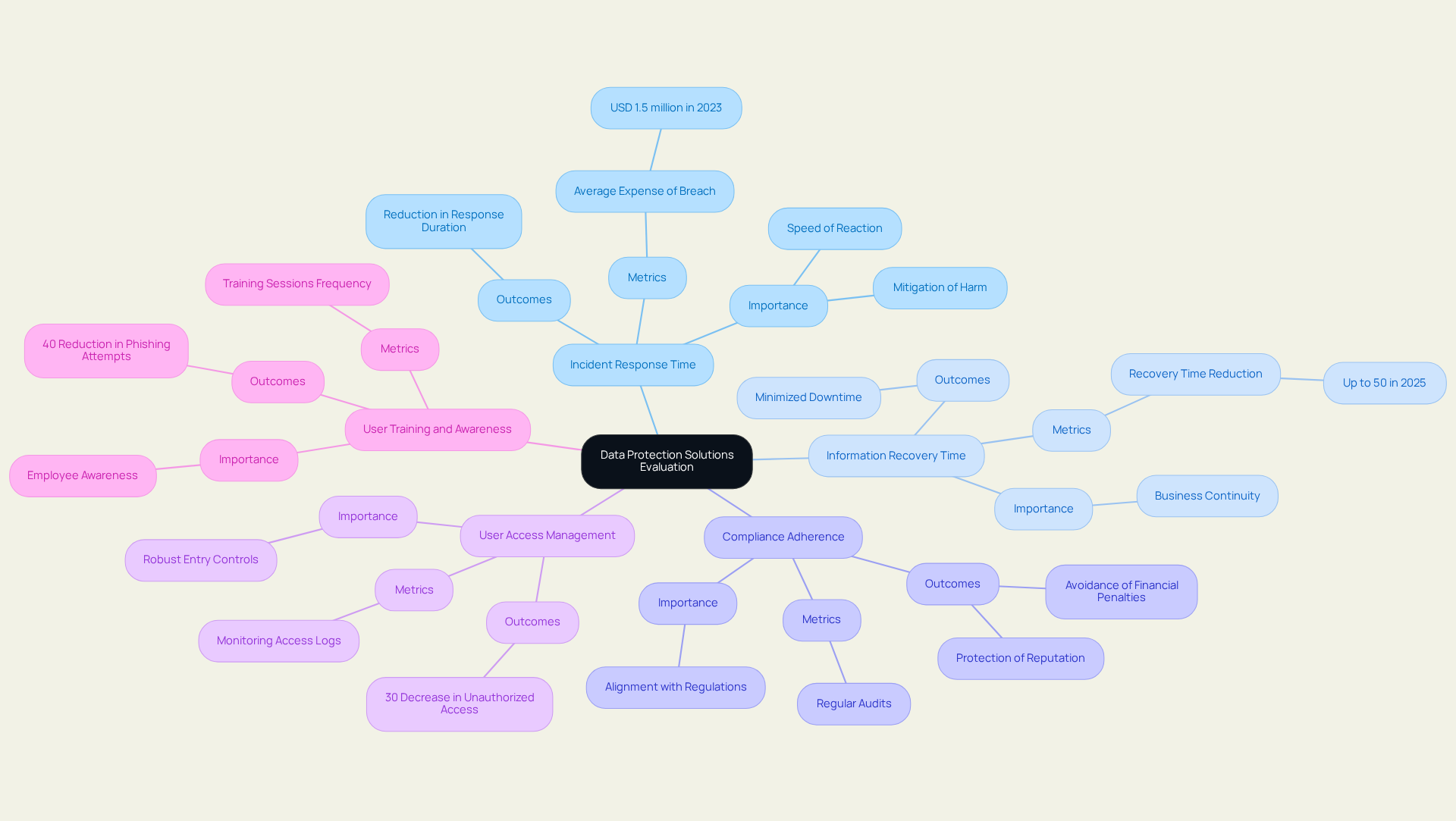
Evaluating the Effectiveness of Data Protection Solutions
To effectively evaluate data protection solutions, organizations must concentrate on several key performance indicators (KPIs):
- Incident Response Time: The speed at which an organization reacts to a breach of information is paramount. Approaches that reduce response times can significantly mitigate harm. Research indicates that a decrease in incident response duration can lead to a reduction in the average expense of a breach, which exceeded USD 1.5 million in 2023.
- Information Recovery Time: This metric assesses how swiftly information can be restored after a loss. Solutions that facilitate rapid recovery are essential for maintaining business continuity. In 2025, companies utilizing advanced information recovery solutions reported recovery times decreased by up to 50%, enabling them to resume operations quickly and minimize downtime.
- Compliance Adherence: Organizations must ensure that their information protection strategies align with relevant regulations. Regular audits and assessments are crucial for gauging compliance levels, as non-compliance can result in significant financial penalties and reputational damage.
- User Access Management: Effective solutions should incorporate robust entry controls, ensuring that only authorized personnel can access sensitive information. Monitoring access logs is vital for detecting potential breaches, with entities that proactively manage access reporting a 30% decrease in unauthorized access occurrences.
- : The effectiveness of information protection solutions is heavily influenced by employee awareness and training. Frequent training sessions can enhance the overall defensive posture of the organization, with firms emphasizing staff training experiencing a 40% reduction in successful phishing attempts.
By systematically evaluating these factors, organizations can assess the effectiveness of their information protection solutions and make informed adjustments as necessary, ultimately fortifying their cybersecurity framework.
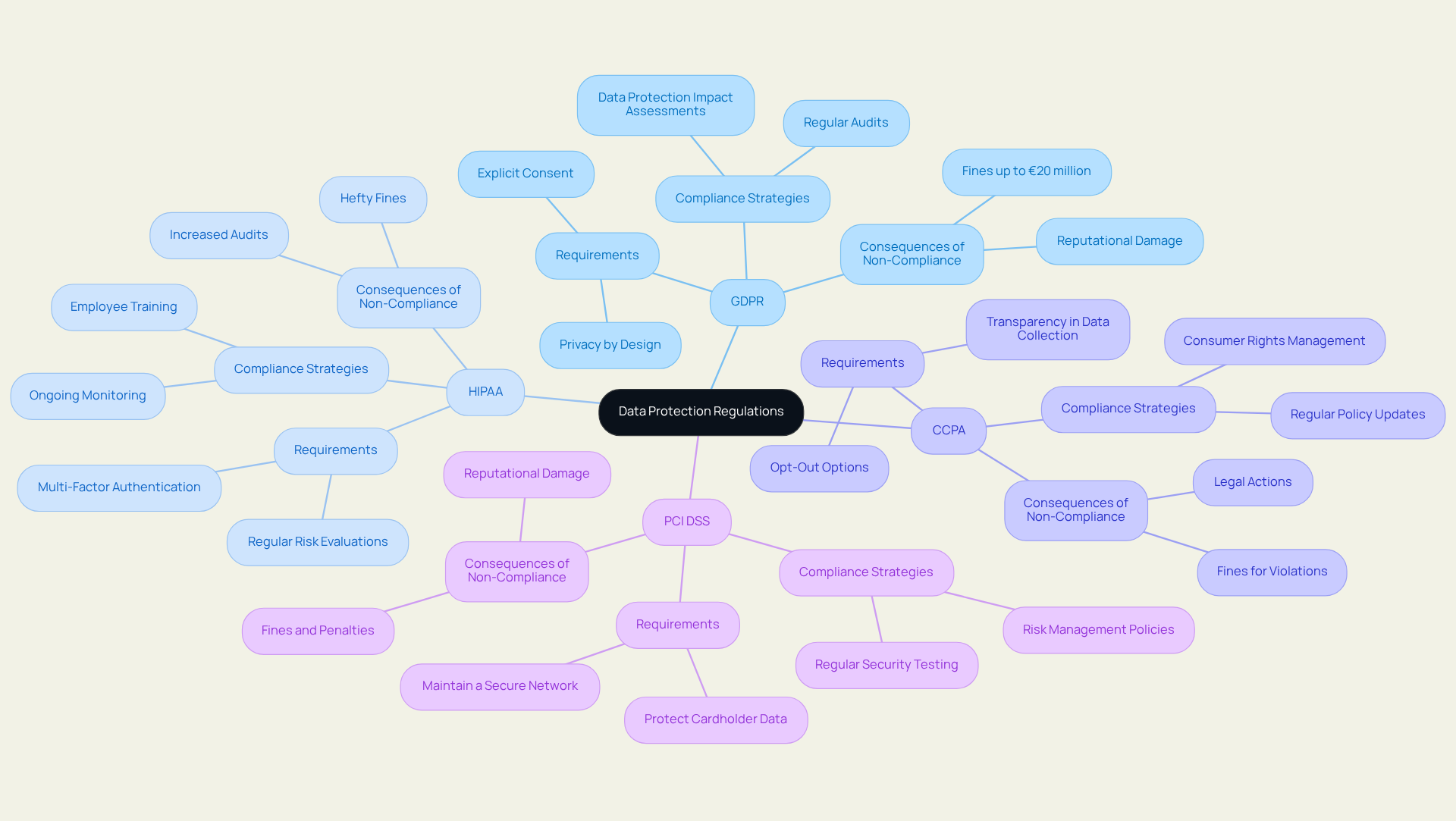
Navigating Compliance and Regulatory Frameworks in Data Protection
Adherence to privacy protection regulations is vital for any organization's information security strategy. Key regulations include:
- General Data Protection Regulation (GDPR): This EU regulation mandates strict guidelines for information handling, requiring explicit consent from individuals before processing their information. With for violations, entities must prioritize compliance to avoid substantial penalties. JSOC IT's customized consulting services can assist entities in navigating GDPR requirements effectively, ensuring strong data protection strategies are in place.
- Health Insurance Portability and Accountability Act (HIPAA): In the healthcare sector, HIPAA establishes standards for protecting sensitive patient information. Organizations must adopt specific protective measures, such as multi-factor authentication and regular risk evaluations, to safeguard electronic protected health information (ePHI). The anticipated updates to HIPAA in 2025 will further enhance these requirements, emphasizing the need for proactive compliance strategies. JSOC IT's managed security services offer ongoing monitoring and expert advice, allowing entities to proactively address these changing compliance requirements.
- California Consumer Privacy Act (CCPA): This state legislation strengthens privacy rights for California residents, requiring businesses to reveal information collection practices and permitting consumers to opt-out of selling personal information. As enforcement escalates, organizations must guarantee transparency in their information handling practices to prevent fines. JSOC IT's comprehensive information protection services, including encryption and strict access controls, enhance customer trust and ensure compliance with CCPA.
- Payment Card Industry Data Protection Standard (PCI DSS): Organizations managing credit card information must adhere to PCI DSS, which specifies protective measures for cardholder information. Non-compliance can lead to hefty fines and reputational damage. JSOC IT's risk evaluation and management policies are crafted to assist businesses in applying essential protective measures to safeguard sensitive payment information.
Navigating these regulations requires a comprehensive understanding of their implications for information protection strategies. Organizations must regularly review and update their policies to ensure compliance, which involves conducting thorough risk assessments, implementing necessary security measures, and providing employee training on compliance requirements. Real-world examples, such as the €290 million fine imposed on a ride-sharing app for improper data transfers, highlight the critical importance of adhering to these regulations to mitigate risks and protect sensitive information. With JSOC IT's expertise, organizations can enhance their compliance frameworks and achieve a secure, compliant operational environment.
Conclusion
Data protection solutions are critical for enterprises aiming to secure sensitive information amid rising cyber threats. By adopting a comprehensive strategy that encompasses:
- Encryption
- Access controls
- Data loss prevention
- Robust backup systems
organizations can markedly enhance their security posture and mitigate risks associated with data breaches.
This article underscores the essential components of effective data protection, highlighting the significance of:
- Encryption for maintaining confidentiality
- Access control to thwart unauthorized access
- The necessity of incident response tools for efficient breach management
Furthermore, it stresses the imperative for compliance with regulations such as GDPR, HIPAA, and CCPA, which impose stringent requirements for handling sensitive data. Organizations that prioritize these strategies not only protect their information but also fortify their compliance frameworks, ultimately nurturing trust and resilience in a complex digital landscape.
In an era where data breaches can yield catastrophic consequences, enterprises must proactively evaluate and enhance their data protection solutions. By concentrating on key performance indicators and adapting to regulatory shifts, organizations can cultivate a robust security environment that not only safeguards their assets but also positions them advantageously in a competitive market. The importance of investing in effective data protection strategies cannot be overstated; it is an indispensable element of any enterprise's long-term success and sustainability.
Frequently Asked Questions
What are data protection solutions for enterprises?
Data protection solutions for enterprises are strategies and technologies designed to safeguard sensitive information against unauthorized access, breaches, and loss.
What key strategies are included in data protection solutions?
Key strategies include encryption, access controls, loss prevention (DLP), and robust backup and recovery systems.
Why is encryption important for data protection?
Encryption is vital for ensuring that sensitive information remains confidential, even if intercepted. It helps organizations manage regulatory obligations and reduce risks associated with breaches.
How does encryption impact business protection?
Organizations prioritizing confidentiality and integrity through advanced encryption techniques have reported significant reductions in the likelihood of information exfiltration and unauthorized access.
What role do access controls play in data protection?
Access controls specify who can access certain information and under what circumstances, reducing the risk of insider threats and external breaches.
What measures can enhance access control security?
Implementing multi-factor authentication and role-based permission control guarantees that only authorized personnel can interact with sensitive data.
How do organizations benefit from stringent access controls?
Organizations that enforce stringent access controls have witnessed a marked decline in incidents stemming from human error.
What is the importance of integrating data protection solutions?
Integrating data protection solutions into a cohesive protective stance helps organizations adopt an anticipatory approach to safeguarding information, enhancing resilience against evolving cyber threats.
How can organizations strengthen their data protection strategies?
Organizations can strengthen their strategies by incorporating continuous monitoring and regular updates to protective measures, ensuring informed decisions that enhance security investments.