Overview
The post-security model for integrated cybersecurity is not just beneficial; it is essential. This model promotes a comprehensive approach that merges IT operations with protective measures, thereby enhancing organizational resilience against cyber threats.
By fostering collaboration across departments, embedding security within operational processes, and leading to proactive threat mitigation, this model significantly reduces risks and improves compliance.
Organizations must recognize the value of integrating cybersecurity into their core operations to effectively combat the evolving landscape of cyber threats.
Introduction
The landscape of cybersecurity is evolving rapidly, necessitating a transition from traditional reactive measures to a more integrated and proactive approach. The post-security model stands as a beacon of innovation, advocating for the seamless fusion of IT operations with security protocols to effectively combat the increasingly complex cyber threats organizations face today.
However, how can businesses successfully transition to this model and ensure that their defenses are not merely reactive but embedded within their operational framework? This article explores essential strategies for implementing the post-security model, providing insights into:
- Assessing current cybersecurity postures
- Integrating security measures
- Fostering a culture of continuous improvement and awareness among staff
Define the Post-Security Model and Its Importance
The post-security model for integrated cybersecurity signifies a transformative shift, advocating for a comprehensive approach that merges IT operations with protective measures. This integration is crucial for organizations confronting the , as it dismantles departmental silos and fosters collaboration among teams. By embedding protection within IT operations, businesses can markedly bolster their resilience against breaches and vulnerabilities.
The model's importance is underscored by its capacity to foster a proactive protective stance, allowing organizations not only to react to incidents but also to foresee and mitigate potential threats effectively. This cohesive approach ensures that protection is woven into the fabric of the entity's operational framework, rather than treated as an afterthought. As a result, organizations benefit from enhanced compliance and a substantial reduction in risk.
For instance, the advent of Behavior and Culture Programs (BCPs) illustrates how integrating protection into organizational culture can lead to improved risk ownership at the individual level. Moreover, organizations that have adopted unified cybersecurity strategies report significant improvements in response times to incidents and overall confidence in their protective measures. As cybersecurity leaders shift towards a resilience-oriented mindset, the post-security model for integrated cybersecurity emerges as a crucial framework for navigating the challenges of 2025 and beyond.
Assess Your Current Cybersecurity Posture
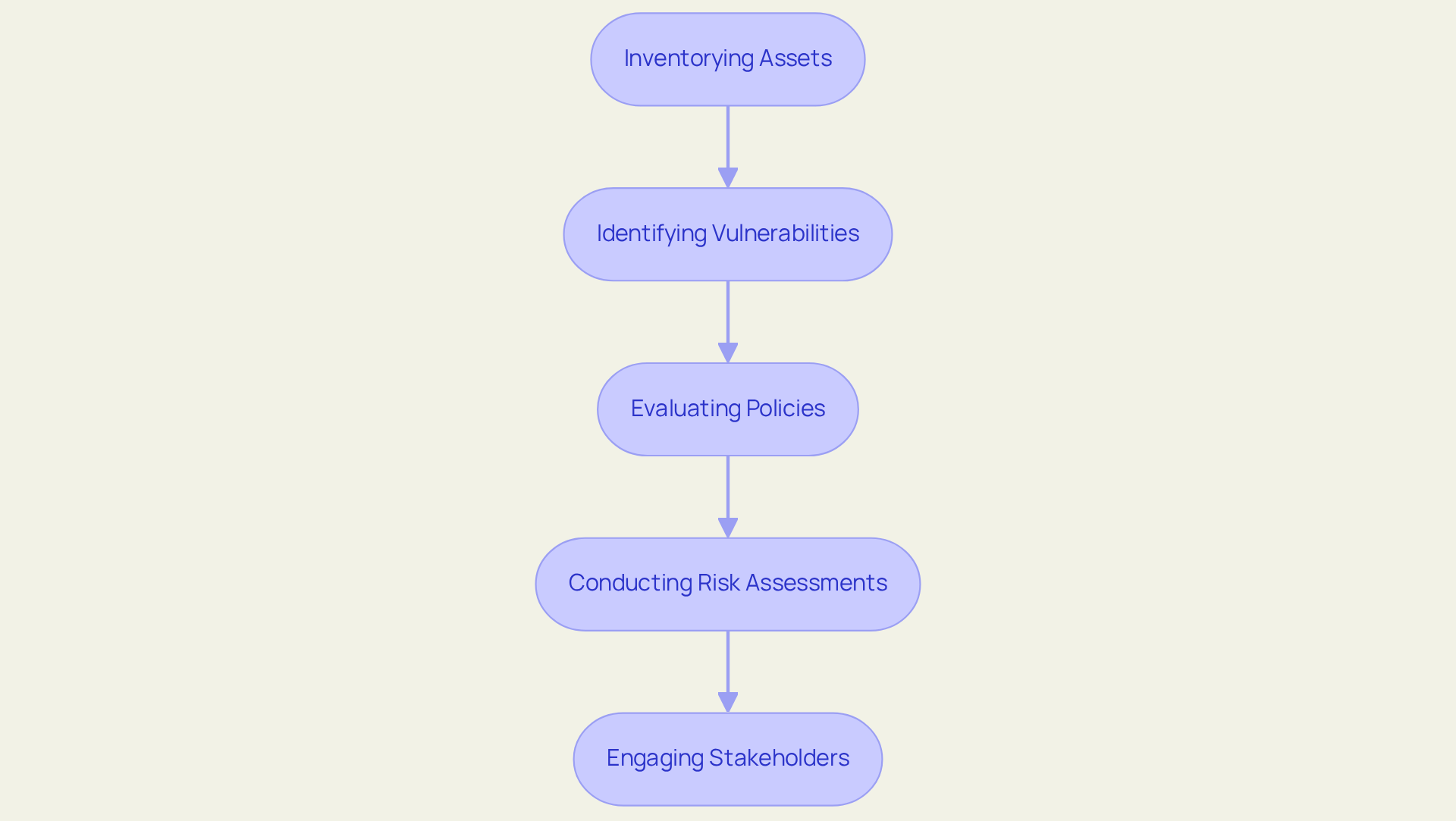
To effectively evaluate your current , initiate a comprehensive review of your existing protection measures, policies, and practices. This process encompasses the following key steps:
- Inventorying Assets: Compile a detailed list of all hardware, software, and data assets to identify what requires protection.
- Identifying Vulnerabilities: Employ advanced vulnerability scanners, such as Nessus or Qualys, to uncover weaknesses within your systems. Frequent assessments significantly reduce the likelihood of serious incidents.
- Evaluating Policies: Review current protection policies and procedures to ensure alignment with industry best practices and compliance with relevant regulations, such as GDPR and HIPAA.
- Conducting Risk Assessments: Identify potential threats and evaluate the impact of various risks on your entity. Recognizing that 71% of established entities perform comprehensive vendor risk evaluations can inform your strategy.
- Engaging Stakeholders: Involve key stakeholders from IT, compliance, and other teams to gather diverse insights on the current posture, fostering collaboration that is essential for effective risk management.
By completing this assessment, you will gain a clear understanding of your entity's strengths and areas for improvement, which is crucial for successfully implementing the Post-Security model. JSOC IT guarantees data protection through advanced protective measures, including data encryption and stringent access controls, further supporting your efforts to safeguard against evolving cyber threats.
Integrate IT Operations with Security Measures
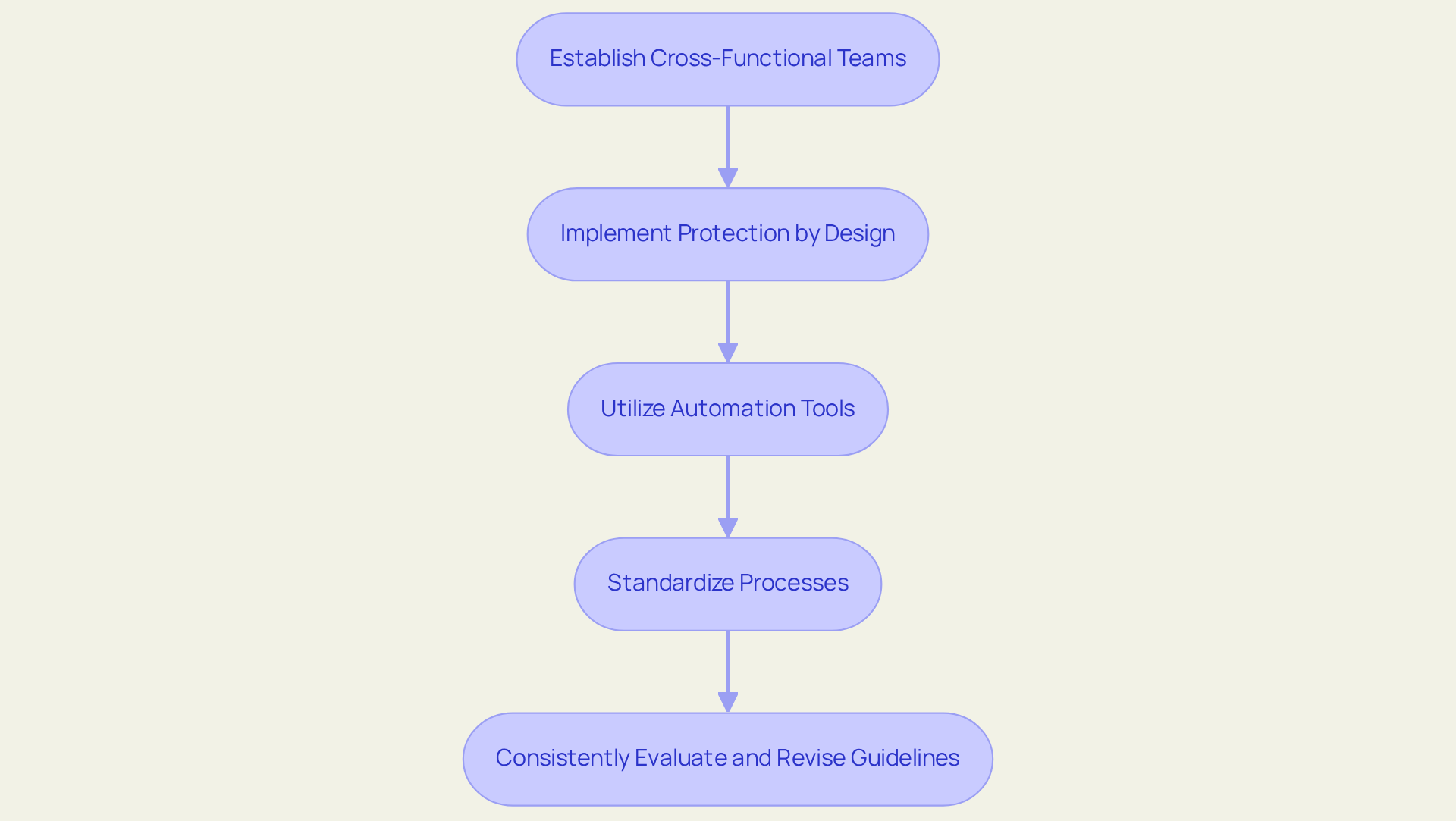
To effectively integrate IT operations with security measures, organizations must adopt several key strategies:
- Establish Cross-Functional Teams: Create teams that comprise members from both IT and safety departments. This partnership promotes communication and ensures that safety considerations are integrated into all operational processes.
- Implement Protection by Design: Integrate protective measures into the development and deployment phases of IT systems from the outset. This proactive approach minimizes vulnerabilities and enhances overall system resilience. Implementing a Secure Development Policy guarantees that safety requirements are outlined and upheld throughout the software development lifecycle.
- Utilize Automation Tools: for monitoring safety and responding to events. Automation not only enhances efficiency but also reduces the chance of human error, enabling teams to focus on more complex safety challenges.
- Standardize Processes: Develop and enforce standardized processes for incident response, change management, and system updates. A robust Change Management Policy oversees the documentation, tracking, testing, and approval of changes, ensuring that protective protocols are consistently applied and risks are effectively managed. Furthermore, a Configuration and Asset Management Policy regulates settings for new sensitive systems, thereby improving protective measures.
- Consistently Evaluate and Revise Guidelines: Continuously assess and refine protective policies to adapt to technological advancements and emerging challenges. This dynamic approach helps organizations stay ahead of potential vulnerabilities, particularly concerning the use of production data and its limitations in development and testing environments.
By integrating protection into IT operations, organizations can cultivate a robust infrastructure that exemplifies the post-security model for integrated cybersecurity, making them better prepared to confront and mitigate cyber threats. Case studies have shown that companies implementing these practices experience improved response times and heightened trust, ultimately resulting in a more secure operational environment.
Establish Continuous Monitoring and Incident Response Protocols
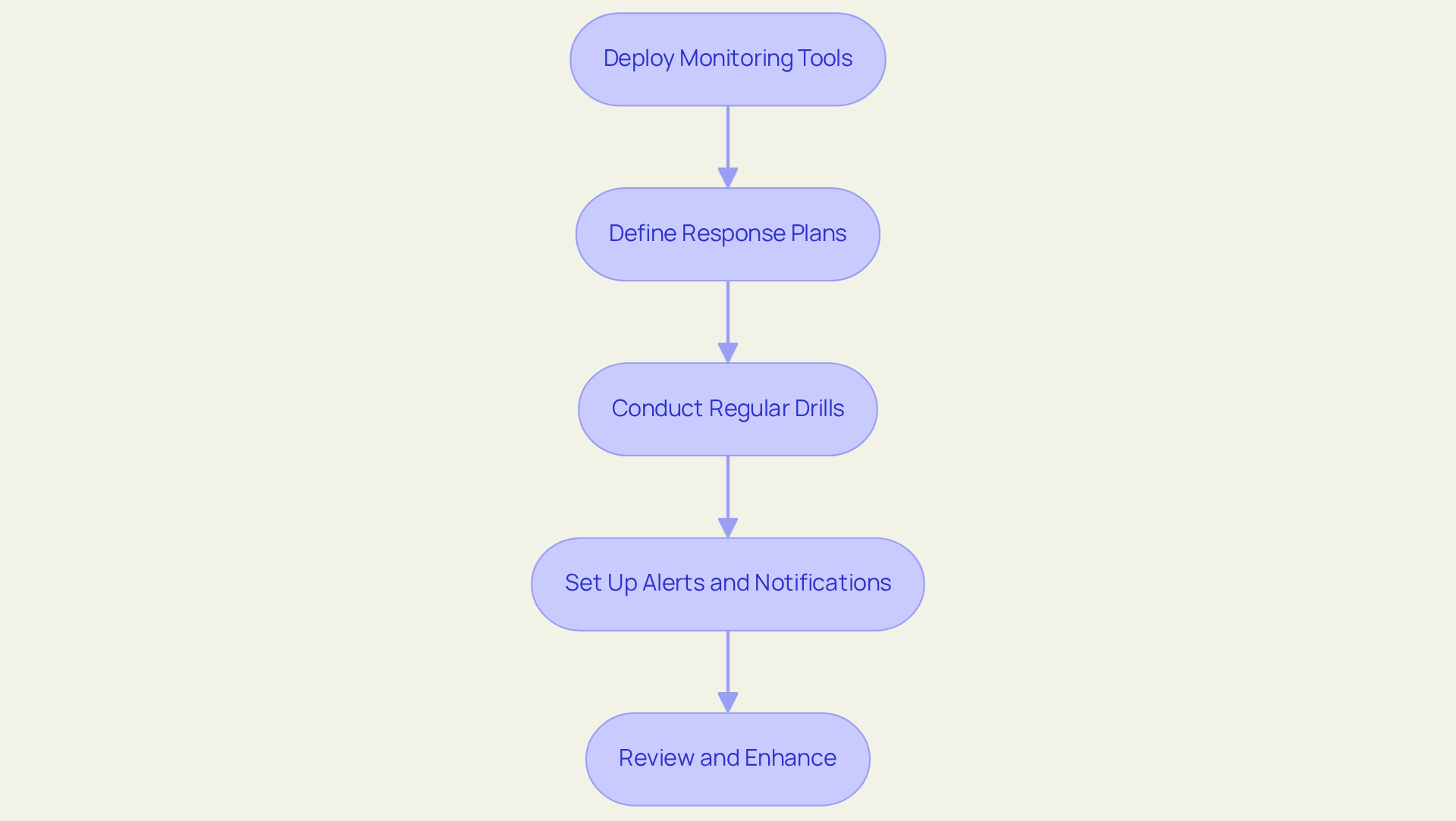
To establish robust continuous monitoring and incident response protocols, organizations must implement the following steps:
- Deploy Monitoring Tools: Organizations should utilize information and event management (SIEM) systems to collect and examine data in real-time. Efficient SIEM systems significantly enhance threat detection capabilities, with research indicating that organizations employing these tools experience a 30% quicker recognition of security events.
- Define Response Plans: It is imperative to create thorough response plans that clearly outline roles, responsibilities, and procedures tailored for various types of occurrences. A well-structured plan is essential for minimizing response times and ensuring effective communication during crises.
- Conduct Regular Drills: Organizations must engage in tabletop exercises and simulations to assess the efficiency of their response plans. Consistent training has been shown to improve response speed by as much as 40%, revealing gaps in coordination and enhancing overall readiness.
- Set Up Alerts and Notifications: Configuring alerts for suspicious activities and anomalies is crucial for facilitating the timely detection of potential threats. This proactive strategy is vital, as entities that employ real-time monitoring can reduce the average duration to identify issues from days to mere hours.
- Review and Enhance: Following each incident, conducting comprehensive post-event evaluations to analyze the response and identify areas for improvement is essential. Ongoing enhancement of event management methods is critical, as entities that frequently revise their protocols based on previous occurrences can significantly bolster their resilience against future threats.
By establishing these protocols, organizations can enhance their ability to detect, respond to, and recover from cyber incidents, which aligns with a post-security model for integrated cybersecurity and reinforces their overall security posture.
Implement Training and Awareness Programs for Staff
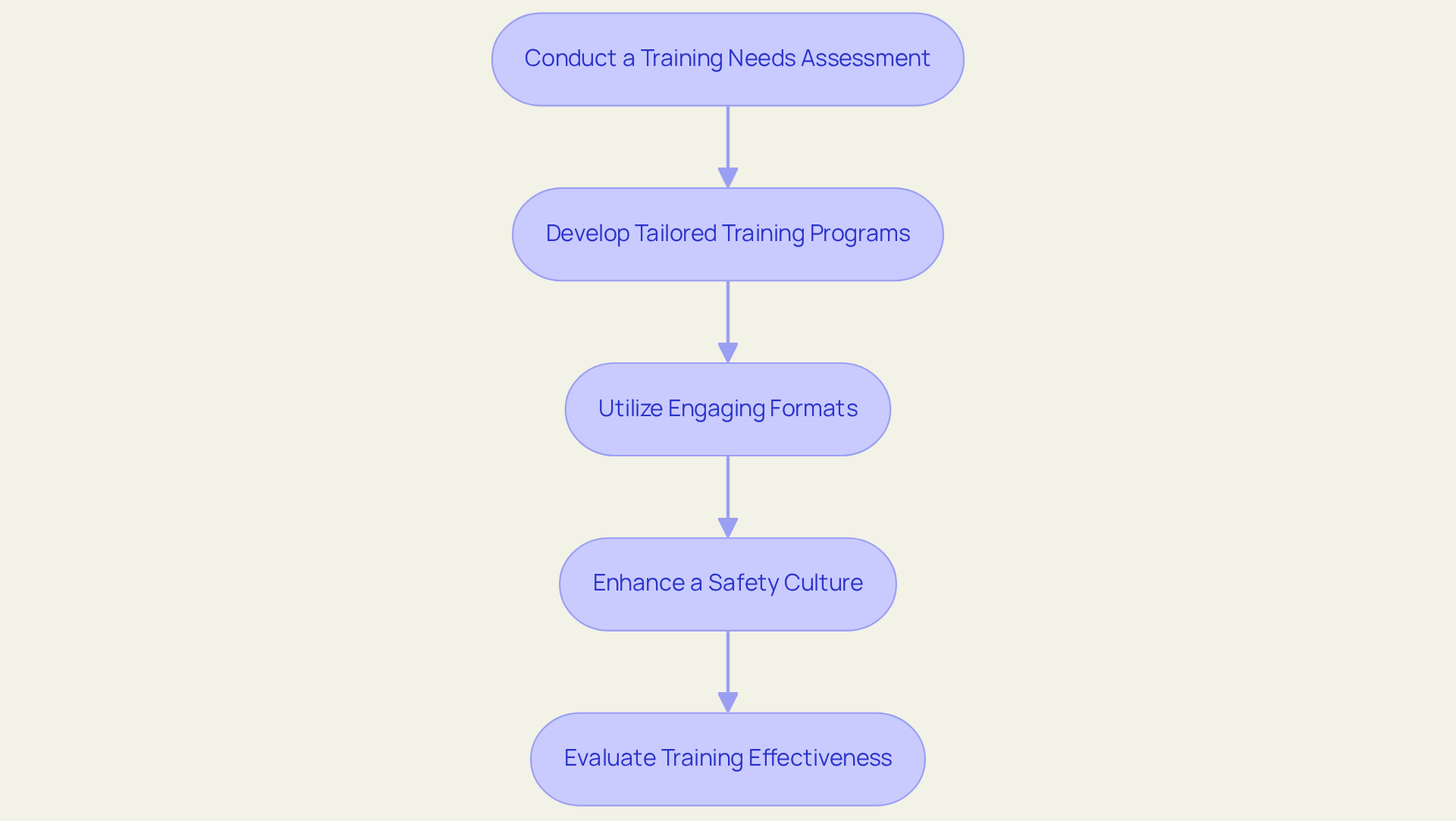
To implement effective training and awareness programs for staff, consider the following steps:
- Conduct a Training Needs Assessment: It is crucial to identify the specific training needs of various roles within the company. This approach ensures that the training is relevant and addresses the unique challenges faced by different departments. Regular updates to training content must align with current risks and regulatory changes to maintain effectiveness.
- Develop Tailored Training Programs: Create customized training modules that focus on the specific cybersecurity threats relevant to each department. This enhances the relevance and impact of the training.
- Utilize : Incorporate interactive elements such as quizzes, simulations, and real-life scenarios. Studies demonstrate that organizations utilizing captivating training formats, including gamification, experience a 30% rise in retention rates compared to conventional methods, thereby enhancing the effectiveness of learning.
- Enhance a Safety Culture: Cultivate an environment of safety by promoting open conversations about cybersecurity and acknowledging employees who exhibit positive practices. This grassroots support can significantly enhance overall security awareness within the organization.
- Evaluate Training Effectiveness: Regularly assess the effectiveness of training programs through feedback, assessments, and incident analysis. Organizations that carry out evaluations witness a 40% boost in employee performance, guaranteeing ongoing enhancement and adjustment to changing challenges. Emphasizing continuous learning and just-in-time training can further reinforce the importance of ongoing education in cybersecurity.
By investing in these comprehensive training and awareness programs, companies can significantly enhance their cybersecurity posture in alignment with a post-security model for integrated cybersecurity, empowering employees to act as the first line of defense against cyber threats. Additionally, organizations should be mindful of challenges such as resource constraints and employee resistance when implementing these programs.
Conclusion
The post-security model signifies a crucial evolution in cybersecurity, underscoring the necessity for a holistic integration of IT operations and security measures. This comprehensive approach not only bolsters an organization’s resilience against cyber threats but also cultivates collaboration across departments, ensuring that security is woven into every aspect of operations. By adopting a proactive stance towards potential risks, organizations can markedly enhance their overall security posture and compliance.
Key insights from the article underscore the importance of:
- Evaluating current cybersecurity practices
- Embedding protective measures into IT operations
- Instituting continuous monitoring and incident response protocols
Moreover, implementing tailored training and awareness programs for staff empowers employees to serve as the first line of defense against cyber threats. Each of these strategies contributes to a more robust cybersecurity framework, in alignment with the principles of the post-security model.
Given the escalating complexity of cyber risks, organizations must embrace this model as an essential strategy for success. By actively integrating security into their operations and nurturing a culture of awareness and preparedness, businesses can not only mitigate vulnerabilities but also enhance their capacity to respond to incidents effectively. The journey towards a resilient cybersecurity posture is ongoing, and organizations are urged to adopt these practices to safeguard their assets and ensure long-term success in an ever-evolving digital landscape.
Frequently Asked Questions
What is the post-security model for integrated cybersecurity?
The post-security model for integrated cybersecurity is a transformative approach that merges IT operations with protective measures, fostering collaboration among teams and dismantling departmental silos to enhance resilience against cyber risks.
Why is the post-security model important for organizations?
It is important because it allows organizations to adopt a proactive protective stance, enabling them to foresee and mitigate potential threats effectively, leading to improved compliance and a substantial reduction in risk.
How can organizations integrate protection into their culture?
Organizations can integrate protection into their culture through Behavior and Culture Programs (BCPs), which promote improved risk ownership at the individual level.
What benefits do organizations report after adopting unified cybersecurity strategies?
Organizations that adopt unified cybersecurity strategies report significant improvements in incident response times and overall confidence in their protective measures.
What are the key steps to assess your current cybersecurity posture?
The key steps include inventorying assets, identifying vulnerabilities using advanced scanners, evaluating policies for alignment with best practices, conducting risk assessments, and engaging stakeholders for diverse insights.
What tools can be used to identify vulnerabilities in systems?
Advanced vulnerability scanners such as Nessus or Qualys can be employed to uncover weaknesses within systems.
What is the significance of conducting risk assessments?
Conducting risk assessments helps identify potential threats and evaluate the impact of various risks, which is crucial for informing cybersecurity strategies.
How does JSOC IT support data protection?
JSOC IT supports data protection through advanced protective measures, including data encryption and stringent access controls, to safeguard against evolving cyber threats.